Vulnerability Remediation Process Flow Chart - Firewall Deployment For Scada Pcn Network Security How
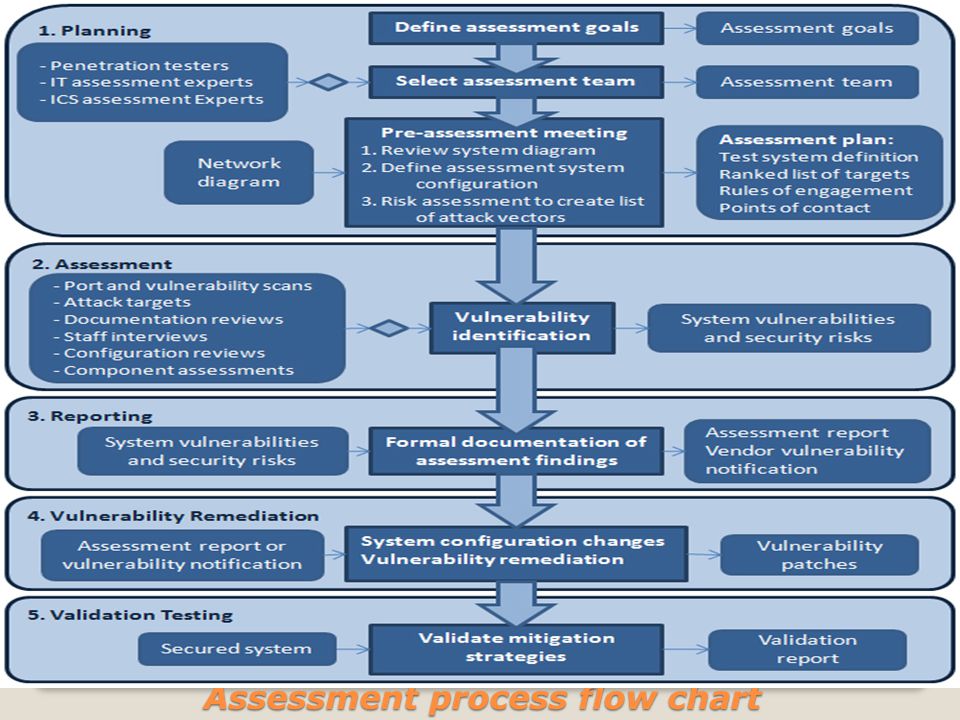
Firewall Deployment For Scada Pcn Network Security How

Creating A Remediation Operation For Truesight Server .

Vulnerability Assessment Flow Chart Adapted From The Us Doe .

Vulnerability Management Process Flow Chart Www .

Vulnerability Group And Vulnerable Item States Servicenow Docs .

Vulnerability Remediation You Only Have 4 Options Synopsys .

Risk Triage For Security Vulnerability Announcements .
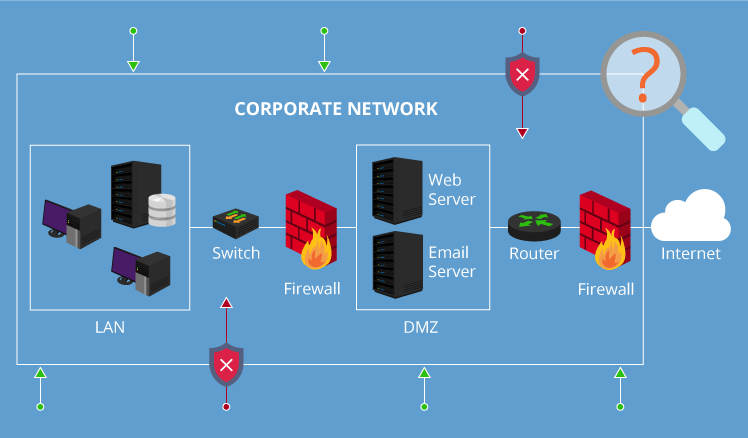
A Complete Guide To Network Vulnerability Assessment .

Vulnerability Management Qualys Inc .

