Unix Permissions Chart - How To Use Unix File Permissions To Increase Security
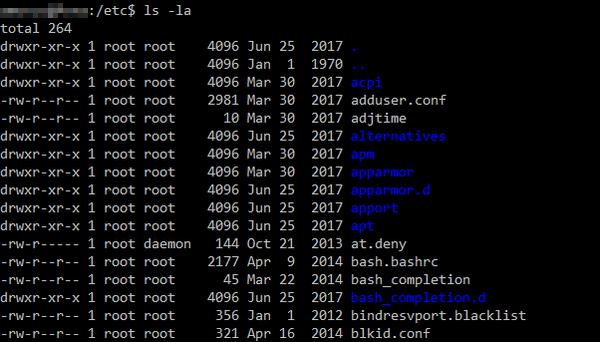
How To Use Unix File Permissions To Increase Security

A Unix And Linux Permissions Primer Daniel Miessler .
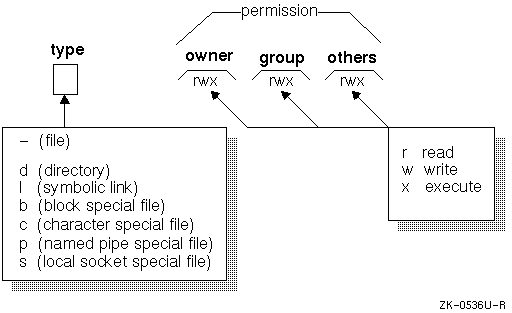
Unix Permissions .

Execute Vs Read Bit How Do Directory Permissions In Linux .
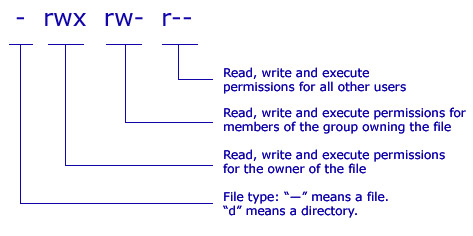
Unix Linux Os X File Permissions .
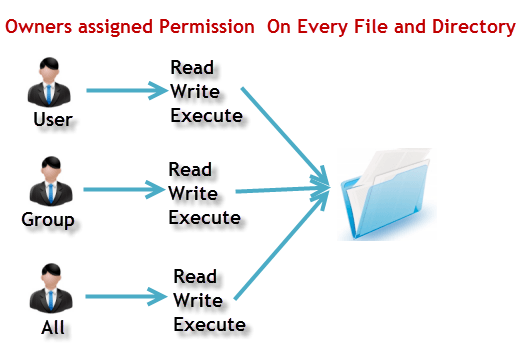
File Permissions In Linux Unix With Example .

Chmod Wikipedia .
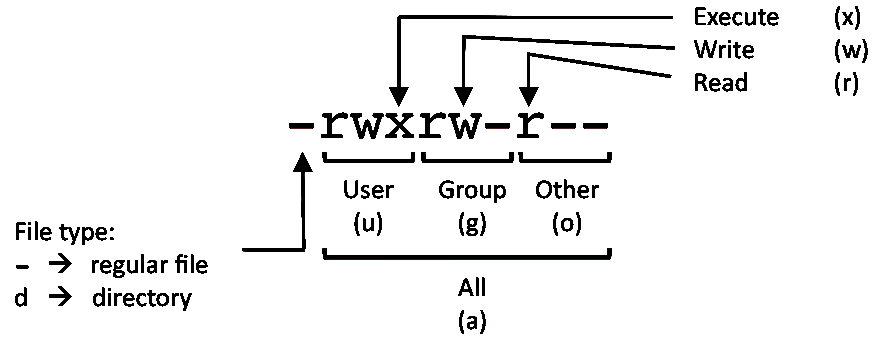
Linux Commands Cheat Sheet Linux Training Academy .
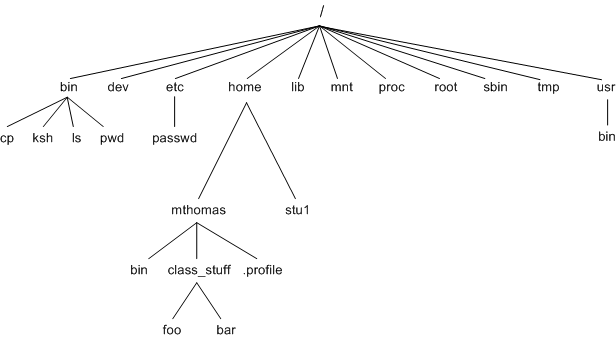
The Unix File System .
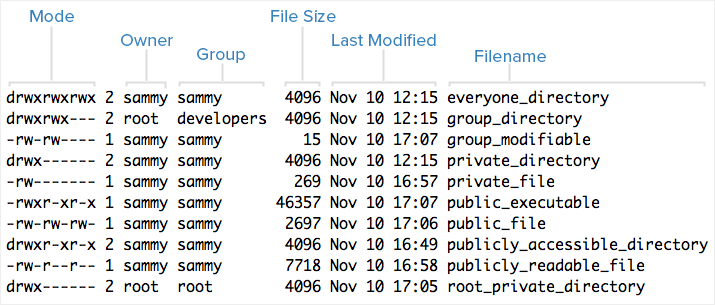
An Introduction To Linux Permissions Digitalocean .

