Vulnerability Remediation Process Flow Chart - What Is Vulnerability Assessment Testing Process Vapt Scan
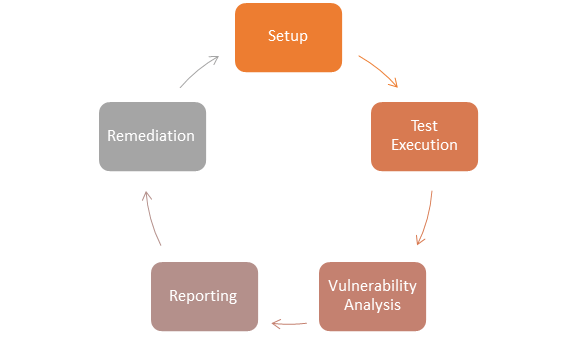
What Is Vulnerability Assessment Testing Process Vapt Scan

Creating A Remediation Operation For Truesight Server .

Vulnerability Assessment Flow Chart Adapted From The Us Doe .

Vulnerability Management Process Flow Chart Www .

Vulnerability Group And Vulnerable Item States Servicenow Docs .

Vulnerability Remediation You Only Have 4 Options Synopsys .

Risk Triage For Security Vulnerability Announcements .
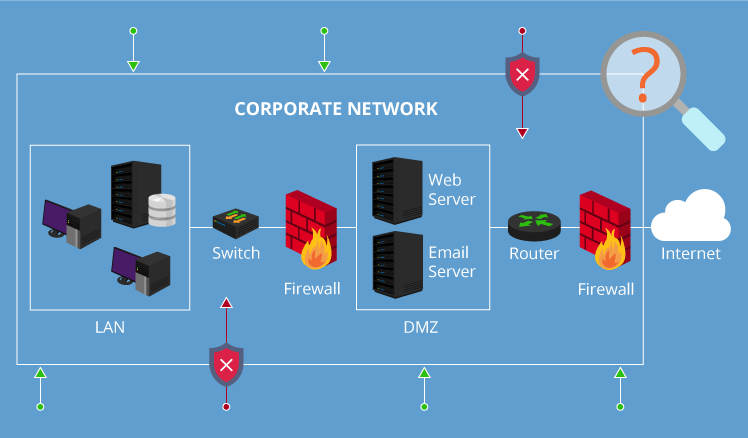
A Complete Guide To Network Vulnerability Assessment .

Vulnerability Management Qualys Inc .

Vulnerability Response Remediation Overview Servicenow Docs .
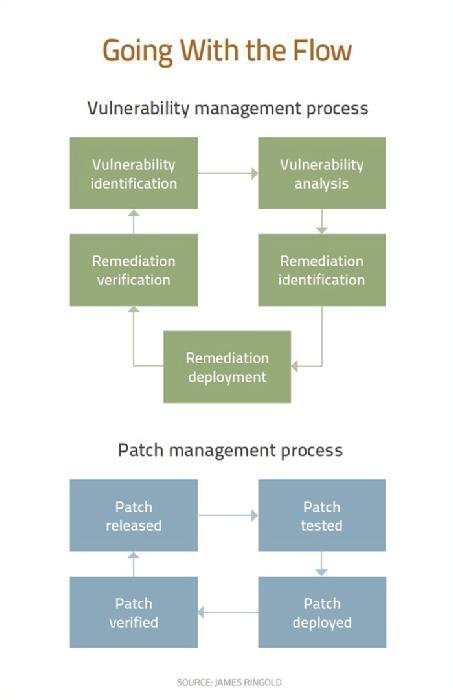
The Vulnerability Management Process After Equifax .

Cybersecurity Specialist It Security And Service Cynexlink .

