Vulnerability Remediation Process Flow Chart - Applying Ai In Application Security

Applying Ai In Application Security

Creating A Remediation Operation For Truesight Server .

Vulnerability Assessment Flow Chart Adapted From The Us Doe .

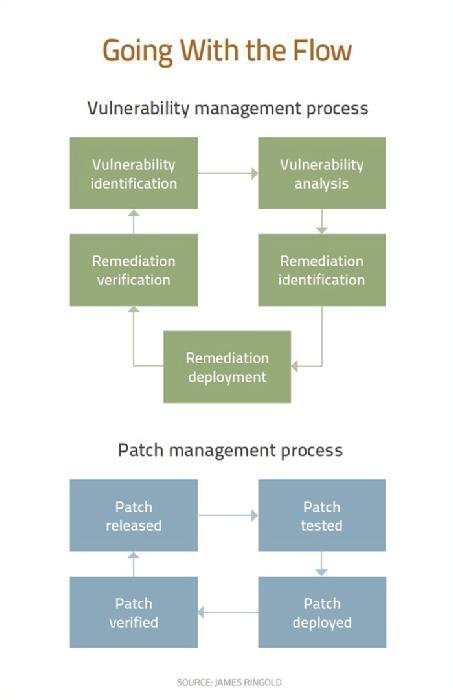
Vulnerability Management Process Flow Chart Www .

Vulnerability Group And Vulnerable Item States Servicenow Docs .

Vulnerability Remediation You Only Have 4 Options Synopsys .

Risk Triage For Security Vulnerability Announcements .
A Complete Guide To Network Vulnerability Assessment .

Vulnerability Management Qualys Inc .

Vulnerability Response Remediation Overview Servicenow Docs .
The Vulnerability Management Process After Equifax .

Cybersecurity Specialist It Security And Service Cynexlink .

Application Security Deconstructed And Demystified .
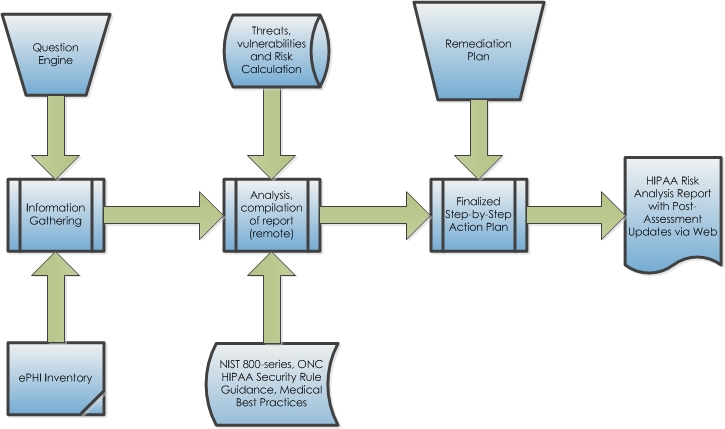
Hipaa Security Risk Analysis Data Risk Managementdata Risk .

