Vulnerability Analysis Chart - How To Perform It Security Risk Assessment

How To Perform It Security Risk Assessment

Wave Exposure Methodological Flow Chart For Coastal .

Flow Chart For Flood Structural Vulnerability Assessment .

Conducting A Vulnerability Assessment Smart Trees Pacific .
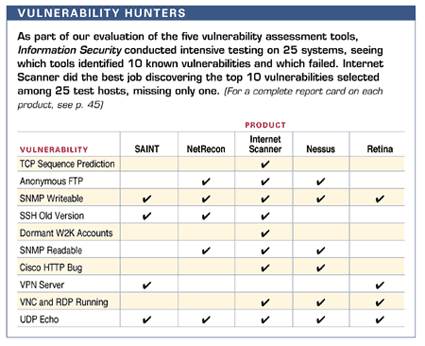
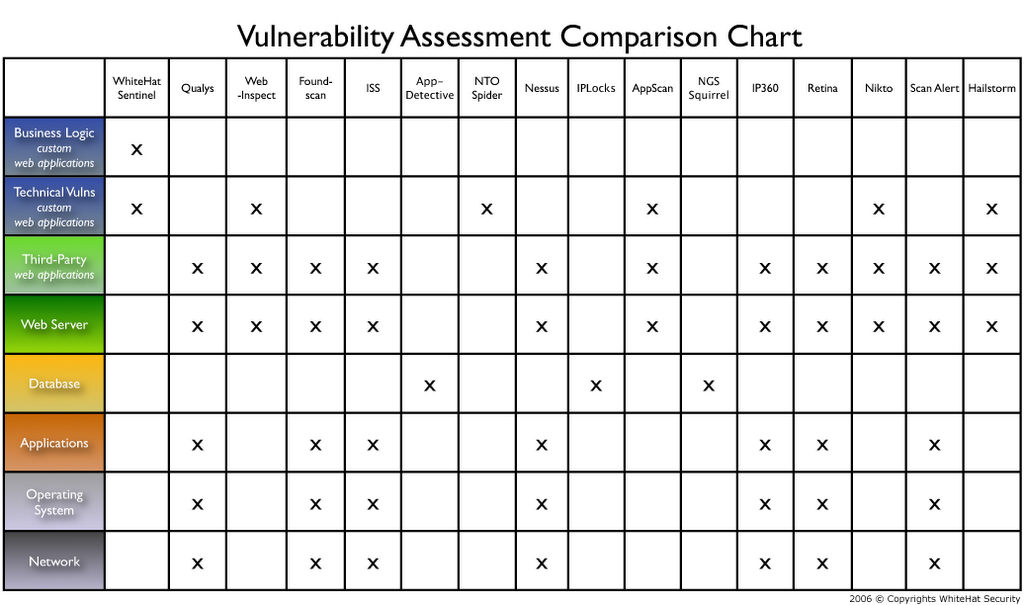
Testing And Comparing Vulnerability Analysis Tools .

Flow Chart Of Methodology For Groundwater Vulnerability .

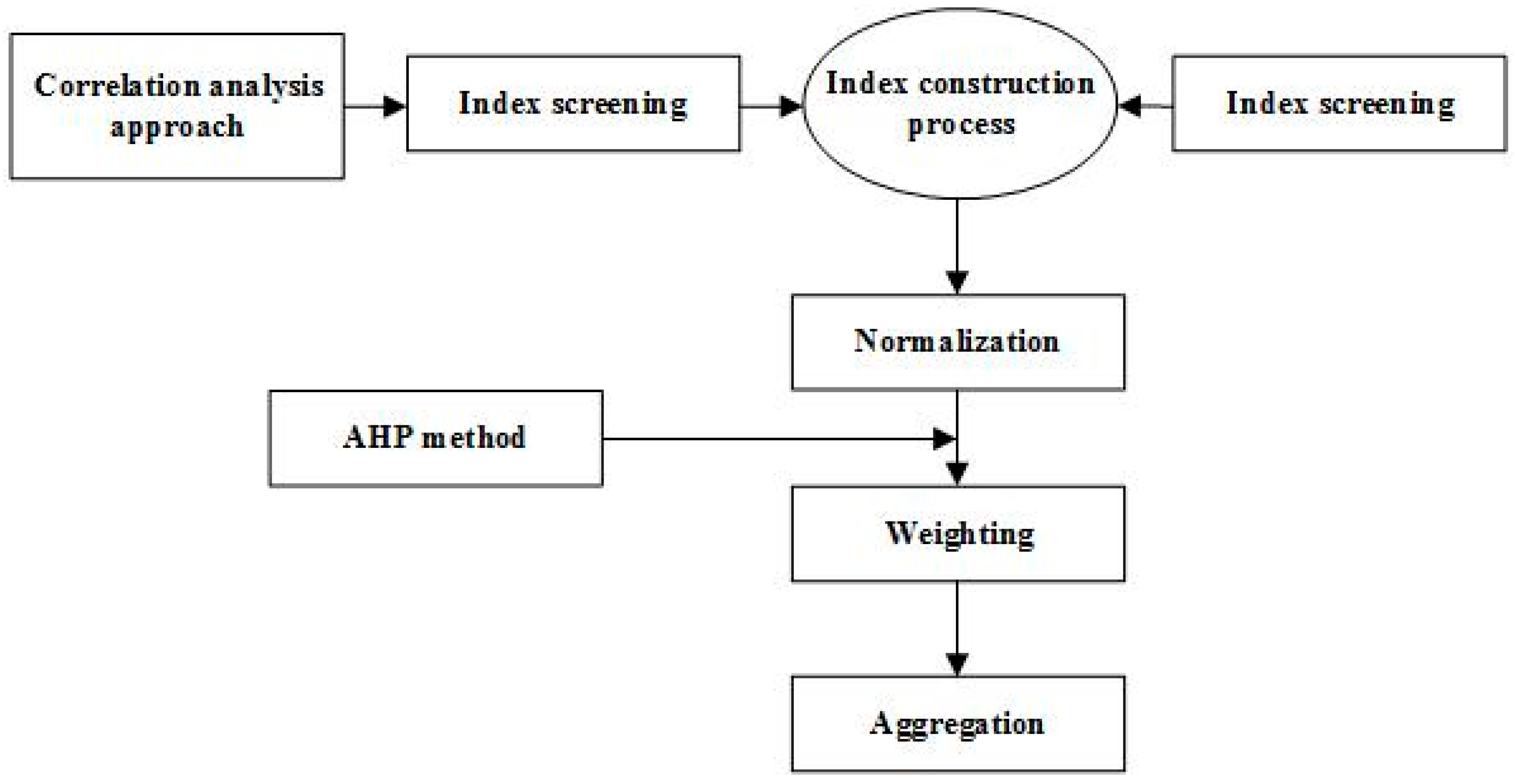
Conceptual Framework For The Risk Vulnerability Analysis Of .