Vulnerability Response Remediation Overview Servicenow Docs .
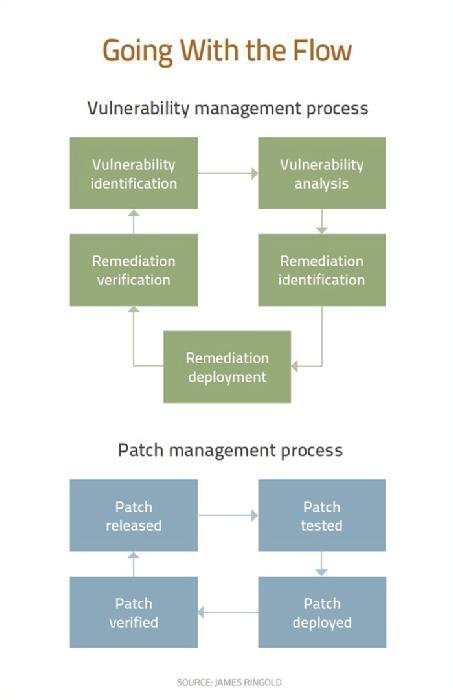
The Vulnerability Management Process After Equifax .

Cybersecurity Specialist It Security And Service Cynexlink .

Application Security Deconstructed And Demystified .
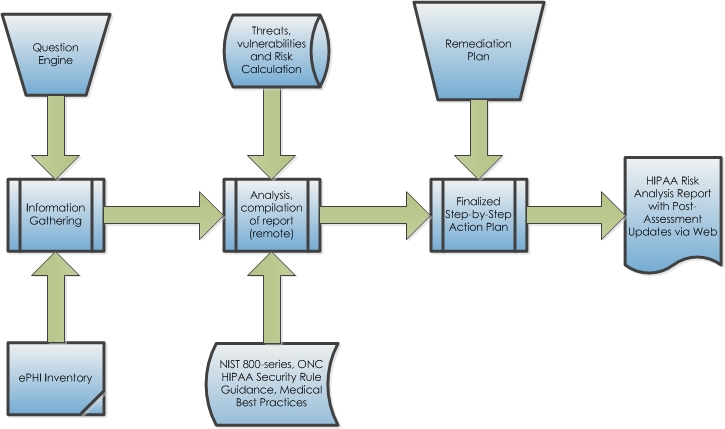
Hipaa Security Risk Analysis Data Risk Managementdata Risk .