Scan Vulnerability Workflow Servicenow Docs .
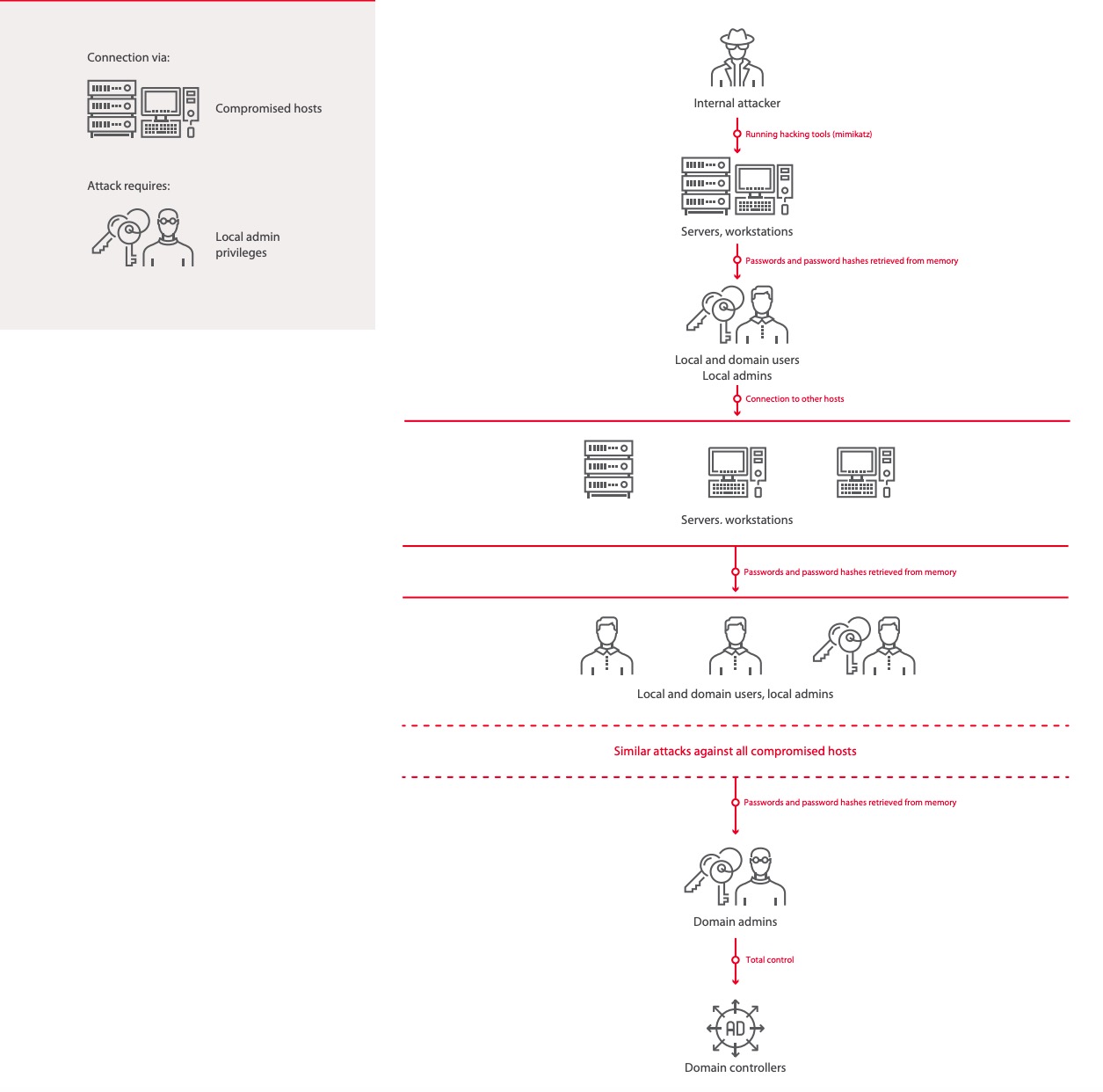
Industrial Control Systems Cyber Security Attack Vectors .

Psirt Services Framework 1 0 .
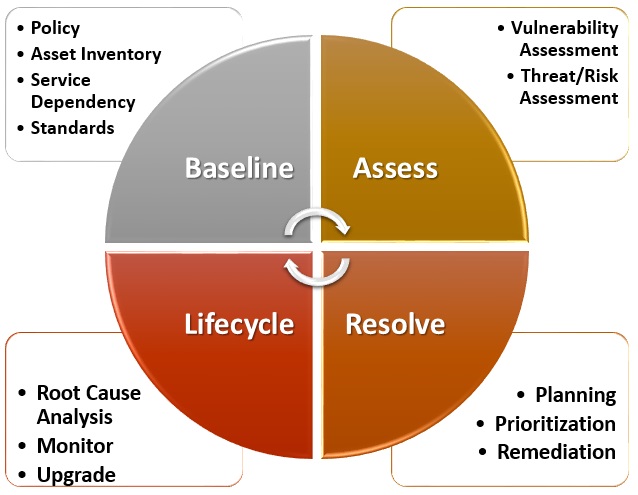
Vulnerability Nige The Security Guy .