Figure 2 From Groundwater Vulnerability Assessment Using .

Flowchart For Vulnerability Assessment Download .
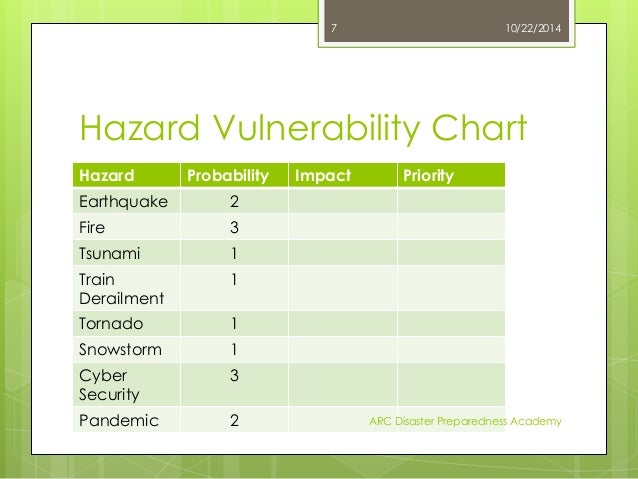
Hazard Vulnerability Assessments .

Seismic Vulnerability Assessment Flow Chart Download .
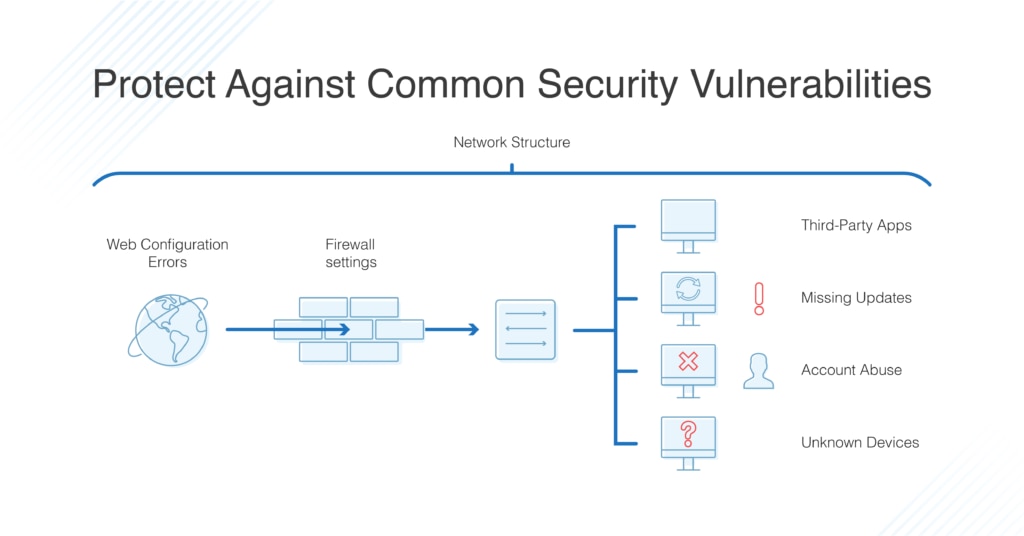
Top 14 Paid And Free Vulnerability Scanner Tools 2019 Dnsstuff .