19b Permissions .

19b Permissions .
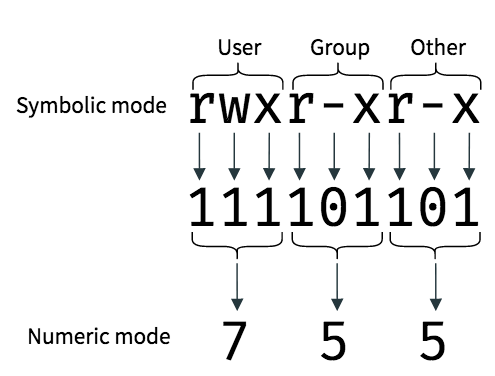
An Introduction To Linux File Permissions Boolean World .
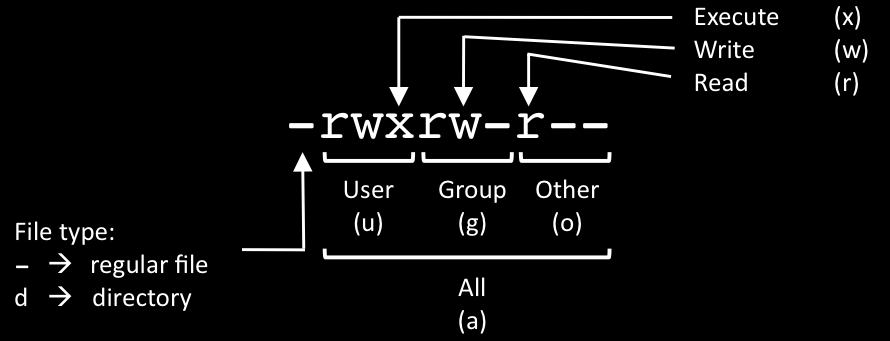
Chmod Cheat Sheet Dan Flood .