Application Security Deconstructed And Demystified .
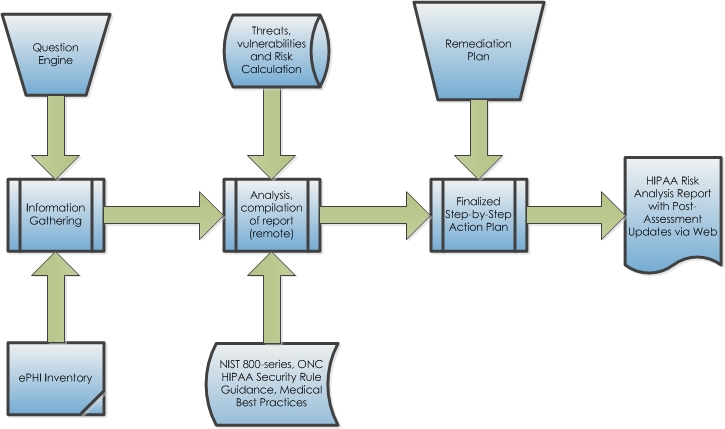
Hipaa Security Risk Analysis Data Risk Managementdata Risk .

Scan Vulnerability Workflow Servicenow Docs .
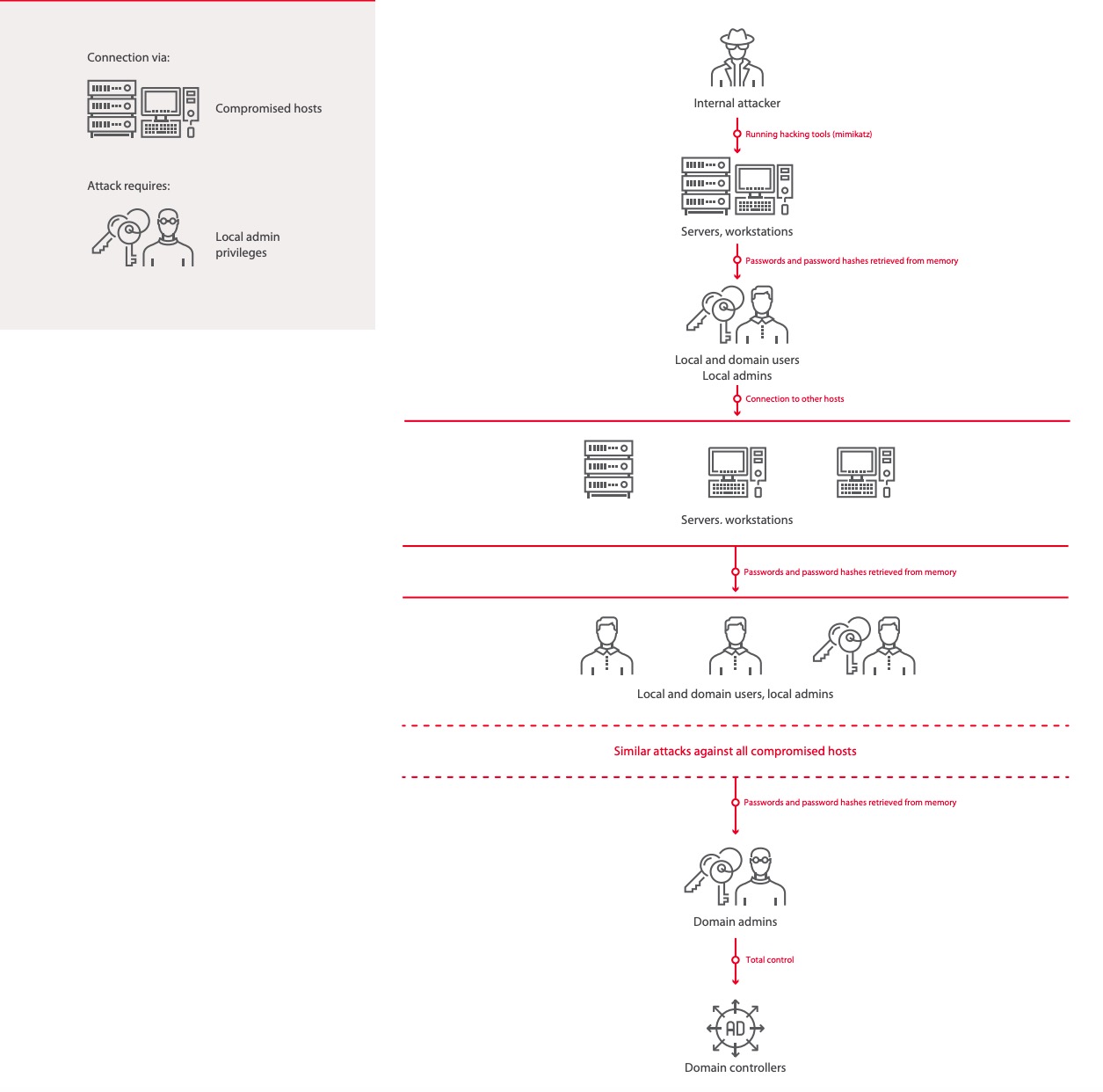
Industrial Control Systems Cyber Security Attack Vectors .