Scan Vulnerability Workflow Servicenow Docs .
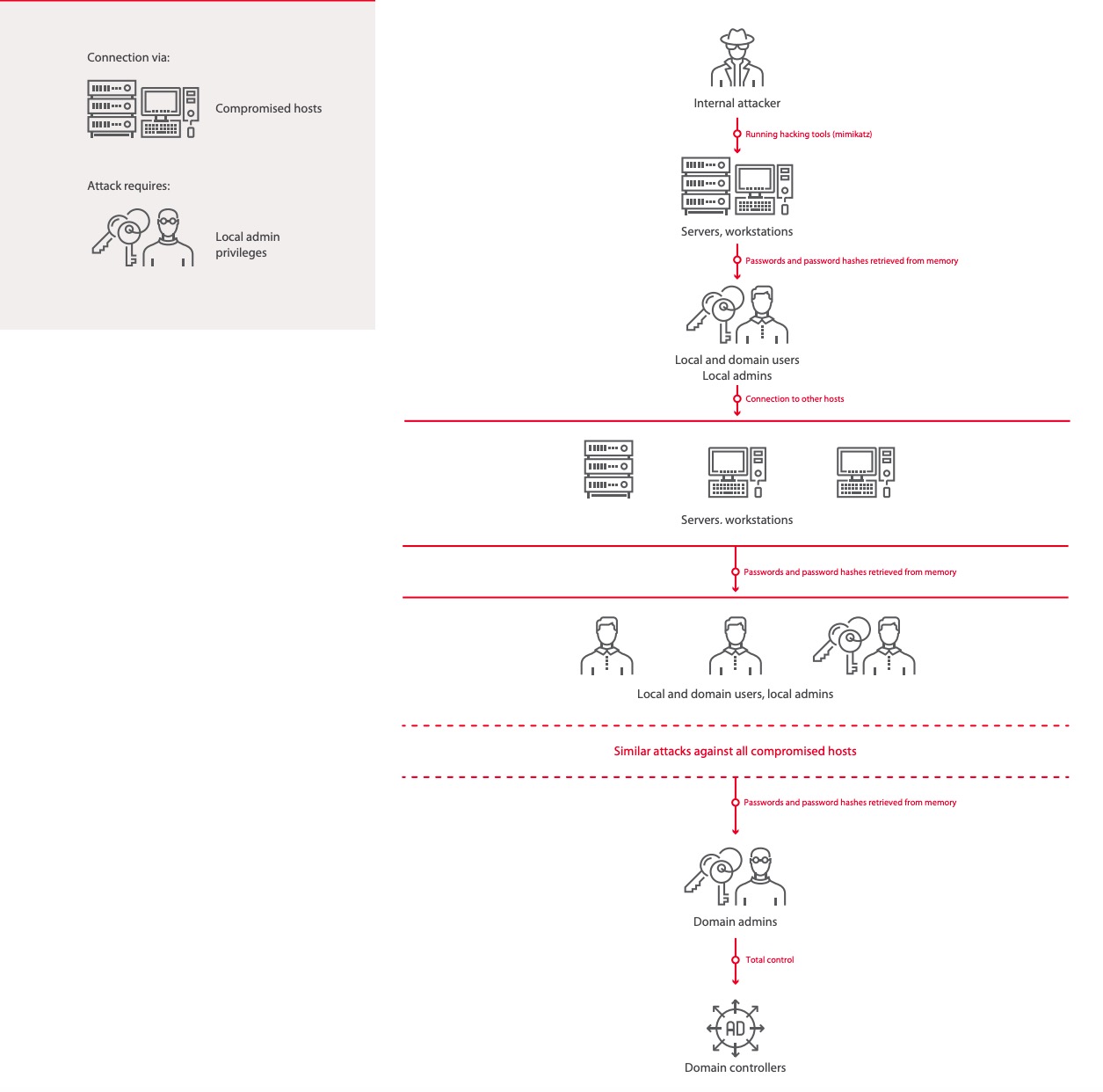
Industrial Control Systems Cyber Security Attack Vectors .

Psirt Services Framework 1 0 .
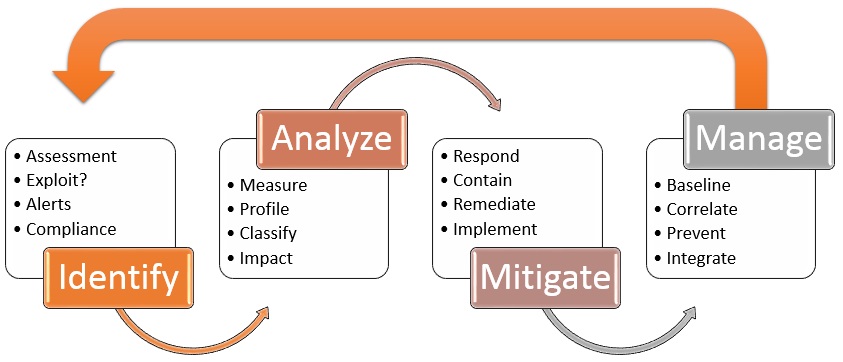
Vulnerability Nige The Security Guy .

Understanding The Vulnerability Response Application .

What Is Sast And How Does It Work Synopsys .

Vulnerability Management Policy Pdf Free Download .

Building Strong Ulnerability Management Program Being .

Prioritizing Remediation Plug Into The Firehose Of .

Software Vulnerability Management Secunia R D Patch Management .

Vulnerability Management Qualys Inc .