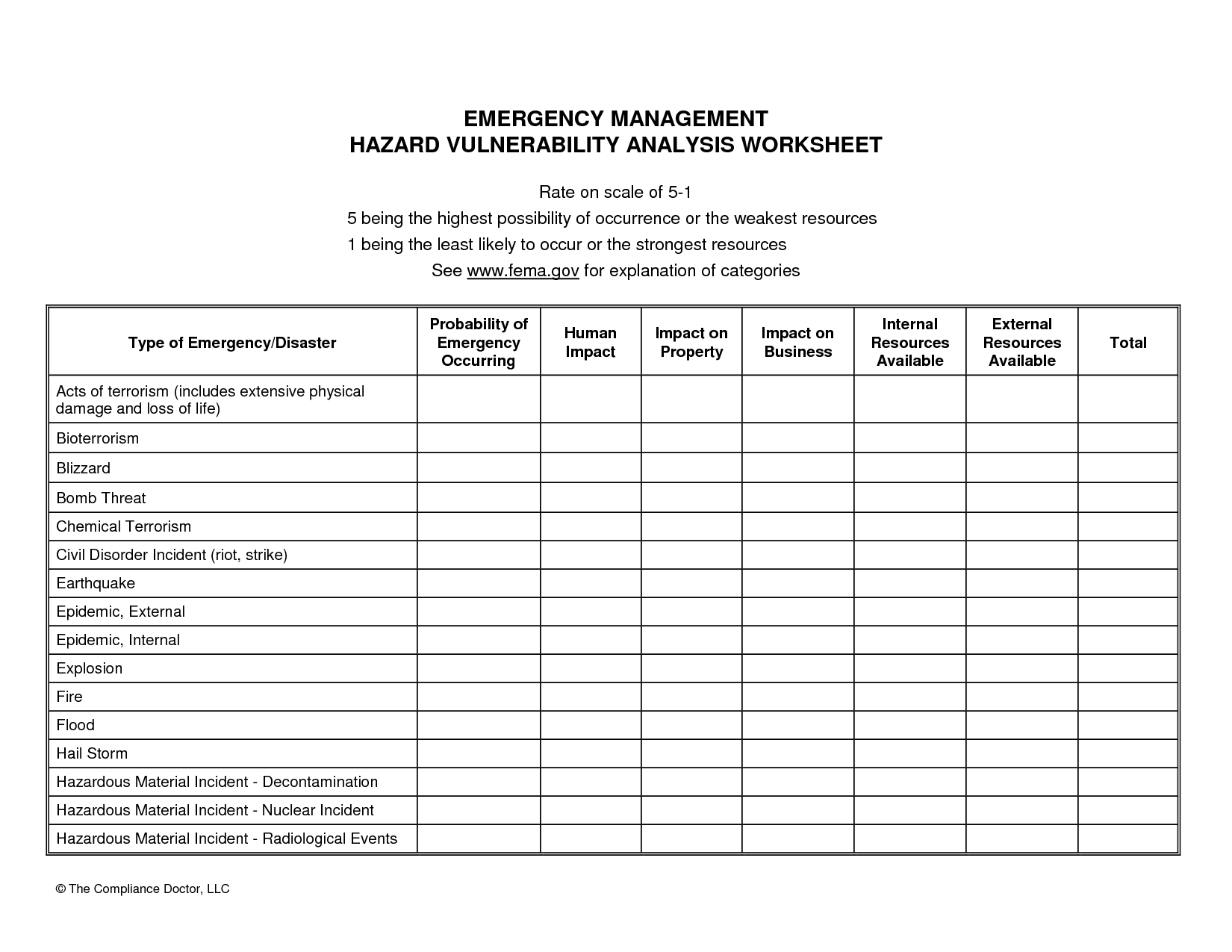
Hazard Vulnerability Analysis Hfm Wiki Fandom .
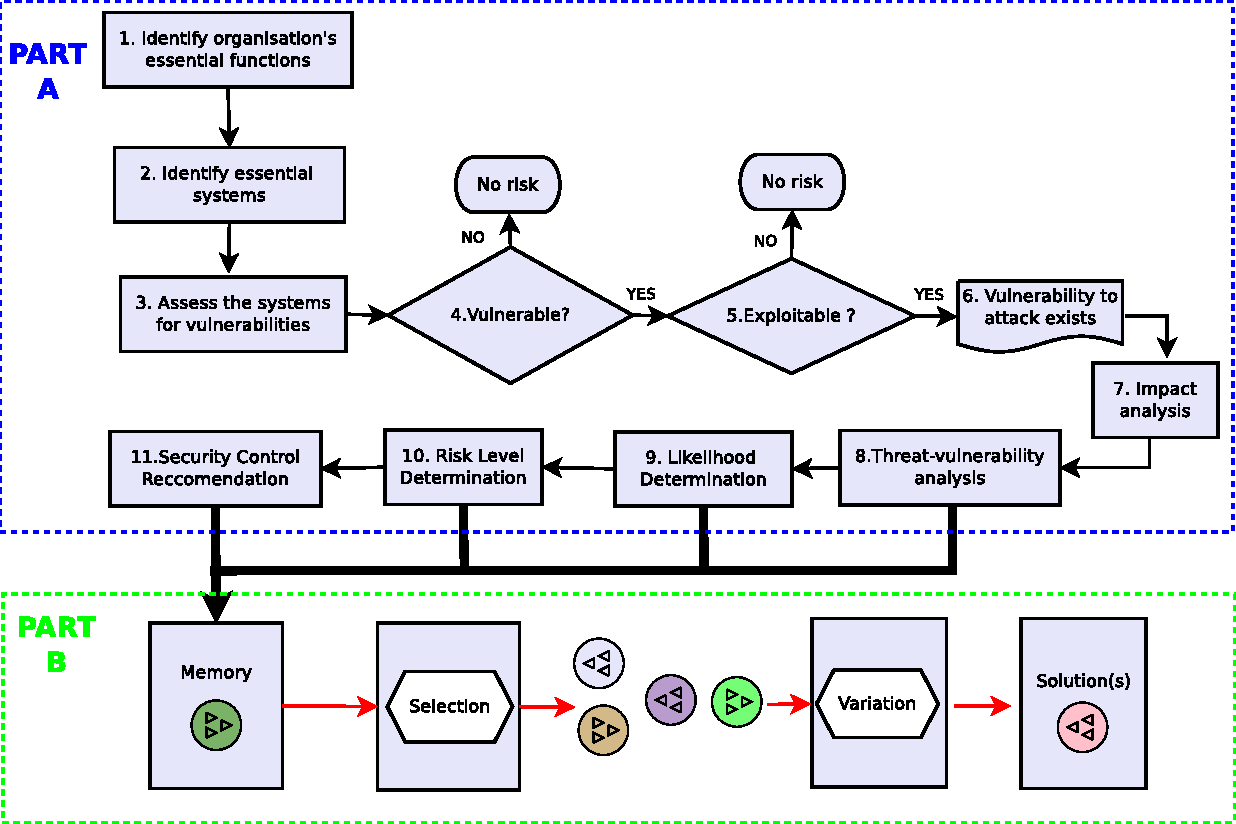
Figure 4 2 From A Risk Assessment And Optimisation Model For .
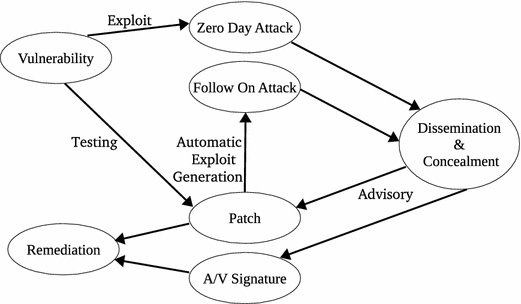
An Overview Of Vulnerability Assessment And Penetration .

