Prevent Cyber Attacks 10 Methods To Shield Your Digital Assets - The Top Iot Attack Vectors How Hackers Exploit Vulnerabilities
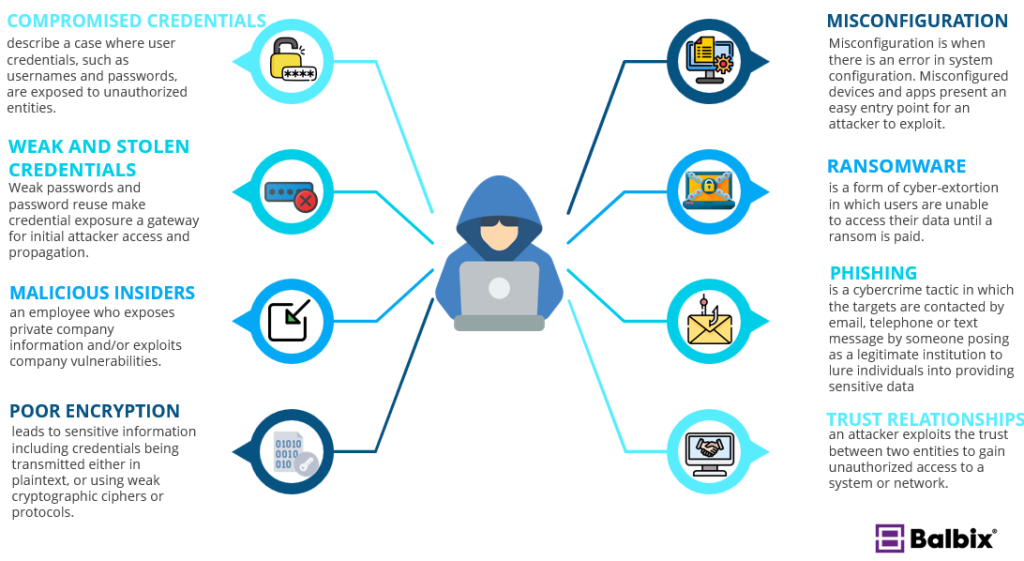
The Top Iot Attack Vectors How Hackers Exploit Vulnerabilities
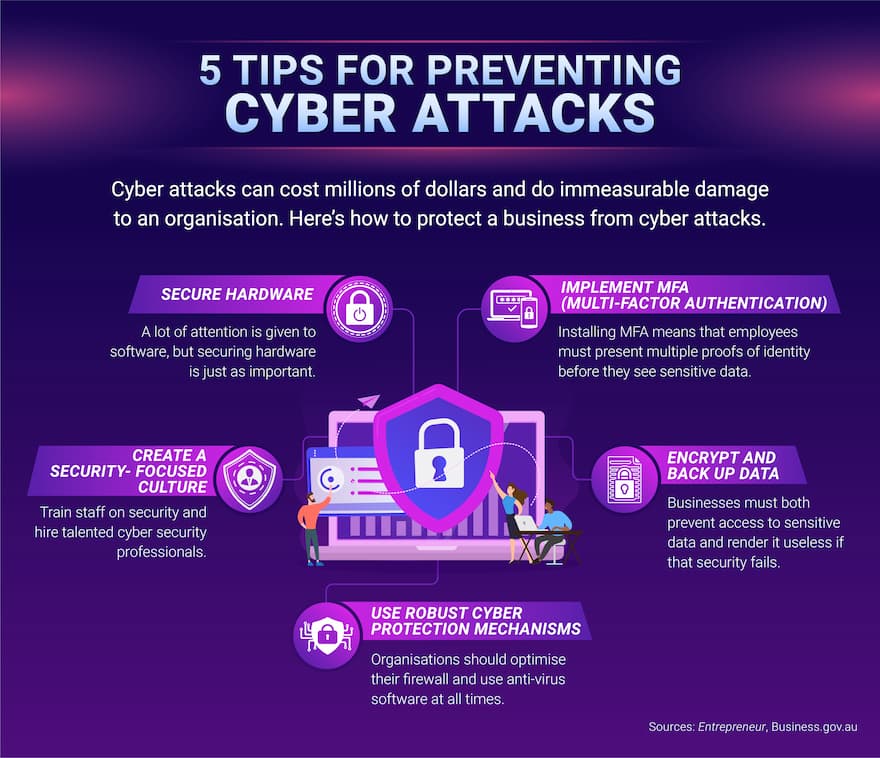
Cyber Attacks Tips For Protecting Your Organisation Ecu Online .
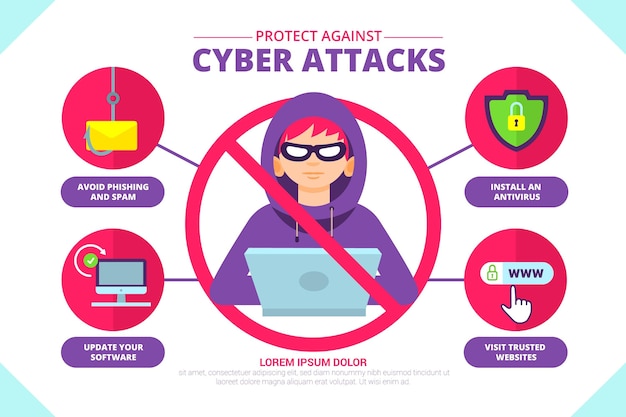
Protect Against Cyber Attacks Infographic Free Vector .