Understanding The Vulnerability Response Application .

What Is Sast And How Does It Work Synopsys .

Vulnerability Management Policy Pdf Free Download .

Building Strong Ulnerability Management Program Being .

Prioritizing Remediation Plug Into The Firehose Of .

Software Vulnerability Management Secunia R D Patch Management .

Vulnerability Management Qualys Inc .

Cyber Risk Remediation Analysis The Mitre Corporation .
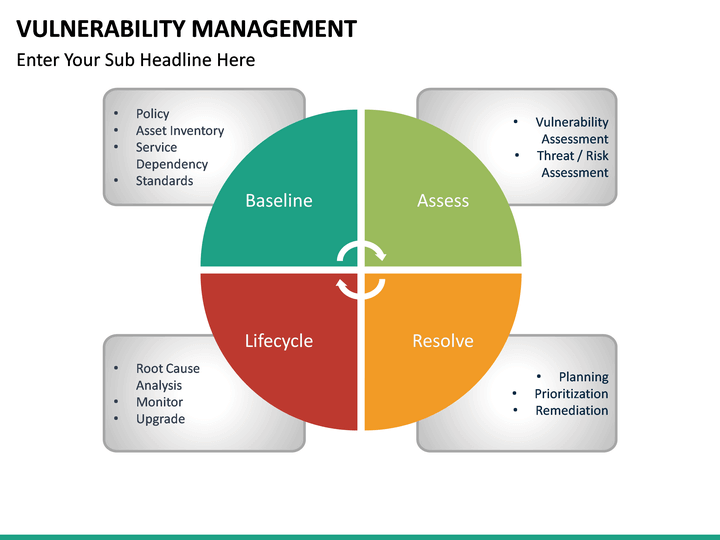
Vulnerability Management .

Application Security Deconstructed And Demystified .

I Cant Keep Up With All These Cisco Security Advisories Do .

Securosis Blog Article .
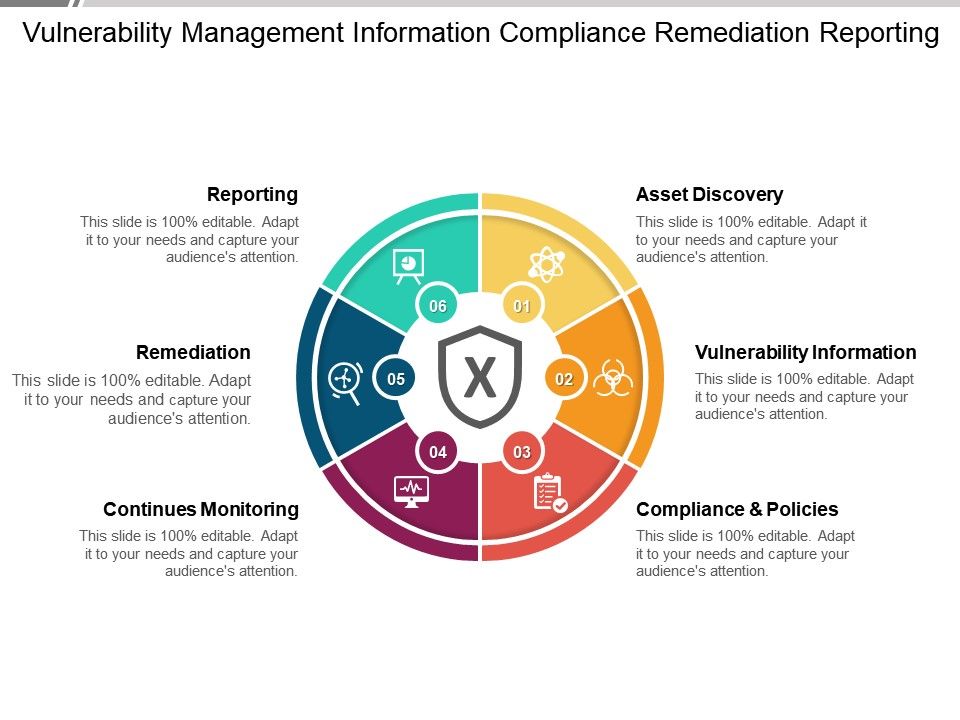
Vulnerability Management Information Compliance Remediation .