Develop Preliminary Vulnerability And Risk Assessment E .

Vulnerability Management Qualys Inc .

5 1 Introduction To Exposure Vulnerability And Risk .

Using Vulnerability And Exploit Analysis To Effectively .

Vulnerability Management Process Flow Chart Www .
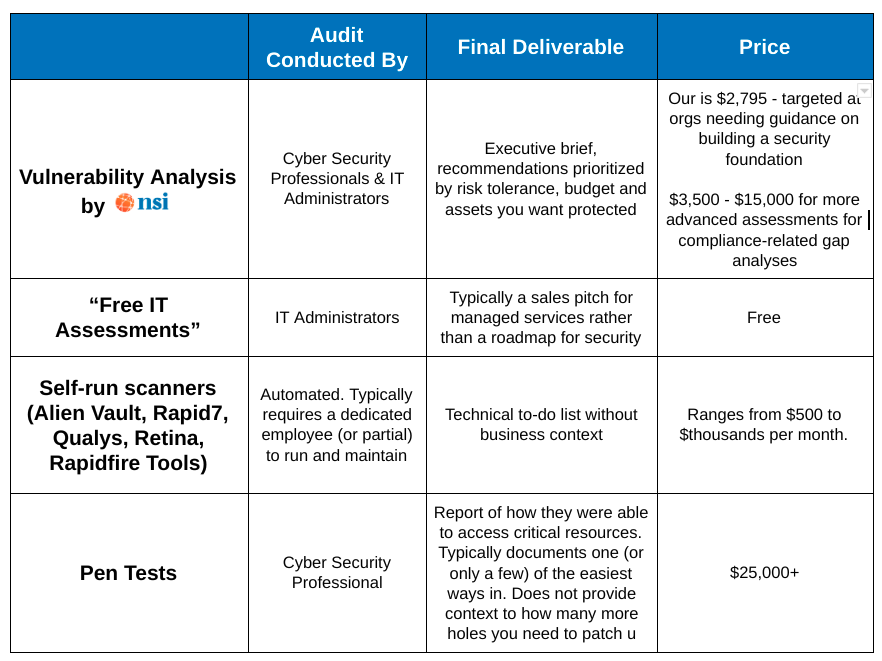
Best Vulnerability Assessment In Connecticut For Smbs Nsi .

What Is A Vulnerability Assessment Vulnerability .

How To Perform It Security Risk Assessment .

An Approach For Measuring Social Vulnerability In Context .

Flow Chart Of The Processes Involved In The Analysis Of The .
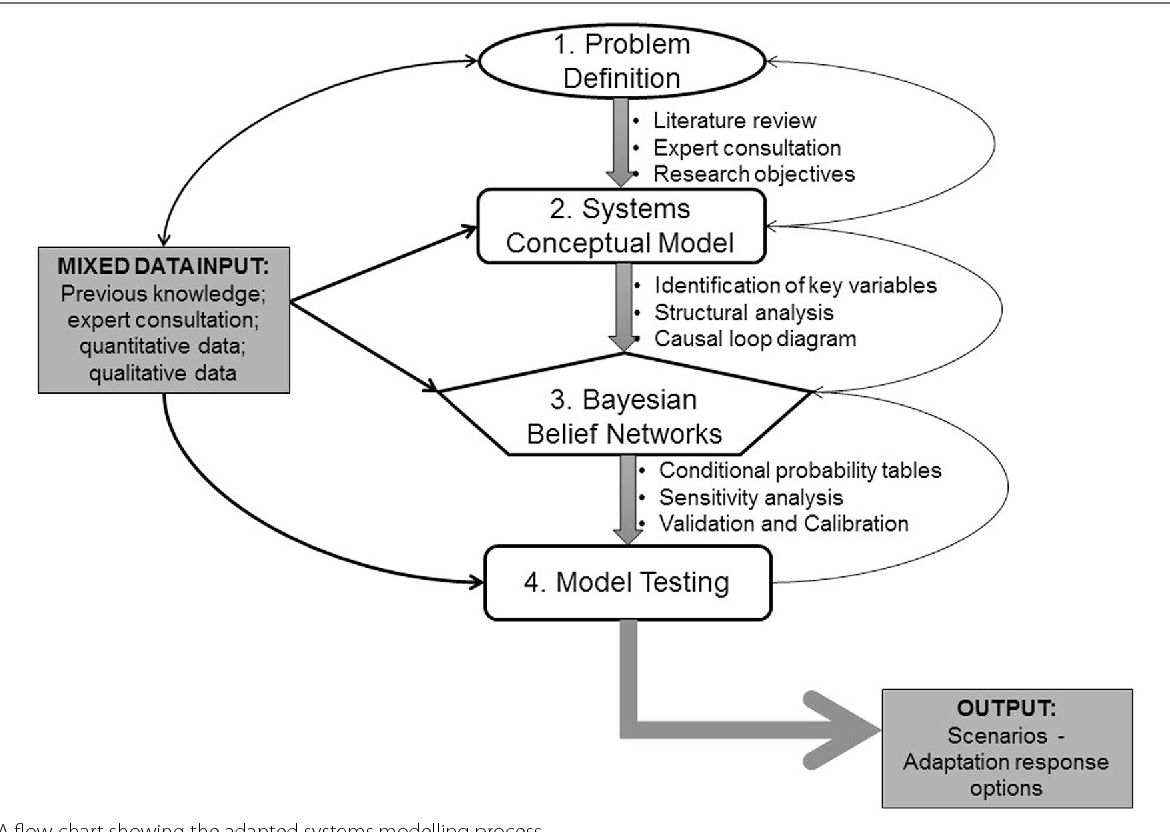
Figure 1 From An Integrated Risk And Vulnerability .