Cyber Risk Remediation Analysis The Mitre Corporation .
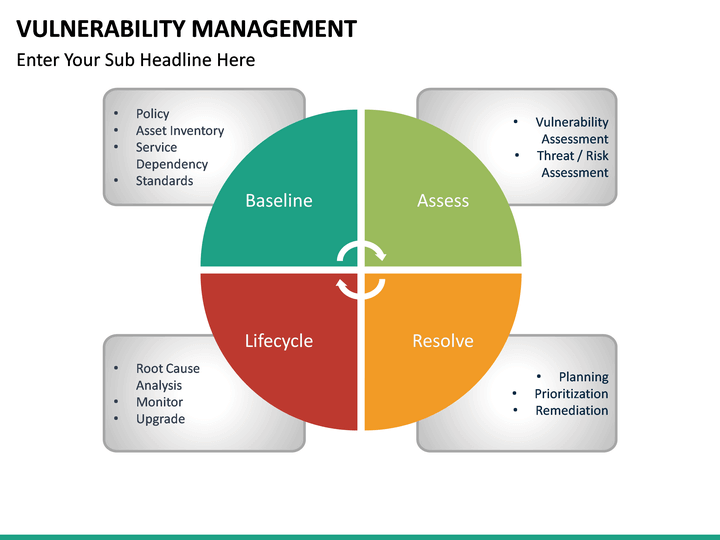
Vulnerability Management .

Application Security Deconstructed And Demystified .

I Cant Keep Up With All These Cisco Security Advisories Do .

Securosis Blog Article .
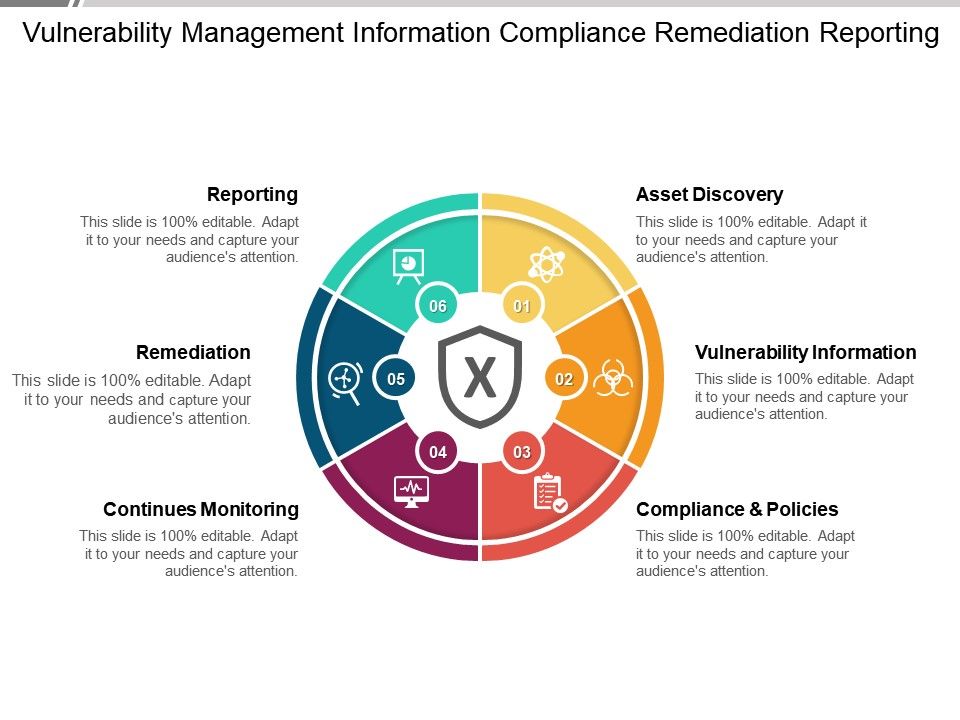
Vulnerability Management Information Compliance Remediation .