Vulnerability Management Qualys Inc .
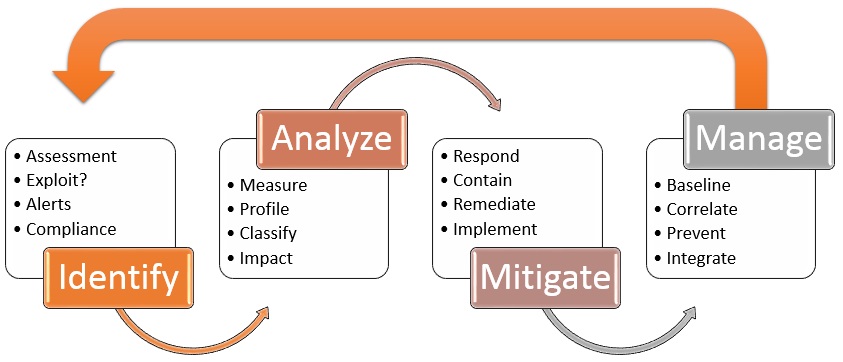
Threat And Vulnerability Management Nige The Security Guy .

Product Vision Secure Gitlab .
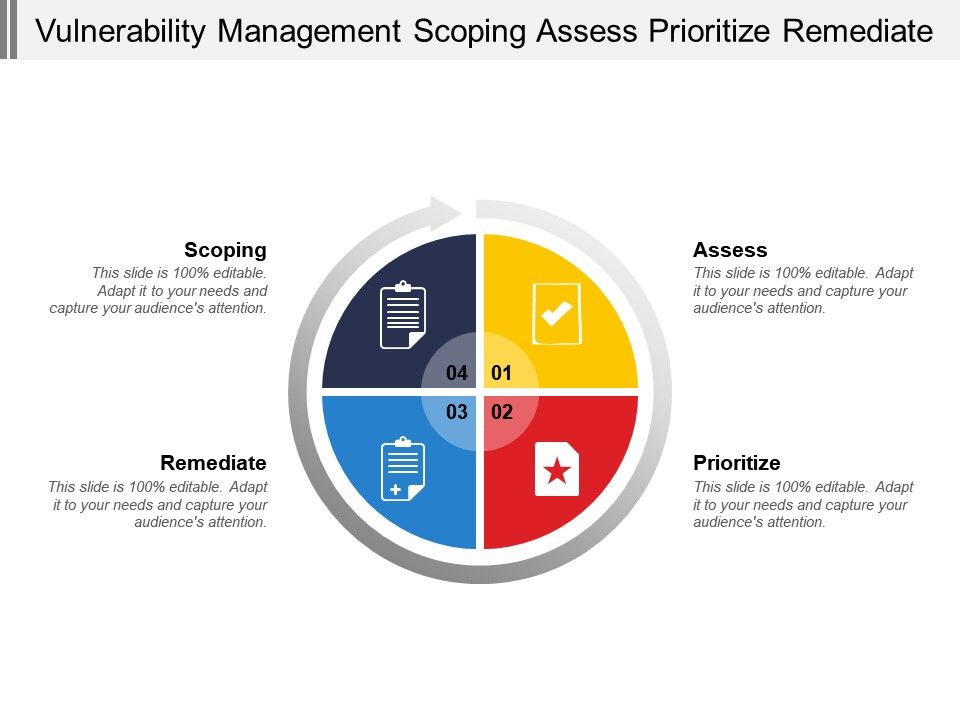
Vulnerability Management Scoping Assess Prioritize Remediate .

Understanding The Vulnerability Response Application .
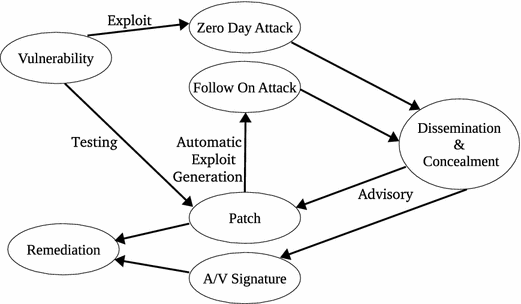
An Overview Of Vulnerability Assessment And Penetration .