Equations Vulnerability To Conflict And Performance Risk .
Ijgi Free Full Text A Gis Based Support Vector Machine .
What Is A Vulnerability Assessment Vulnerability .
Jeremiah Grossman Vulnerability Stack .

7 2 Generating Physical Vulnerability Curves Charim .

Vulnerability Assessment And Penetration Testing Difference .
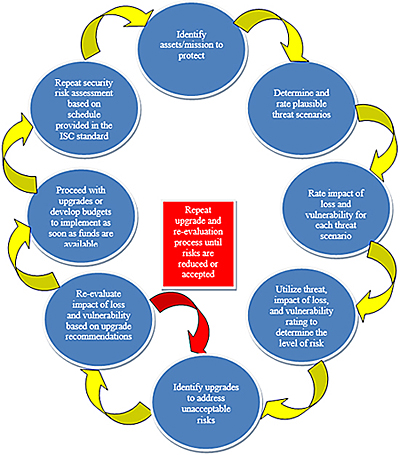
Threat Vulnerability Assessments And Risk Analysis Wbdg .
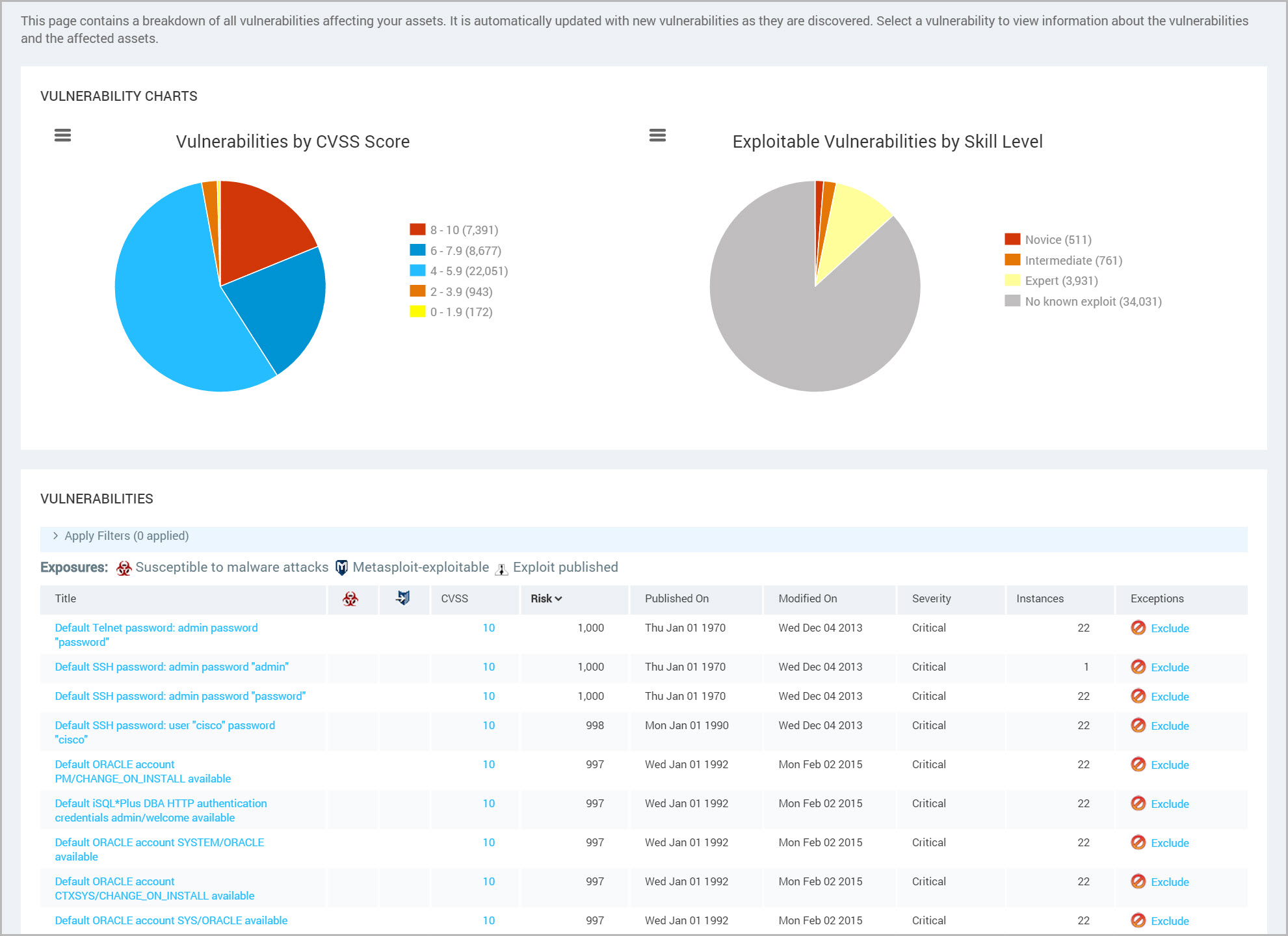
Working With Vulnerabilities .