Vulnerability Management Qualys Inc .
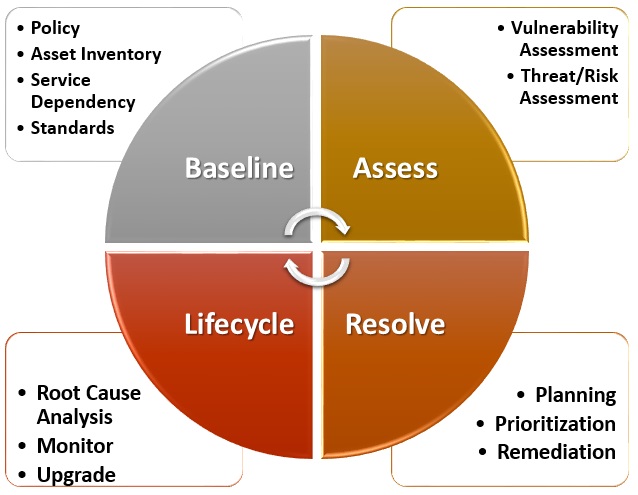
Threat And Vulnerability Management Nige The Security Guy .

Product Vision Secure Gitlab .
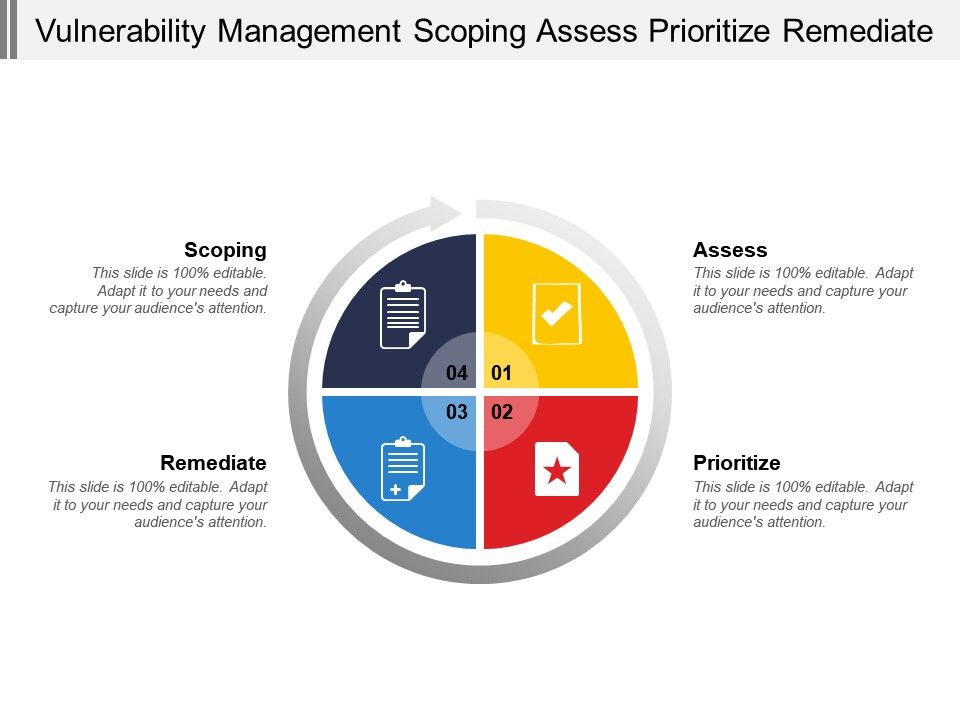
Vulnerability Management Scoping Assess Prioritize Remediate .

Understanding The Vulnerability Response Application .
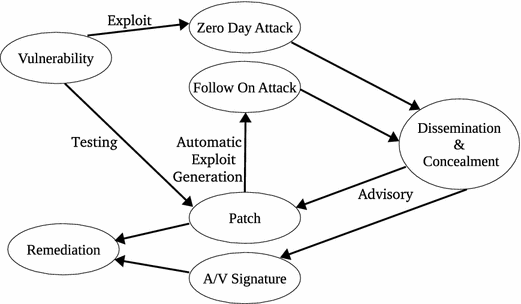
An Overview Of Vulnerability Assessment And Penetration .