Remediation Workflows .
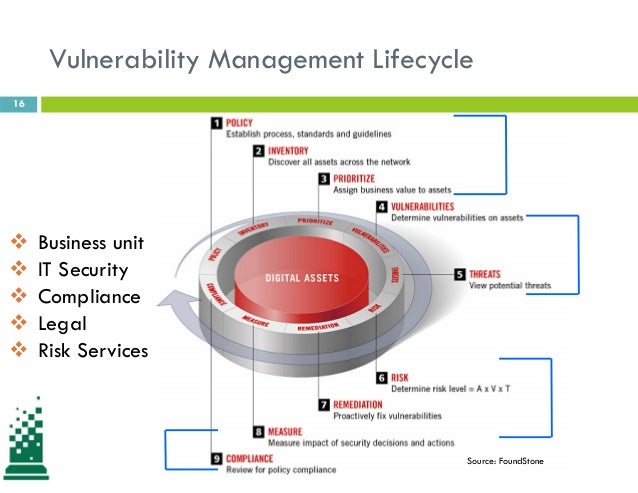
Monitoring Threats For Pci Compliance .
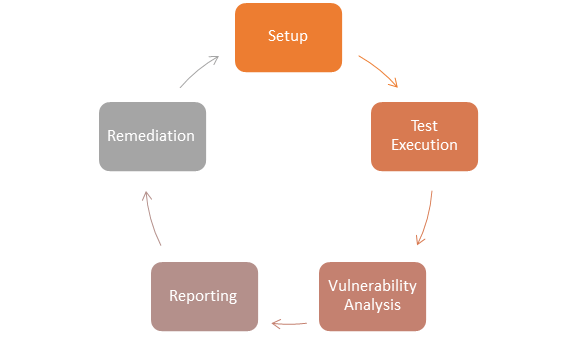
What Is Vulnerability Assessment Testing Process Vapt Scan .
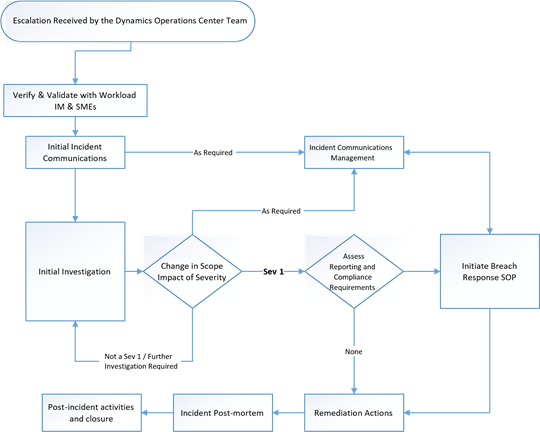
Security Incident Management In Microsoft Dynamics 365 .