How To Use Unix File Permissions To Increase Security .
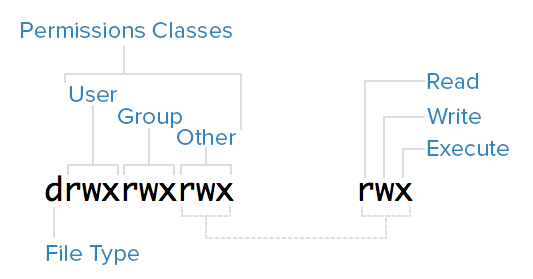
An Introduction To Linux Permissions Digitalocean .
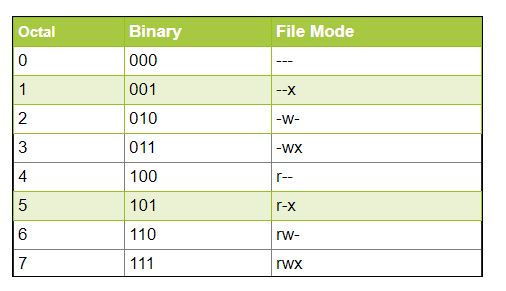
Permissions In Linux Geeksforgeeks .
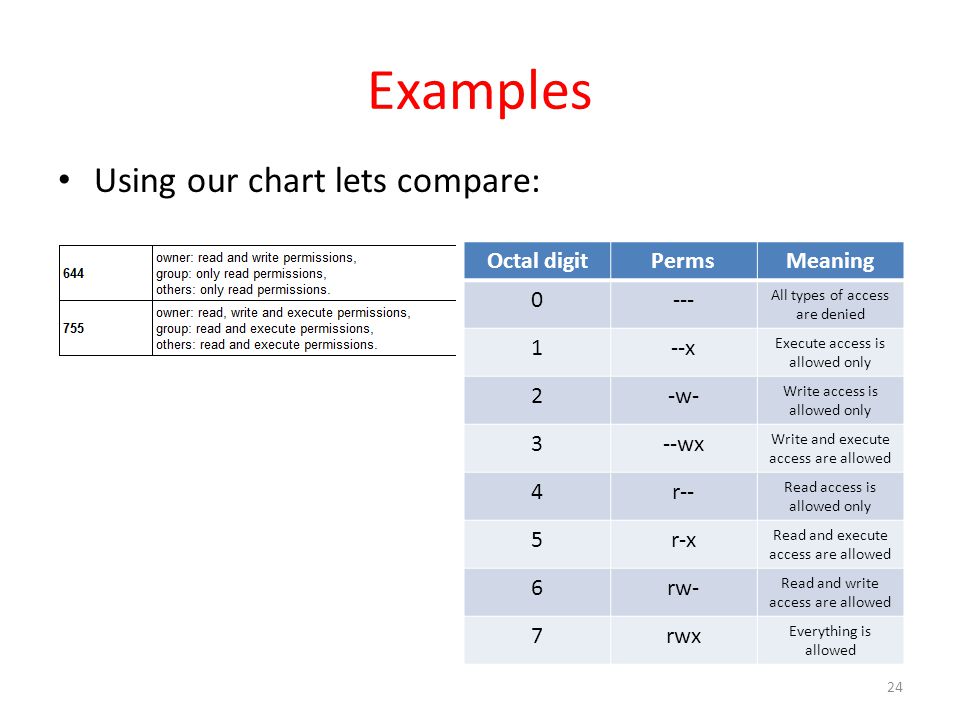
Workbook 4 File Ownerships And Permissions Ppt Video .

19b Permissions .
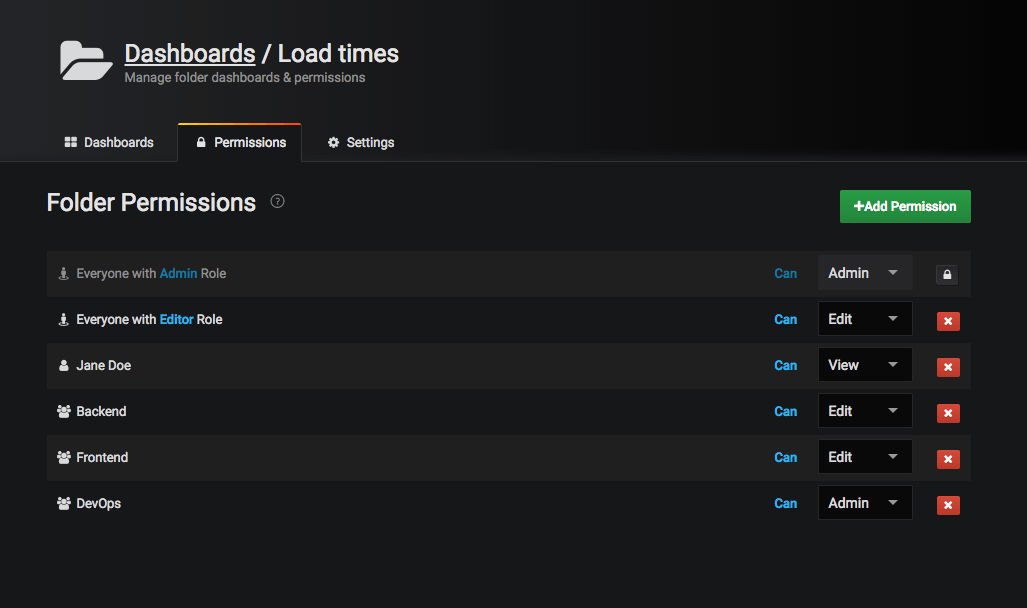
Dashboard And Folder Permissions Grafana Labs .