Remediation Workflows .
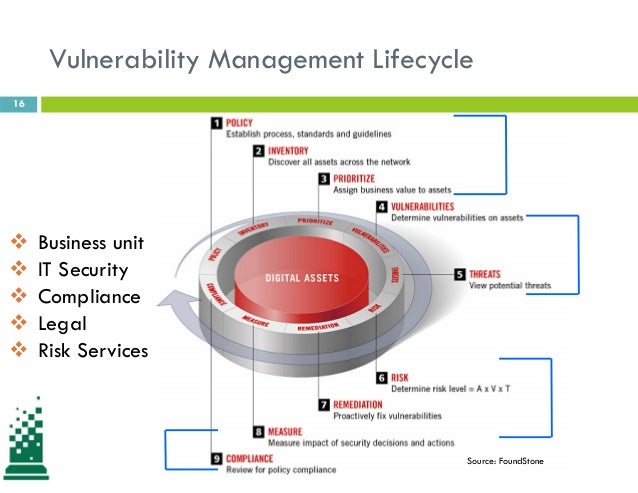
Monitoring Threats For Pci Compliance .
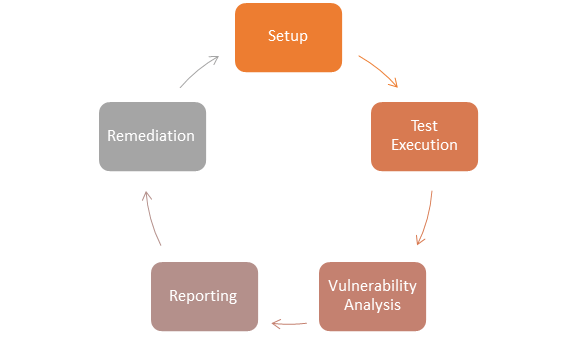
What Is Vulnerability Assessment Testing Process Vapt Scan .
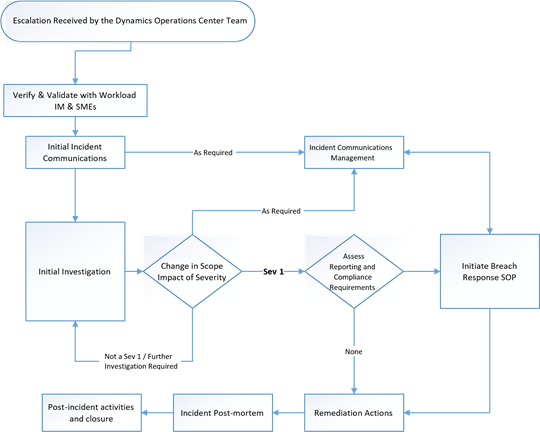
Security Incident Management In Microsoft Dynamics 365 .

Applying Ai In Application Security .
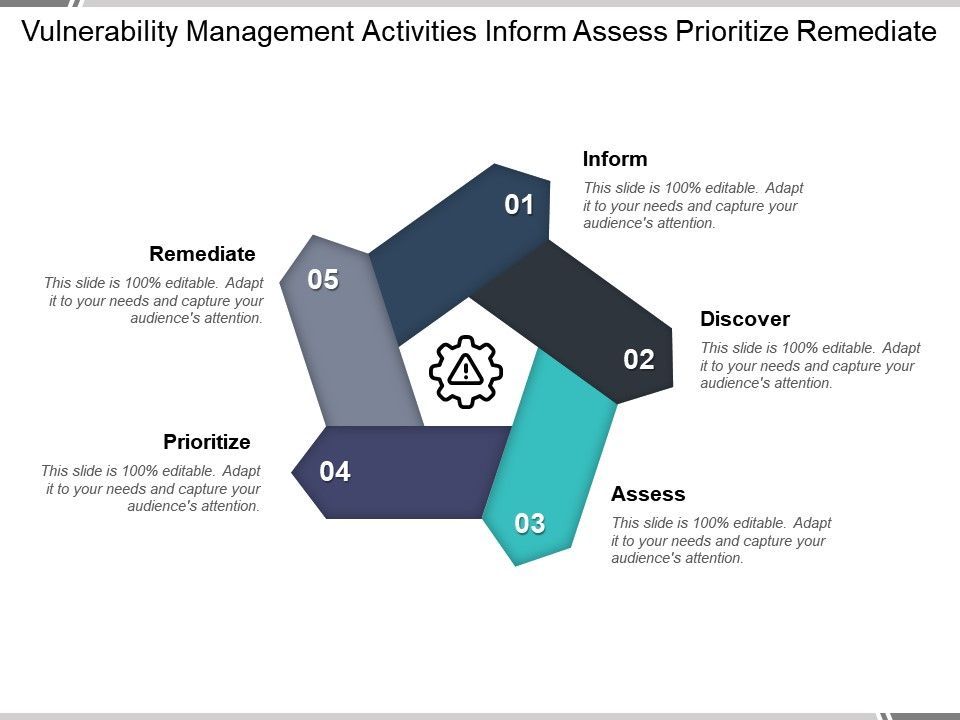
Vulnerability Management Activities Inform Assess Prioritize .