How To Measure Performance In Vulnerability Management Rsa .
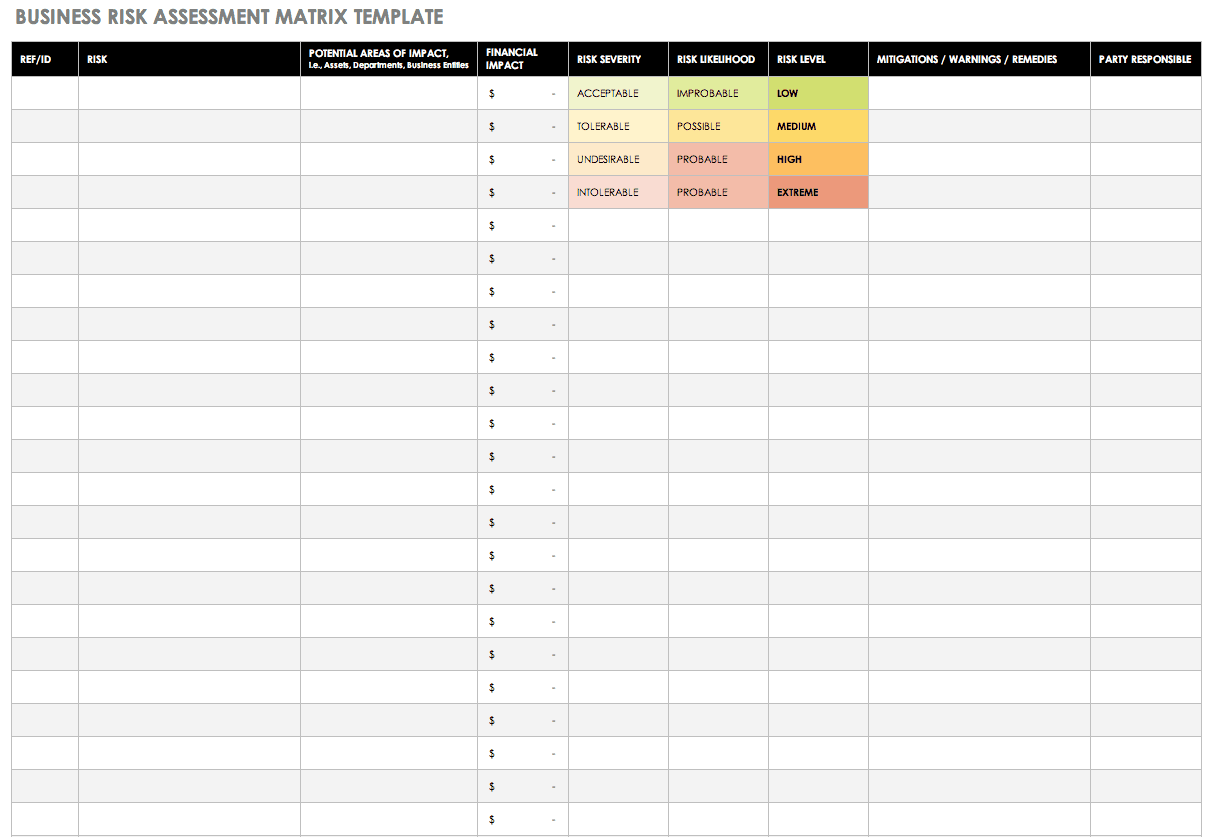
Free Risk Assessment Matrix Templates Smartsheet .
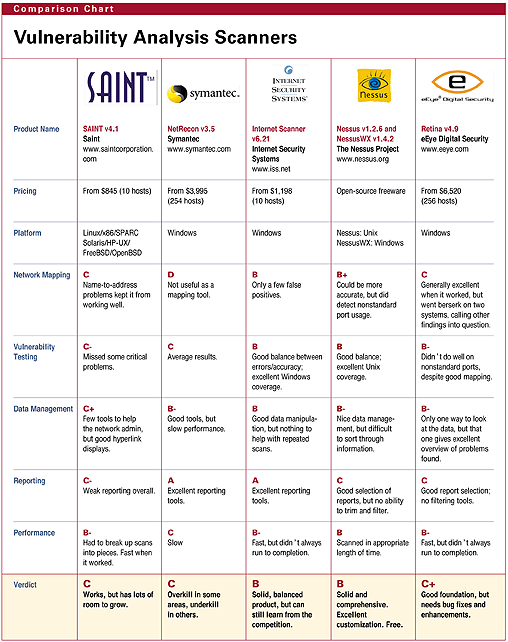
Testing And Comparing Vulnerability Analysis Tools .
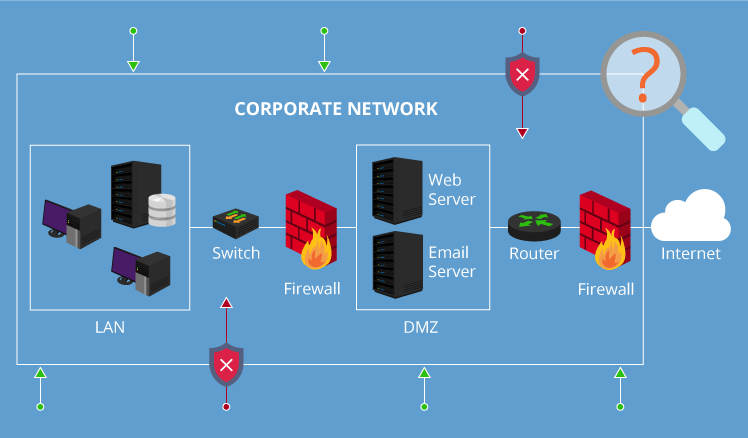
A Complete Guide To Network Vulnerability Assessment .