Psirt Services Framework 1 0 .
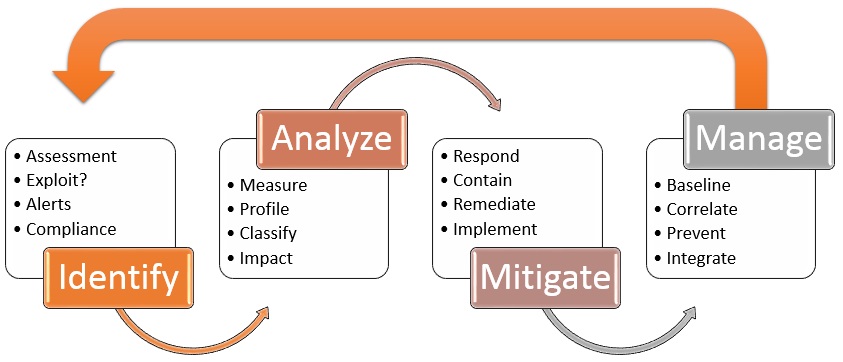
Vulnerability Nige The Security Guy .

Understanding The Vulnerability Response Application .

What Is Sast And How Does It Work Synopsys .

Vulnerability Management Policy Pdf Free Download .

Building Strong Ulnerability Management Program Being .

Prioritizing Remediation Plug Into The Firehose Of .

Software Vulnerability Management Secunia R D Patch Management .

Vulnerability Management Qualys Inc .

Cyber Risk Remediation Analysis The Mitre Corporation .
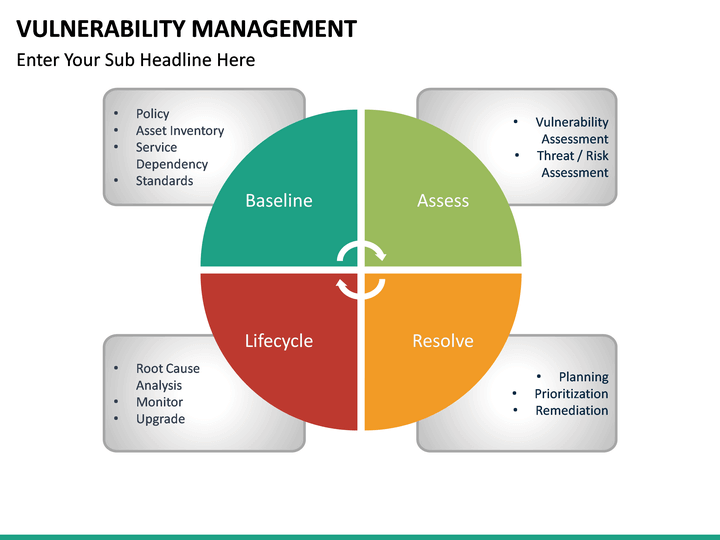
Vulnerability Management .

Application Security Deconstructed And Demystified .

I Cant Keep Up With All These Cisco Security Advisories Do .