Typical Flow Chart Of The Model Development Left Flowchart .
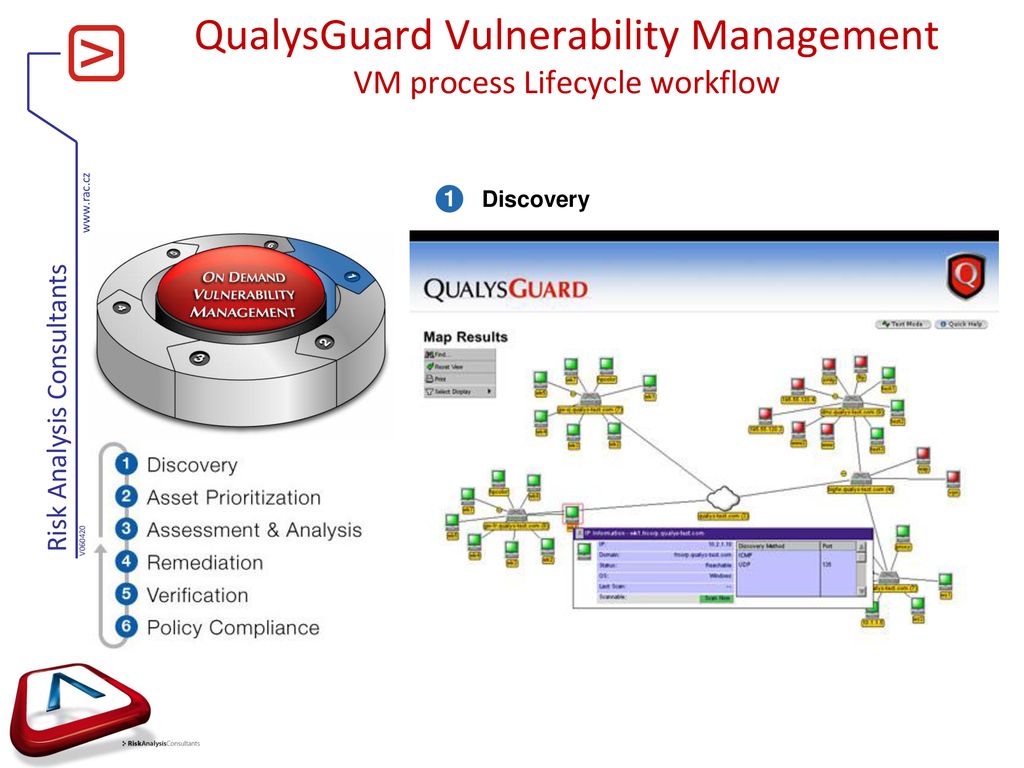
Qg Vulnerability Management Module Ppt Download .
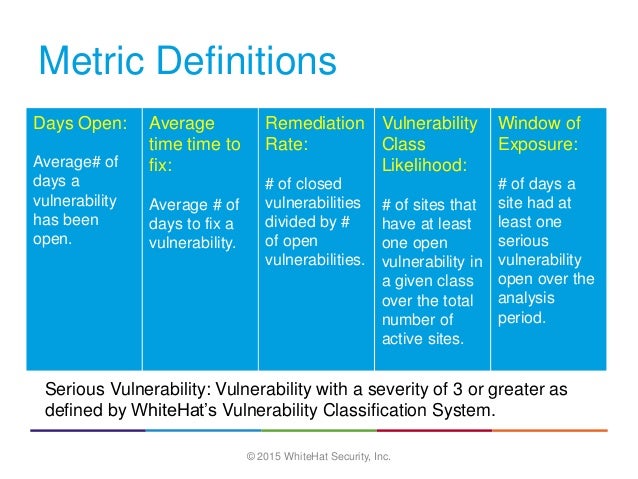
Where Flow Charts Dont Go Website Security Statistics .