Whats An Uppercase T At The End Of Unix Permissions .

Goals Infocloud Technologies Samba Installation In Aix .
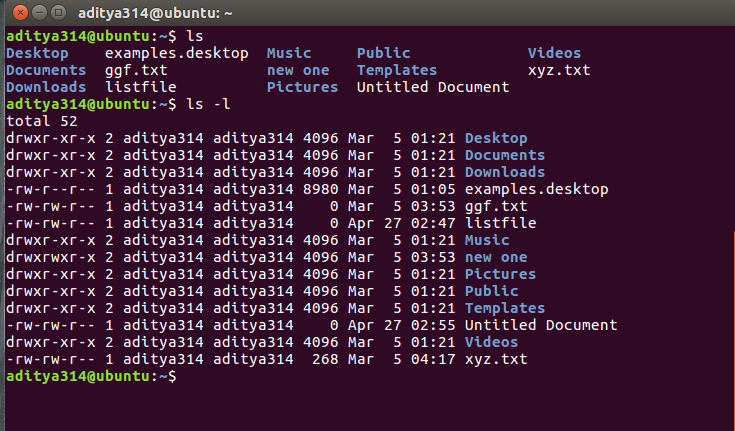
Permissions In Linux Geeksforgeeks .

Whats An Uppercase T At The End Of Unix Permissions .
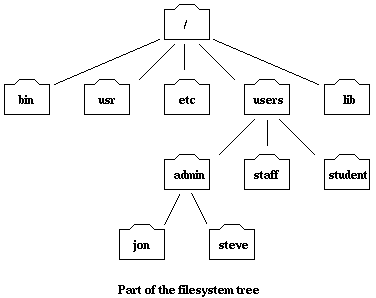
Working With Files And Directories .
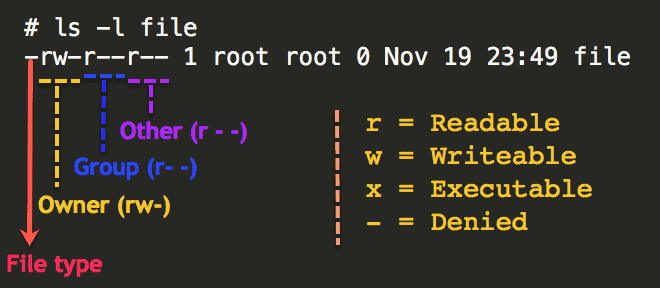
Understanding Basic File Permissions And Ownership In Linux .

Roles And Permissions Solution Manager Community Wiki .
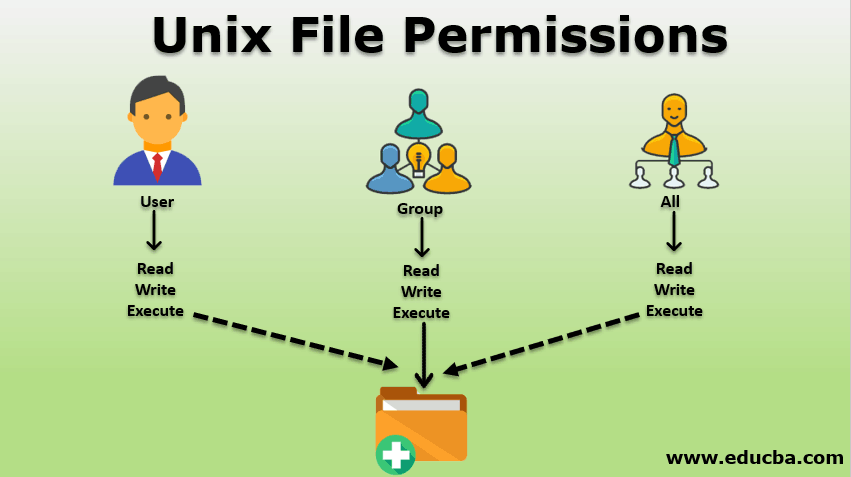
Unix File Permissions Guide To Unix File Permissions With .