Securosis Blog Article .
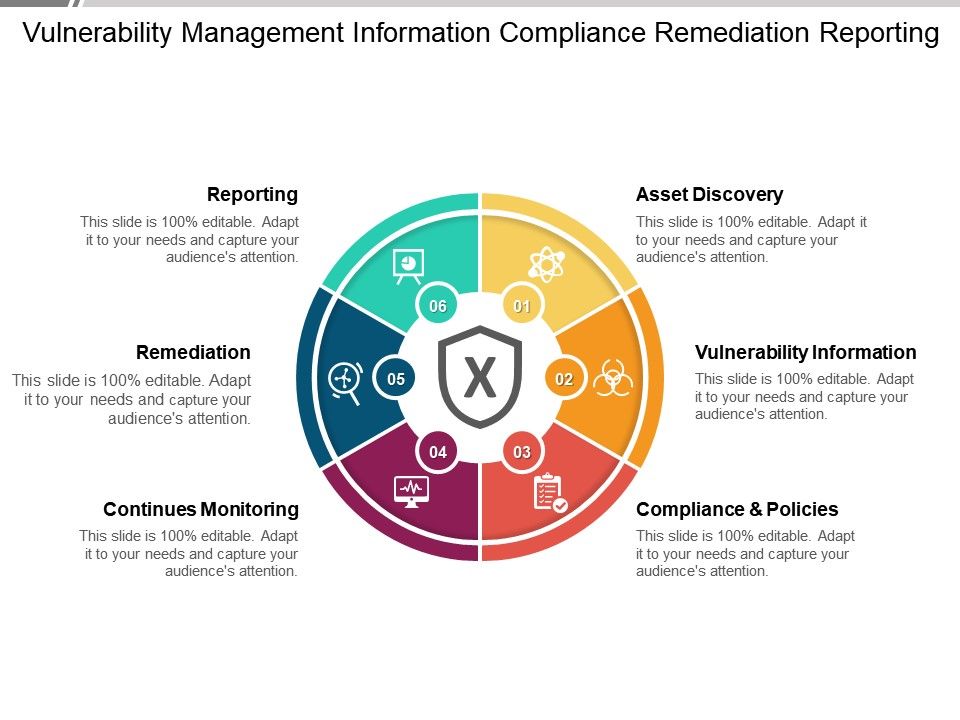
Vulnerability Management Information Compliance Remediation .

Vulnerability Management Qualys Inc .
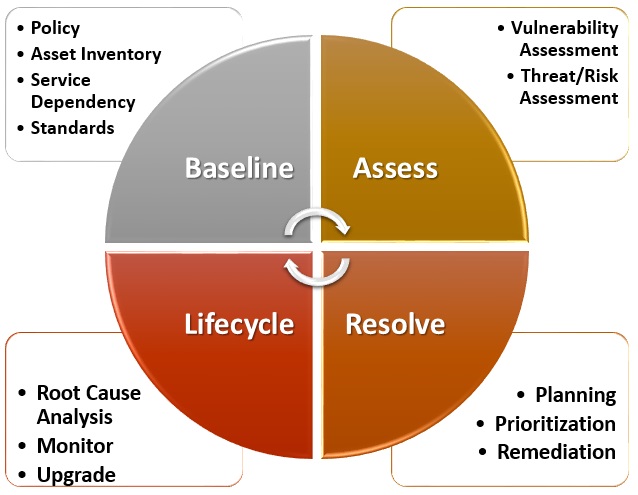
Threat And Vulnerability Management Nige The Security Guy .