Risk Assessment Wikipedia .
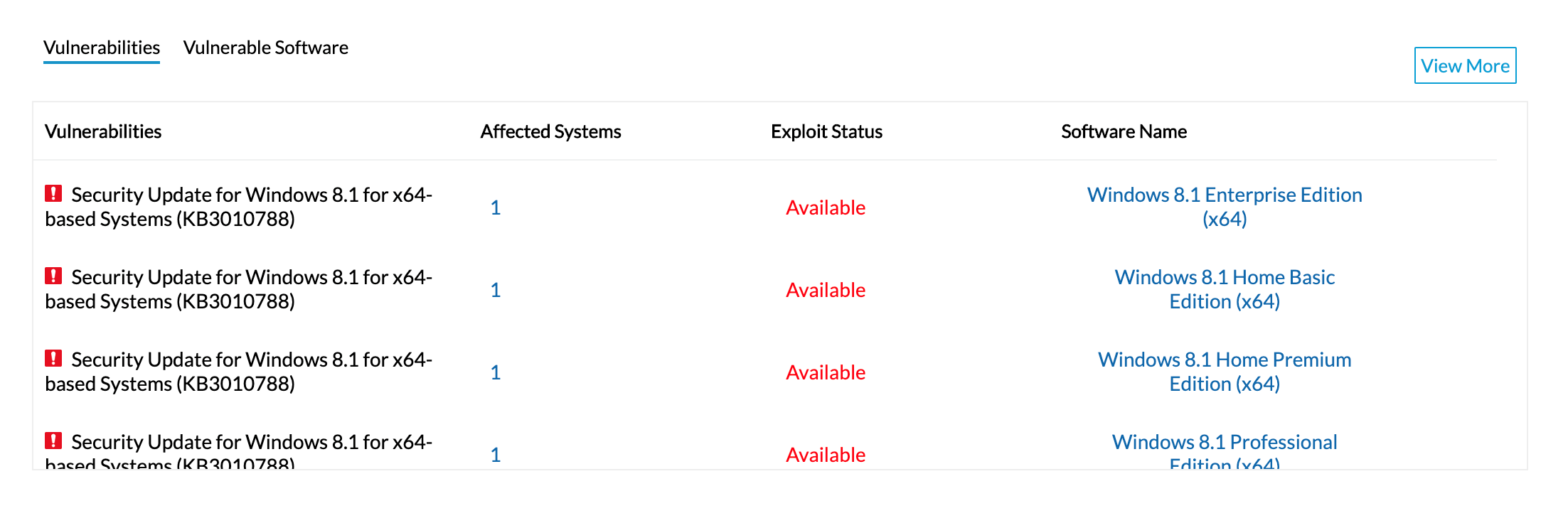
What Is A Vulnerability Assessment Vulnerability .
A Spatial Vulnerability Analysis Of Multi Hazard Threat In .

Flowchart Of Seismic Vulnerability Analysis Of Bridges .

Vulnerability Group And Vulnerable Item States Servicenow Docs .

Vaccp Haccp For Vulnerability Assessments 2016 02 17 .

Crypto Market Remains Vulnerable Litecoin Ltc Bch Trx Ada .

Vulnerability Notification Microsoft Office Graph Chart Out .
Analysis Framework Of Network Security Situational Awareness .

Chart Android Is The Most Vulnerable Operating System .