Unix Security .

Are Selinux Rules Enforced Before Or After Standard Linux .

Export Mongodb Charts Stack Overflow .
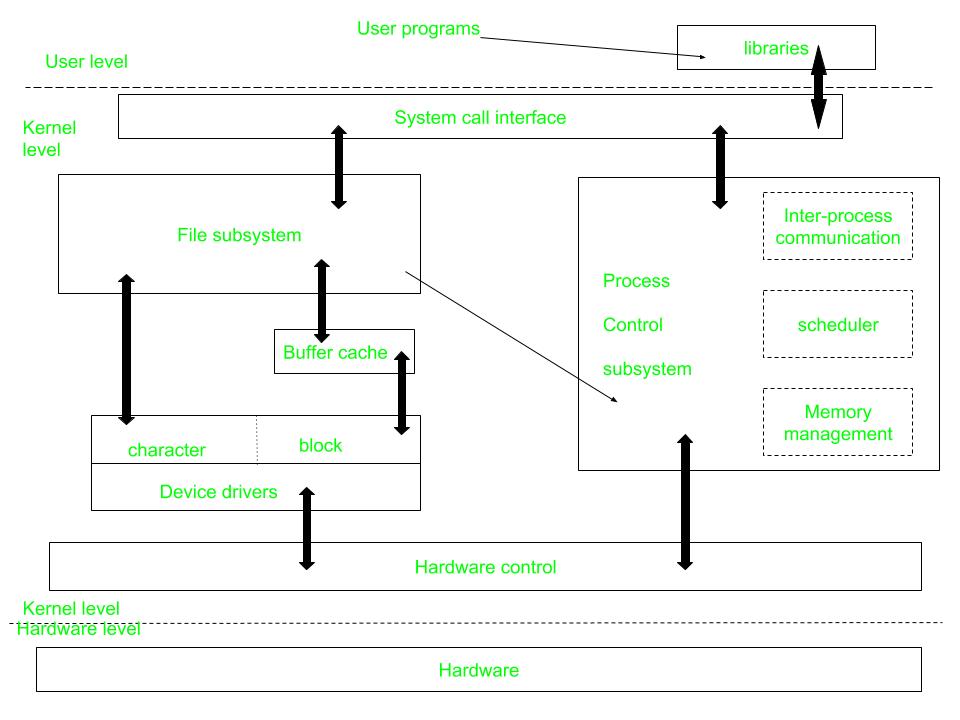
Introduction To Unix System Geeksforgeeks .
.png)
File Permissions In Linux Unix With Example .

19b Permissions .

Unix Chart Wallpaper Computer Wallpapers 14838 .
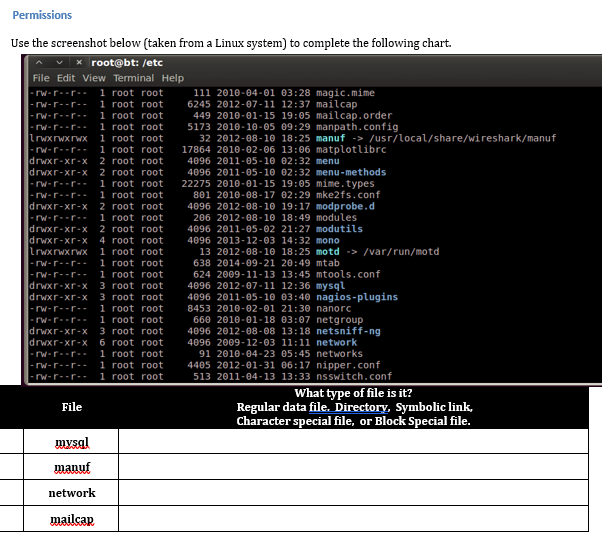
Solved Permissions Use The Screenshot Below Taken From A .
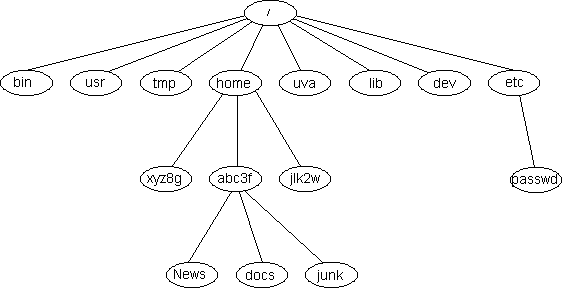
Unix Command Syntax .
Chartio Faqs Modifying Time In Chartio Tips And Tricks .
How To Use Unix File Permissions To Increase Security .