Product Vision Secure Gitlab .
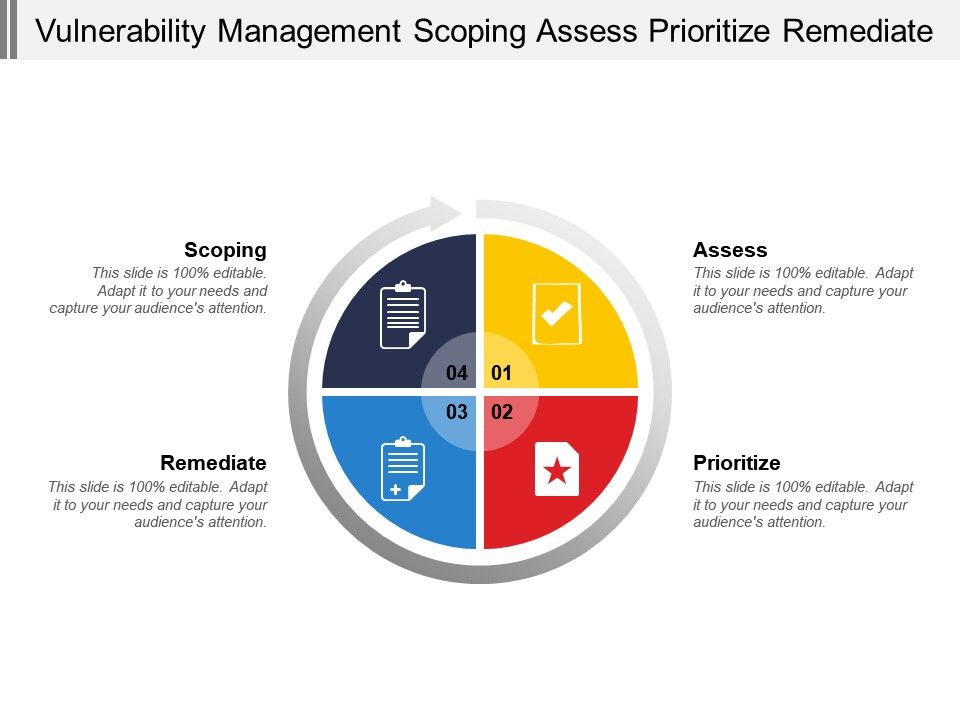
Vulnerability Management Scoping Assess Prioritize Remediate .

Understanding The Vulnerability Response Application .
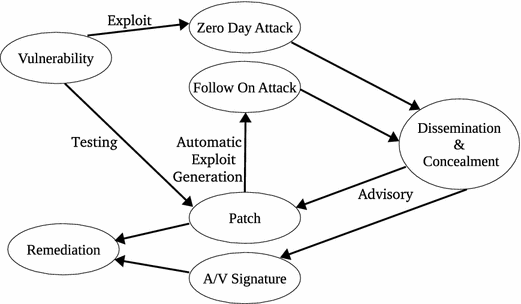
An Overview Of Vulnerability Assessment And Penetration .

Remediation Workflows .
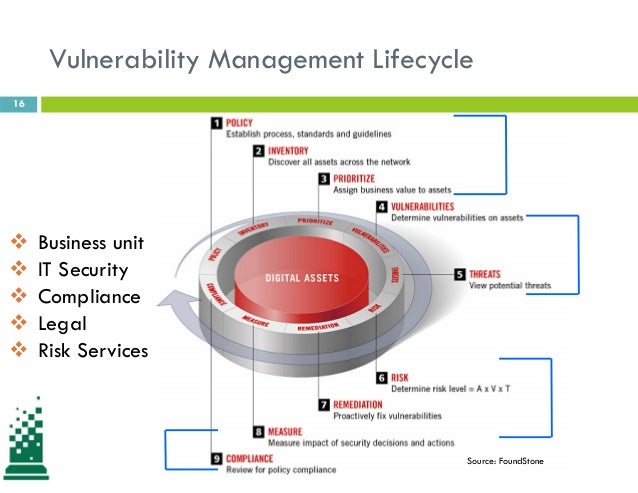
Monitoring Threats For Pci Compliance .

What Is Vulnerability Assessment Testing Process Vapt Scan .
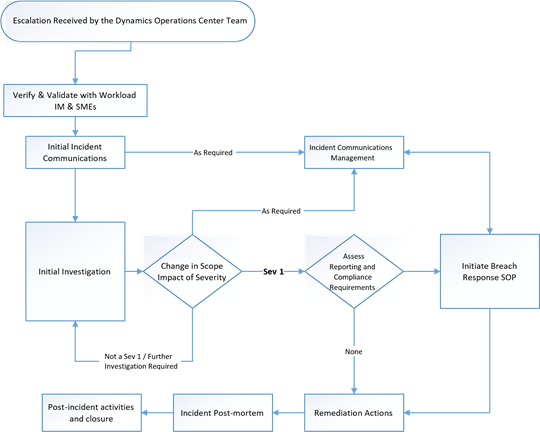
Security Incident Management In Microsoft Dynamics 365 .