Socio Ecological Vulnerability Assessment And Coping .
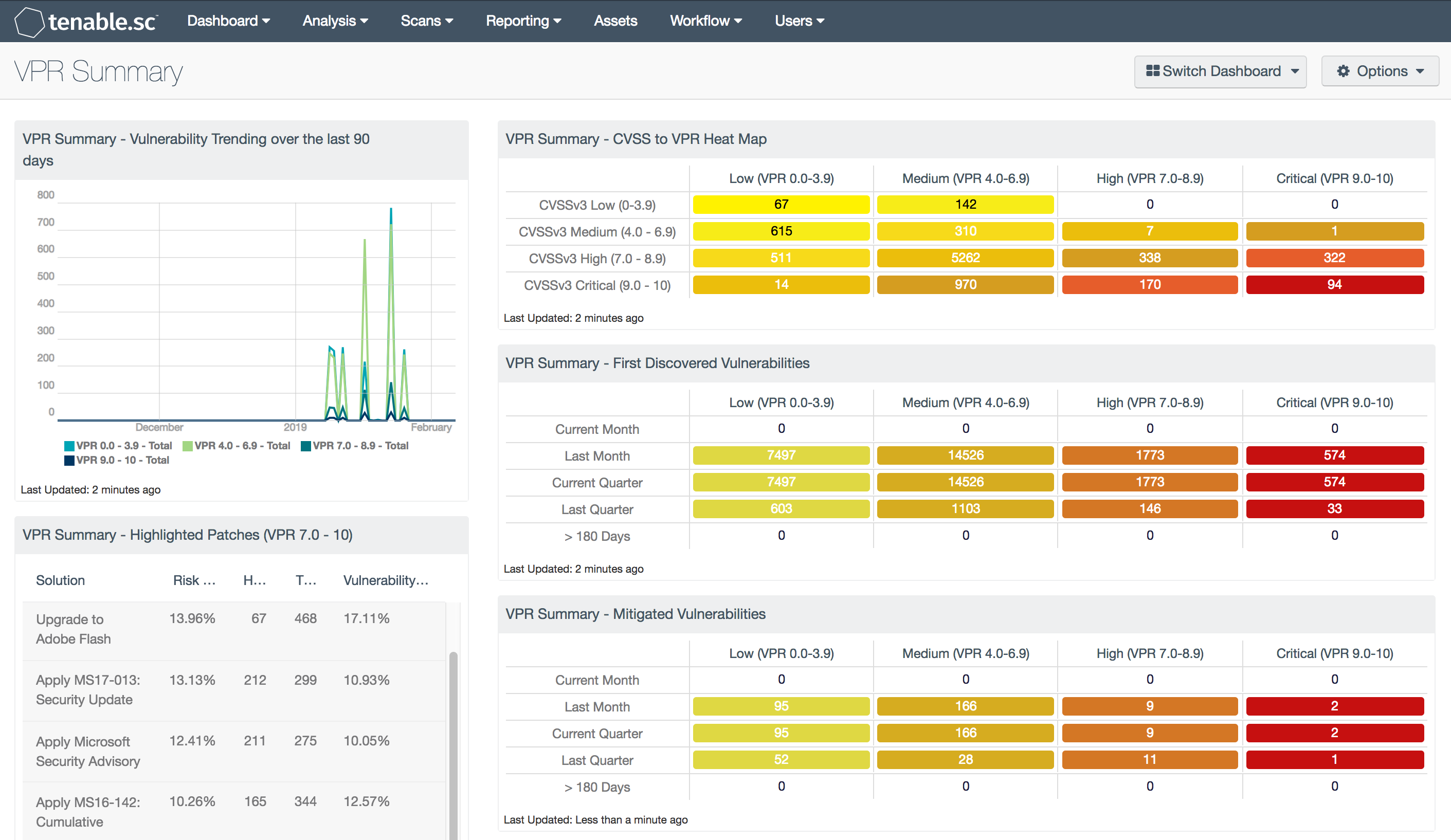
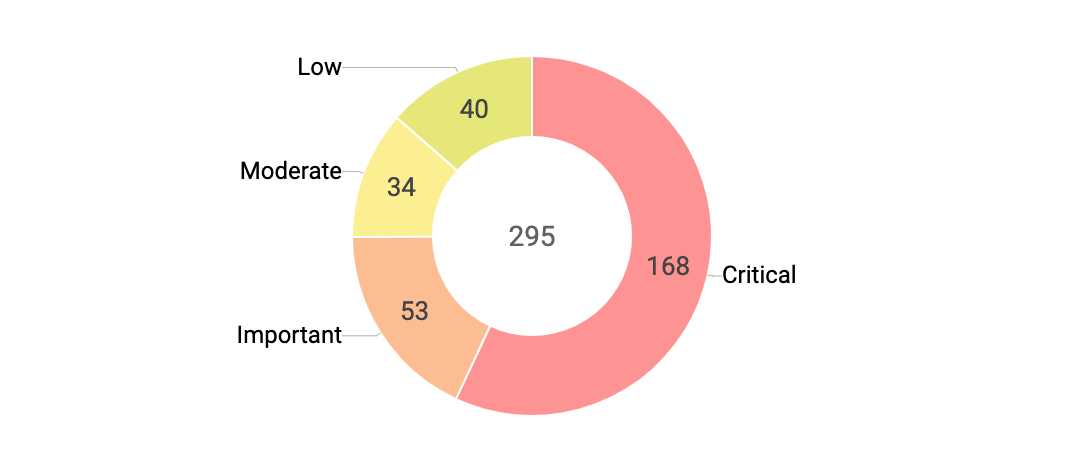
Vulnerability Priority Rating Vpr Summary Sc Dashboard .
Vulnerability Management In Dependencies In Ci Cd .
- jack singer concert hall seating chart
- keybank state theater seating chart
- step chart without date
- boot insulation chart
- cognitive functions chart
- stacked area chart power bi
- rays field seating chart
- hexadecimal chart
- 1 5 16 unf thread chart
- images of guitar chords chart
- gnp comparison chart
- what to eat chart
- chinese birth chart boy or girl calculator
- jordan chart 1 23
- run chart quality
- aloha stadium seating chart bruno mars
- bazi chart 2017
- virginia theater champaign illinois seating chart
- baby thermometer temperature chart
- cosmic intelligence agency free chart
- steel bar weight chart
- pa refund cycle chart
- nuwave oven pro plus cooking chart
- burger king nutrition chart
- what is a synoptic weather chart
- sandisk video capacity chart
- wilson youth poly warp knit baseball pant size chart
- princess of wales seating chart
- vallejo model color conversion chart
- led zeppelin singles chart history