Filter Documents In The Visualization Charts Manual 0 10 .

58 Competent Linux Commands Chart .
How To Manage Access Control Lists With Ansible Opensource Com .

Structures Of Directory In Operating System Geeksforgeeks .

19b Permissions .

Structures Of Directory In Operating System Geeksforgeeks .
Getting To Know Linux File Permissions Linux Com .
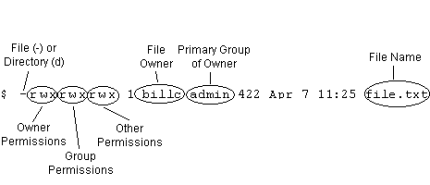
Understanding Unix And Nfs Permissions .
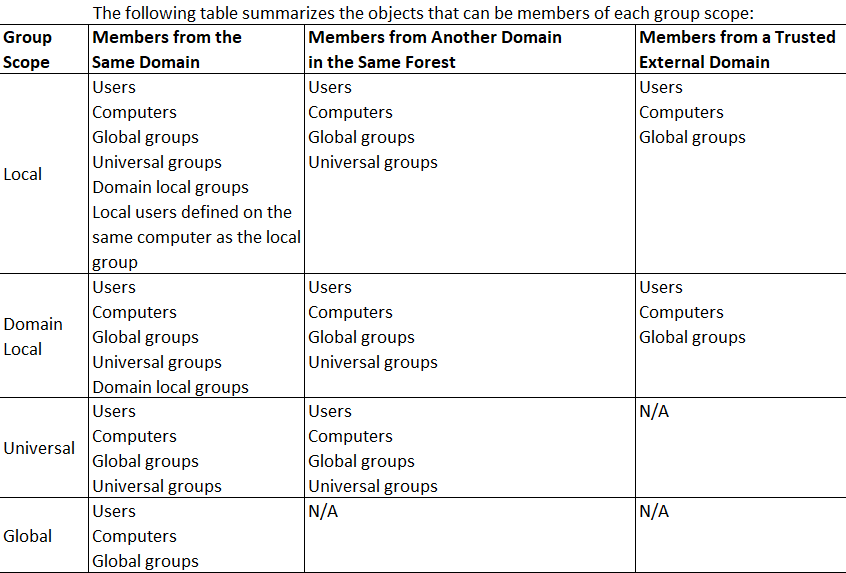
Active Directory Group Management Best Practices .
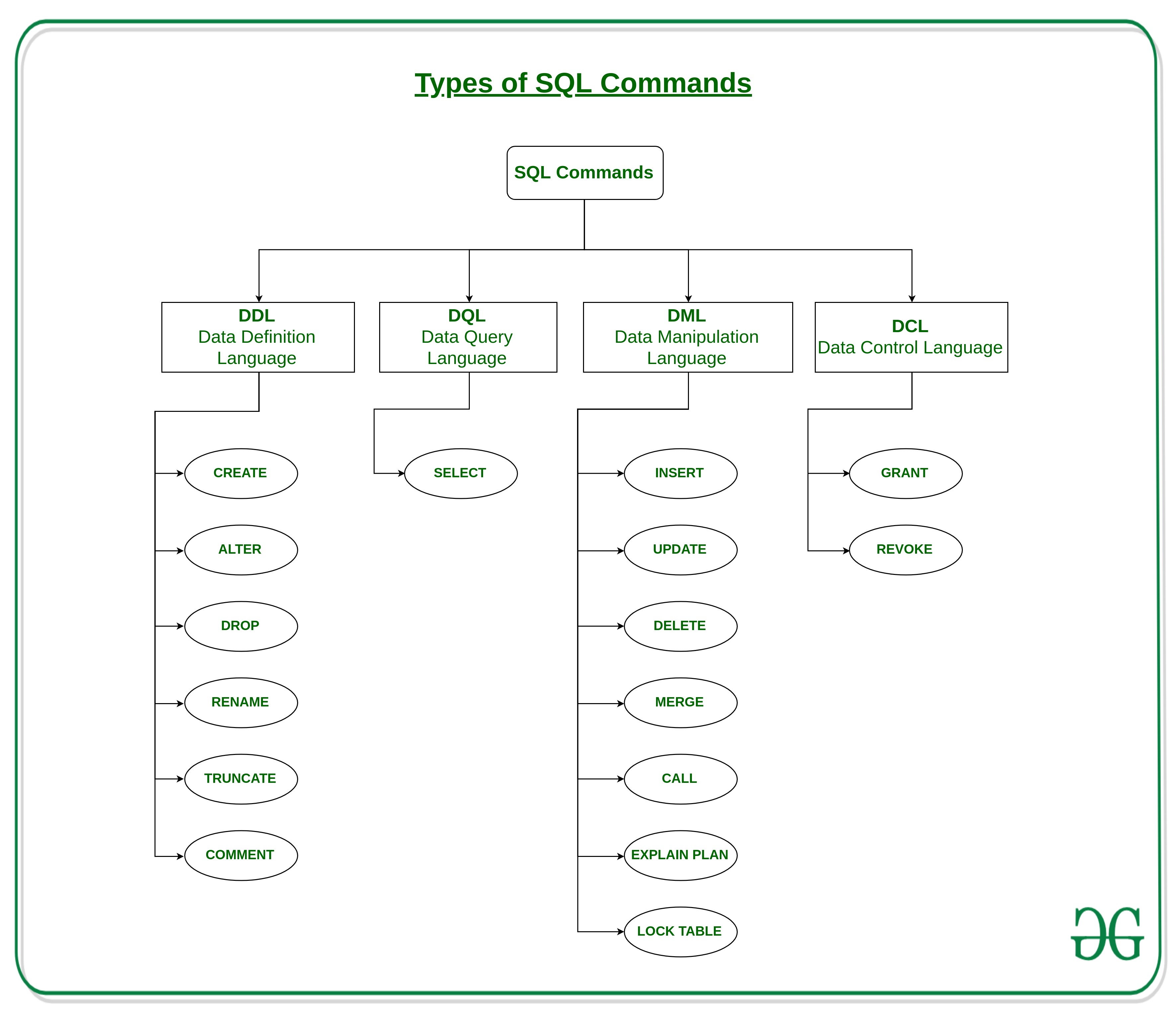
Sql Ddl Dql Dml Dcl And Tcl Commands Geeksforgeeks .

Pin By Kalevi Lindroos On Linux In 2019 Linux Kernel .
- hemoglobin a1c blood sugar conversion chart
- perfect pushup schedule chart
- drakes pride d tec bias chart
- clarinet transposition chart
- uk denim size chart
- siberian tiger population chart
- boeing 767 jet seating chart
- ricci foundation colour chart
- naturino toddler shoes size chart
- victoria secret slipper size chart
- guinea pig space chart
- uk singles charts 1960s
- 10k lull load chart
- babysitting pay chart
- how to create pyramid chart in excel 2016
- structure chart in software engineering ppt
- common childhood illnesses signs and symptoms chart
- beef roast doneness chart
- how to create an organizational chart in microsoft word 2007
- paypal chart
- kohls size chart womens
- tenses rules chart in english
- copper wire trolling depth chart
- excel 2010 create chart from selected cells
- excel chart number format millions
- color wheel chart mixing colors
- size chart in euro
- reading genre chart
- excel gauge chart template download
- 2011 ram 3500 towing capacity chart