Applying Ai In Application Security .
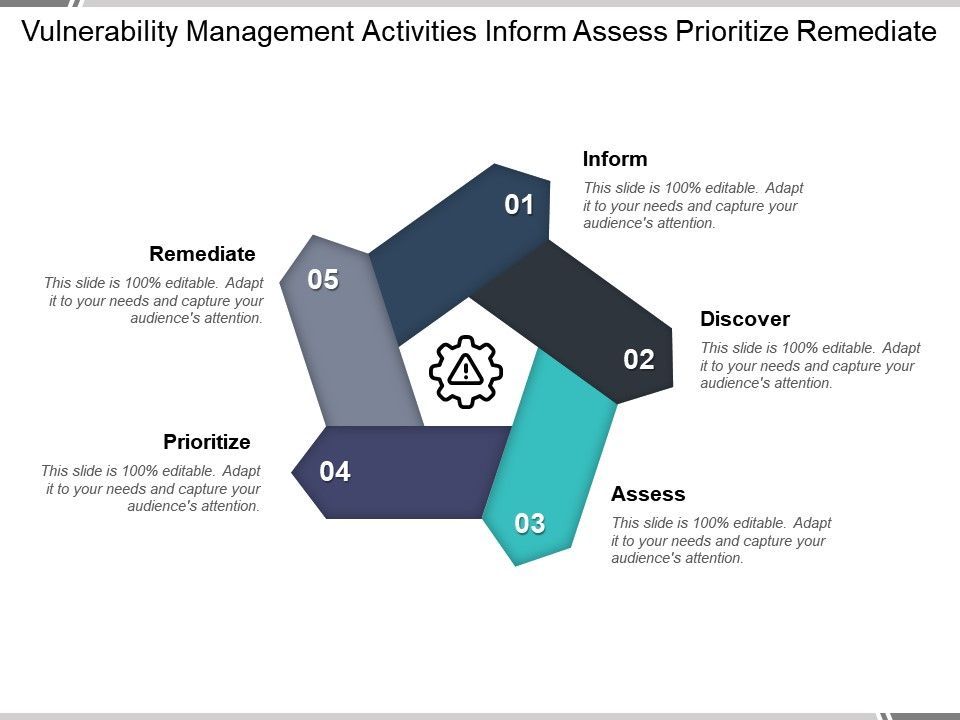
Vulnerability Management Activities Inform Assess Prioritize .