Security Incident Phishing Workflow Template Servicenow Docs .
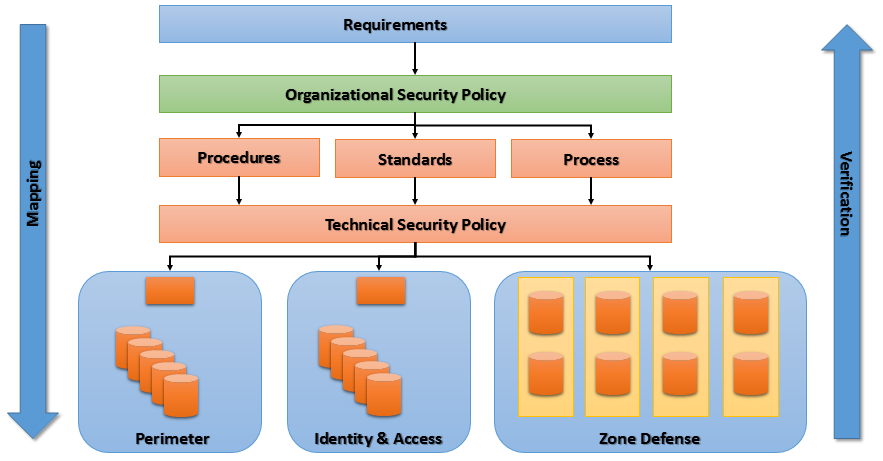
Threat And Vulnerability Management Nige The Security Guy .
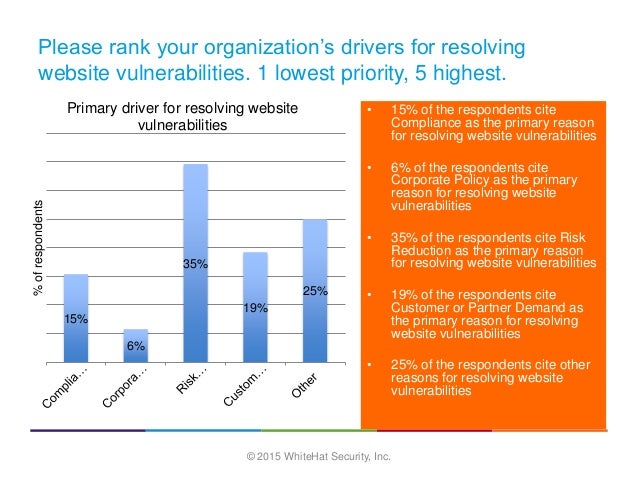
Where Flow Charts Dont Go Website Security Statistics .

Vulnerability Management Dashboard Pa Servicenow Docs .

Firewall Deployment For Scada Pcn Network Security How .
- rebar lapping chart
- chart of sentences
- university of iowa my chart
- ac temp pressure chart
- capo chart pdf
- blood normal values chart
- wealth distribution chart in america
- lic jeevan shanti chart
- treadmill elevation pace chart
- piston ring gap chart
- lake calhoun depth chart
- pechanga seating chart san diego
- polycab aluminium cable current rating chart
- informational text anchor chart 2nd grade
- ibu dosage chart
- us air force identification chart
- ibbotson stock chart
- fx rate chart
- p value chart for t test
- tally chart worksheets grade 5
- detroit lions rb depth chart
- american university organizational chart
- what does g4 p2 mean in mrs santiago's chart quizlet
- hailey baldwin birth chart
- ems chart template
- how to write bar chart in ielts
- insanity chart
- jeffersonian democracy vs jacksonian democracy chart
- renvy size chart
- excel quartile chart