Applying Ai In Application Security .
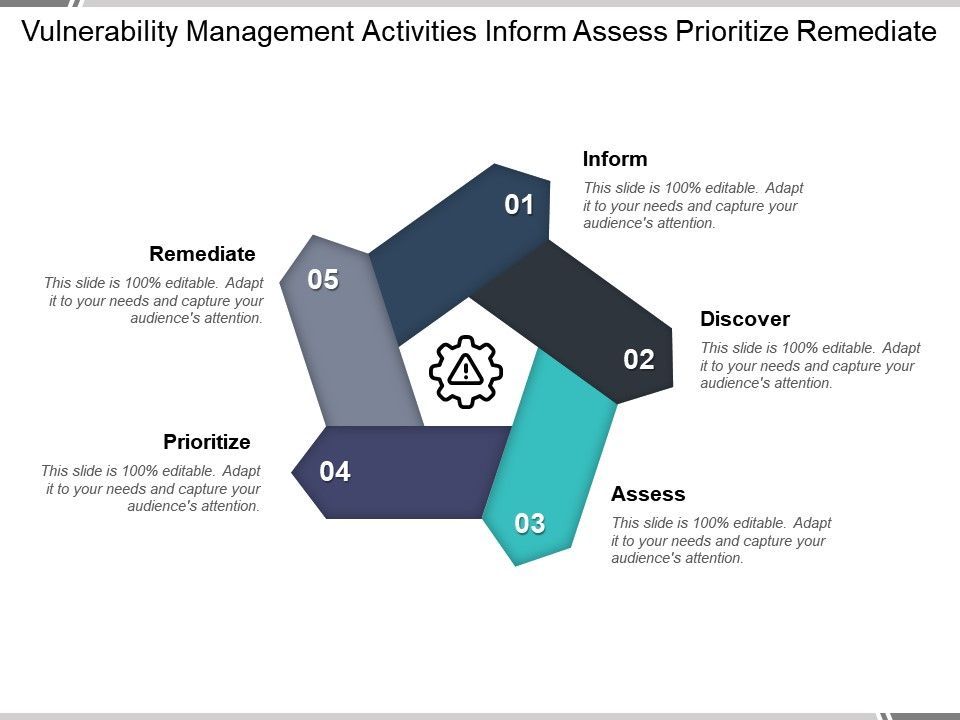
Vulnerability Management Activities Inform Assess Prioritize .

Typical Flow Chart Of The Model Development Left Flowchart .
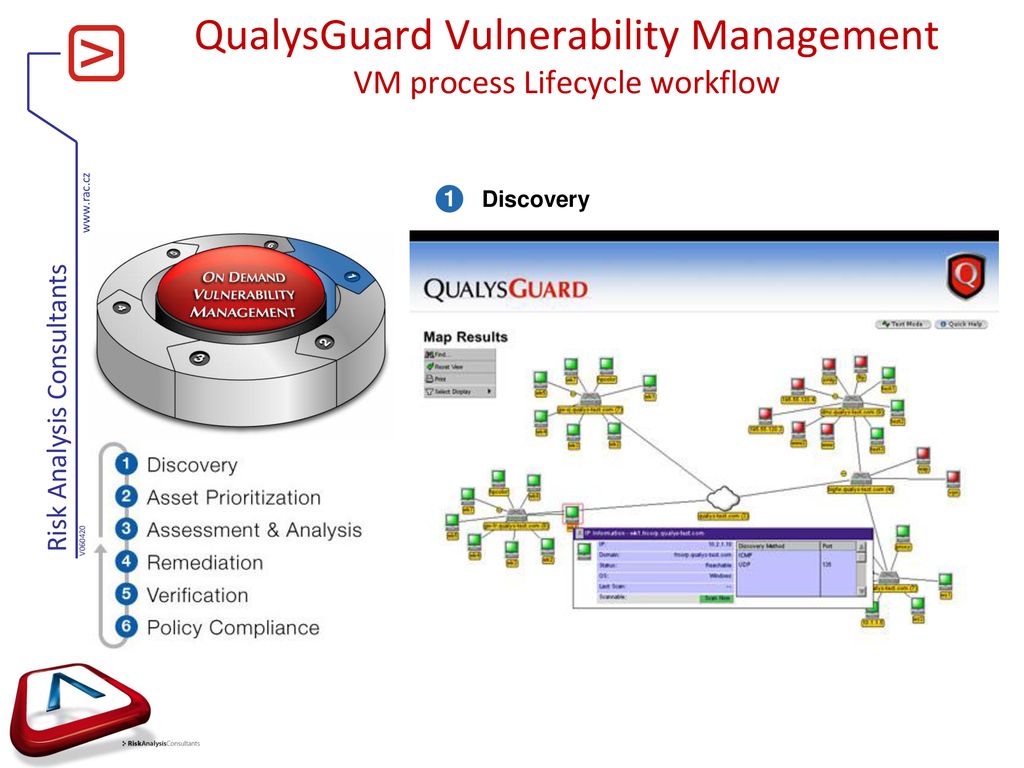
Qg Vulnerability Management Module Ppt Download .
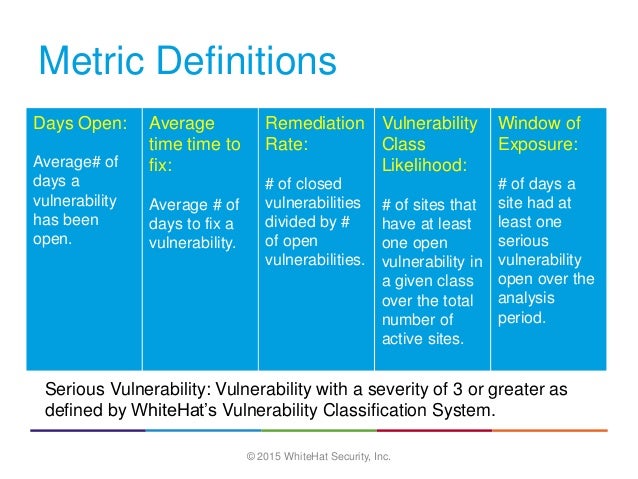
Where Flow Charts Dont Go Website Security Statistics .