Typical Flow Chart Of The Model Development Left Flowchart .
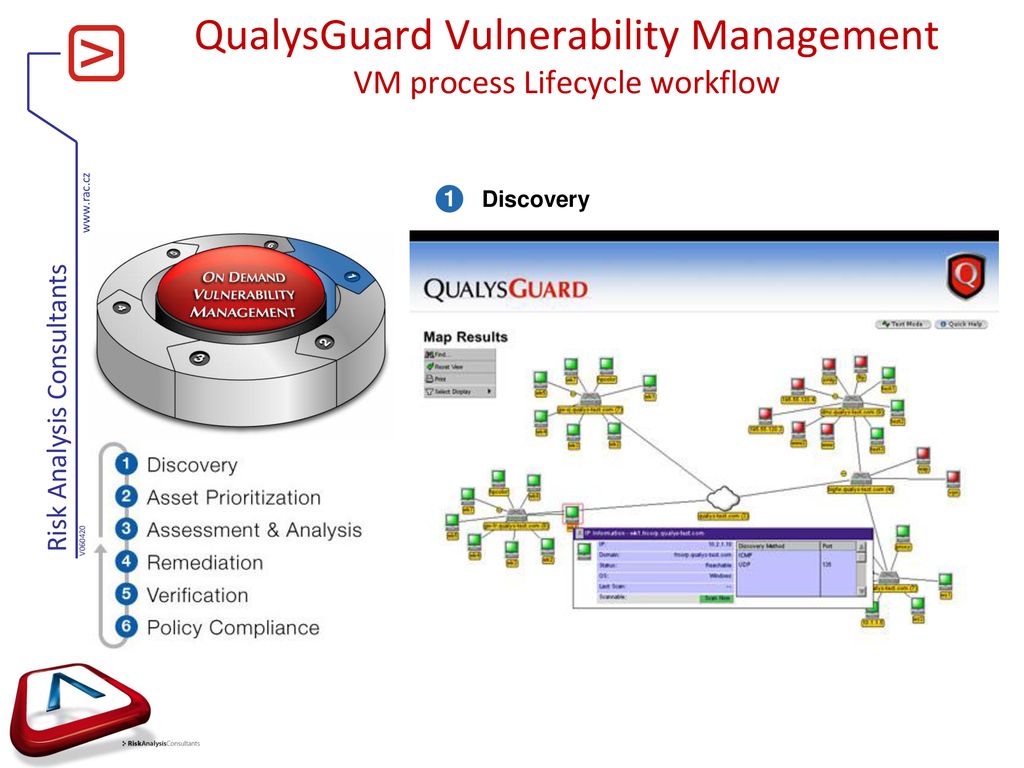
Qg Vulnerability Management Module Ppt Download .
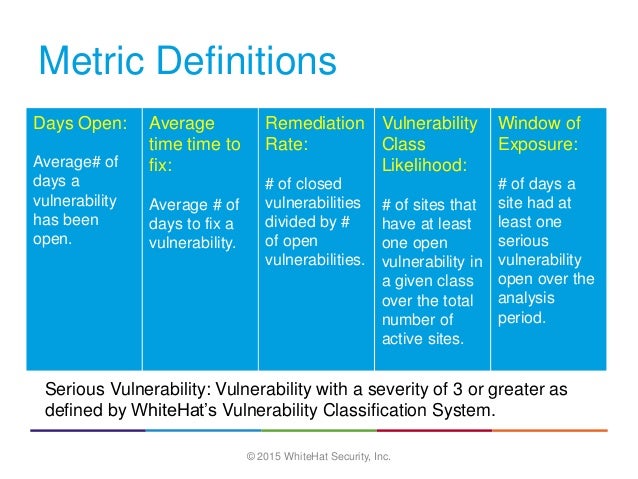
Where Flow Charts Dont Go Website Security Statistics .

Security Incident Phishing Workflow Template Servicenow Docs .
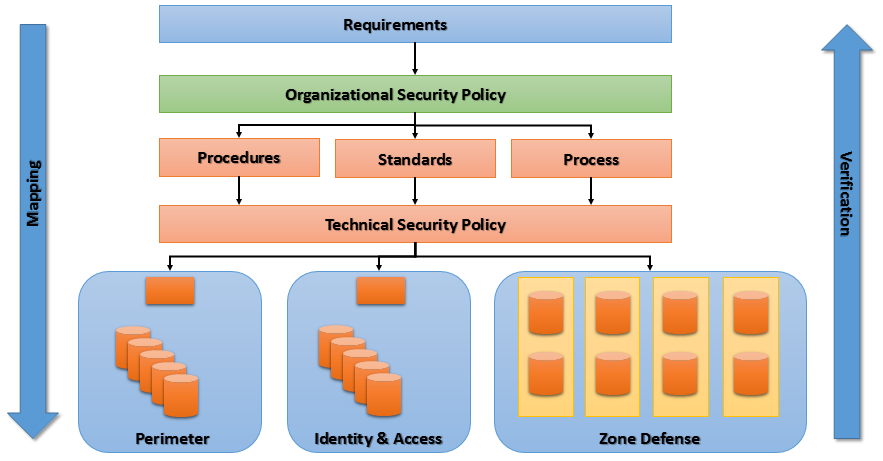
Threat And Vulnerability Management Nige The Security Guy .
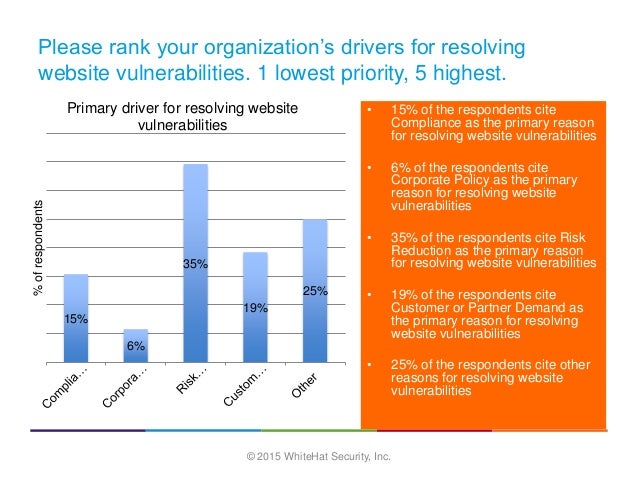
Where Flow Charts Dont Go Website Security Statistics .