Free Vector Protect Against Cyber Attacks Infographic .
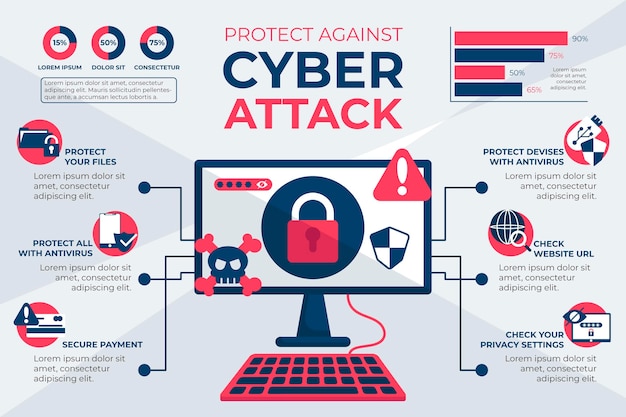
Premium Vector Protect Against Cyber Attacks Infographic .

Tips To Protect Your Business From Cyber Attacks .
7 Important Steps To Cyber Crime Prevention For Businesses .
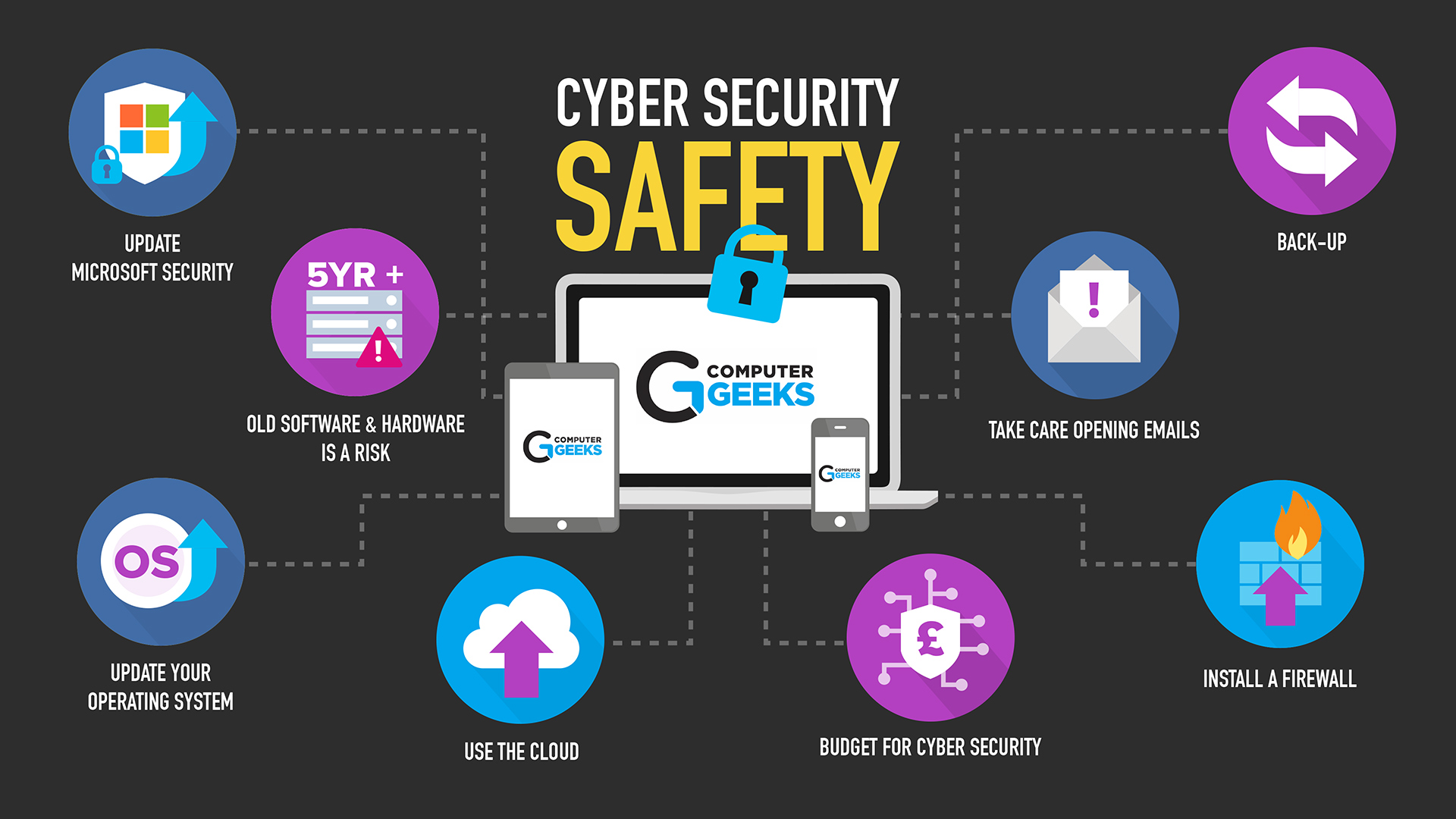
10 Facts Cyber Attack Statistics And Trends In New York Nyc .