Security Incident Phishing Workflow Template Servicenow Docs .
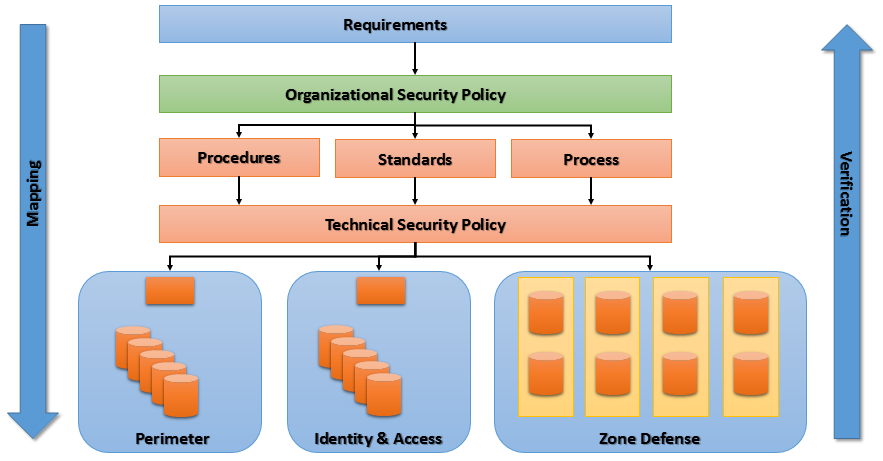
Threat And Vulnerability Management Nige The Security Guy .
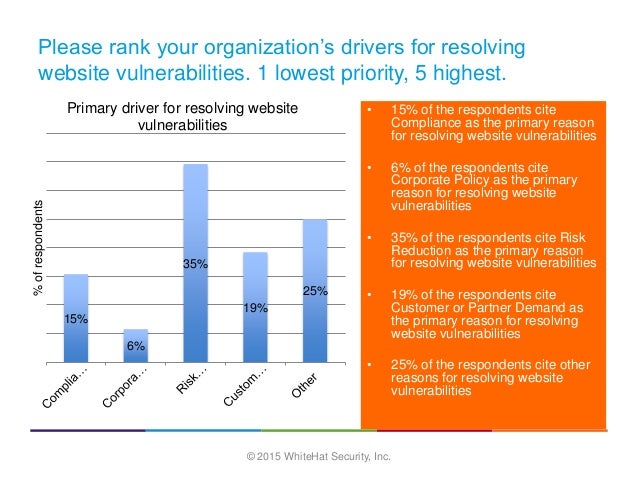
Where Flow Charts Dont Go Website Security Statistics .