Vulnerability Management Dashboard Pa Servicenow Docs .
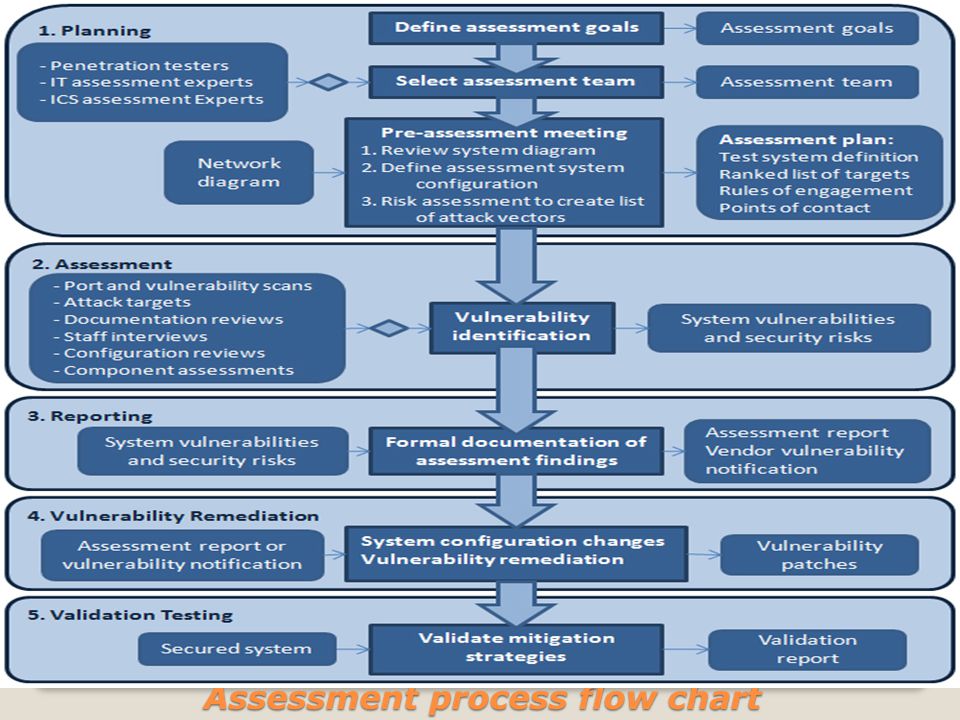
Firewall Deployment For Scada Pcn Network Security How .
- cleveland clinic my chart app
- arborvitae size chart
- nea baptist my chart
- air force reserve pay chart
- american bully colors chart
- vegetable planting chart
- metric chart
- dc wire size chart
- pulse pressure chart
- underarm temperature chart
- children fever chart
- white house black market size chart
- gear ratio chart
- berglund center seating chart
- hjc helmet size chart
- usps postage rates 2019 chart
- transformer sizing chart
- birth chart report
- nags head tide chart
- nuggets seating chart
- envelope size chart
- allen event center seating chart
- siser color chart
- petco park seating chart
- wood floor stain colors chart
- weight chart for women
- pocket chart
- keds size chart
- place value chart to millions
- fibroid sizes chart