Vulnerability Management Dashboard Pa Servicenow Docs .
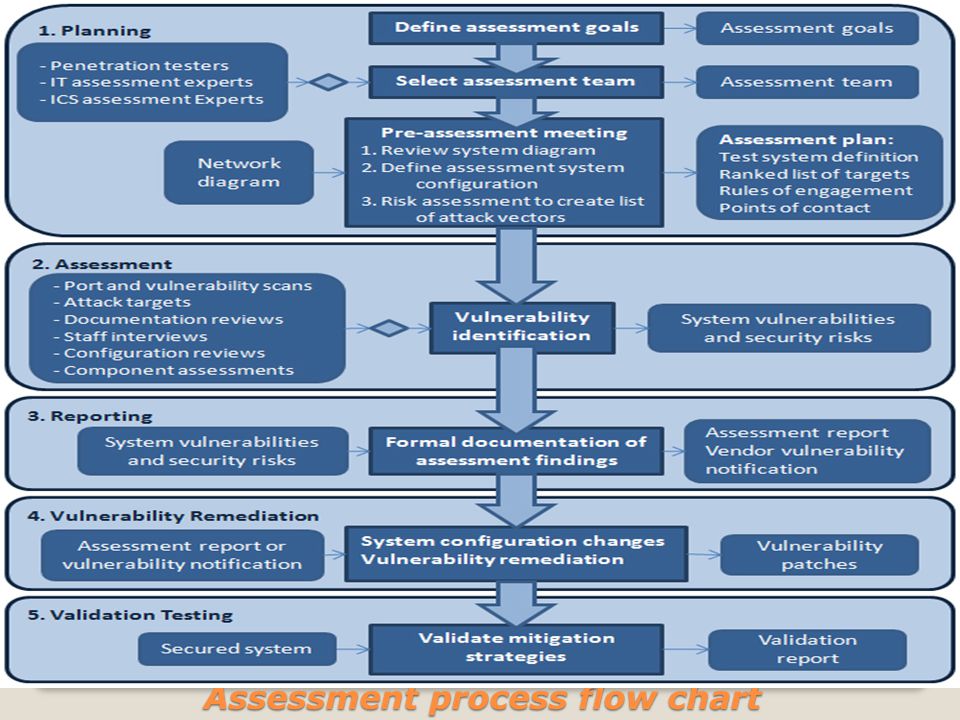
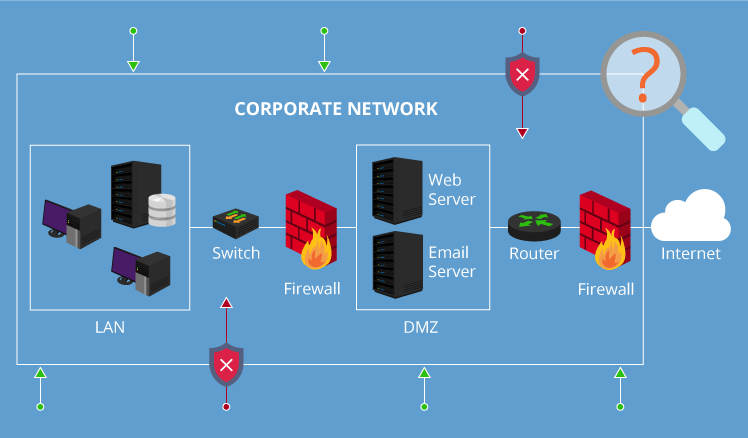
Firewall Deployment For Scada Pcn Network Security How .
- merit badge picture chart
- how to insert a chart
- free vedic horoscope chart online
- size chart salt n pepper
- dwdm channel wavelength chart
- federal budget 2018 pie chart
- ethylene glycol specific gravity chart
- paul mitchell the color swatch chart
- nyc doe organizational chart 2018
- tropical house charts
- standard wire gauge chart download
- health and human services org chart
- dow event center theater seating chart
- depth chart dallas
- excel chart move with scroll
- australian top 40 charts history
- 500 ton crane load chart
- political orientation chart
- bojangles coliseum seating chart charlotte nc
- blood sugar chart 2018
- dunkin donuts allergen chart
- thomson dreamliner seating chart 787
- comparison chart pdf
- super bowl 2018 chart
- con law ii flow chart
- shoe conversion chart inches to size
- polaris snowmobile clutch weight chart
- cold form tap drill chart
- circular mils chart
- personal goal chart template