Perché è Importante Prevenire Il Crimine Informatico Techarex Net .

6 Ways To Protect Yourself Against Cyber Attacks .
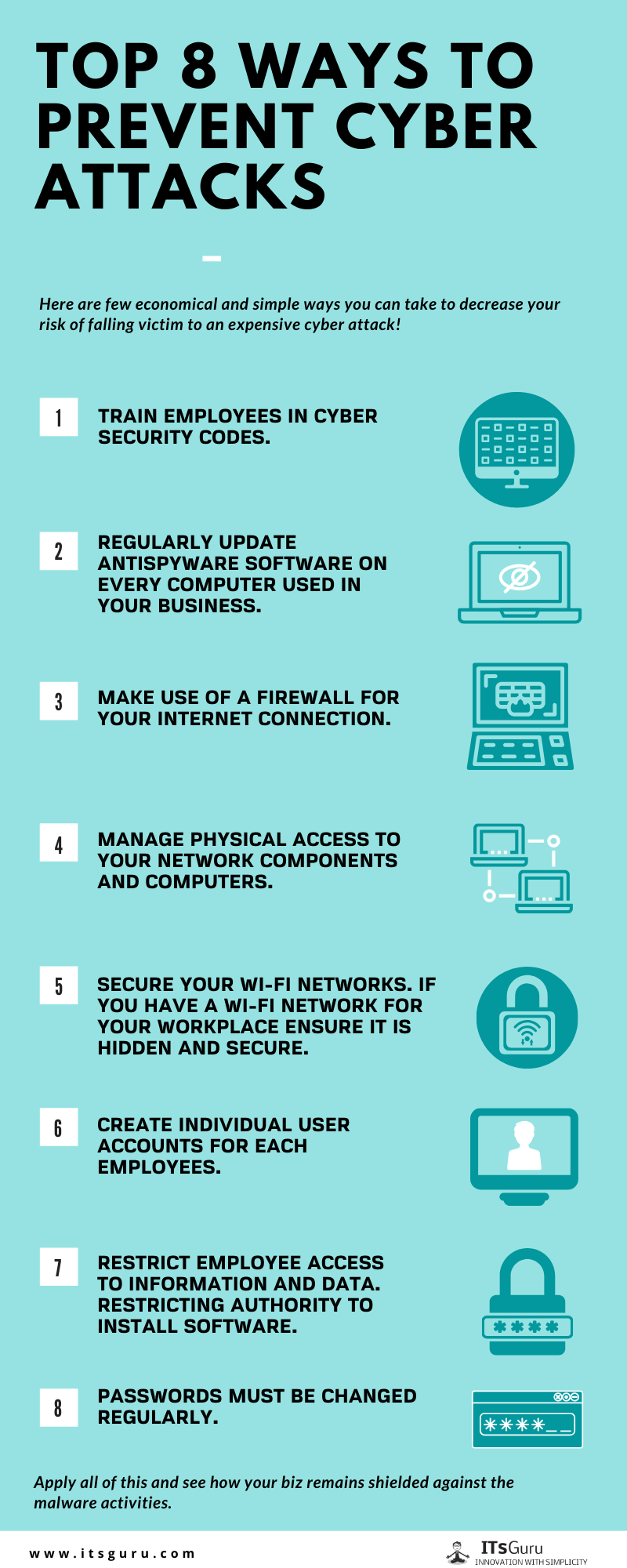
Top 8 Ways To Prevent Cyber Attacks .
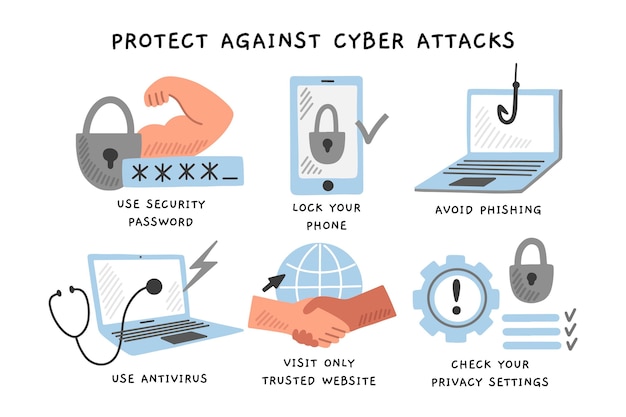
Protect Against Cyber Attacks Infographic Free Vector .

How To Prevent Small Business Cyber Attacks In 2023 .

Prevent Cyber Attacks 10 Methods To Shield Your Digital Assets .

Download Protect Against Cyber Attacks Infographic For Free In 2020 .
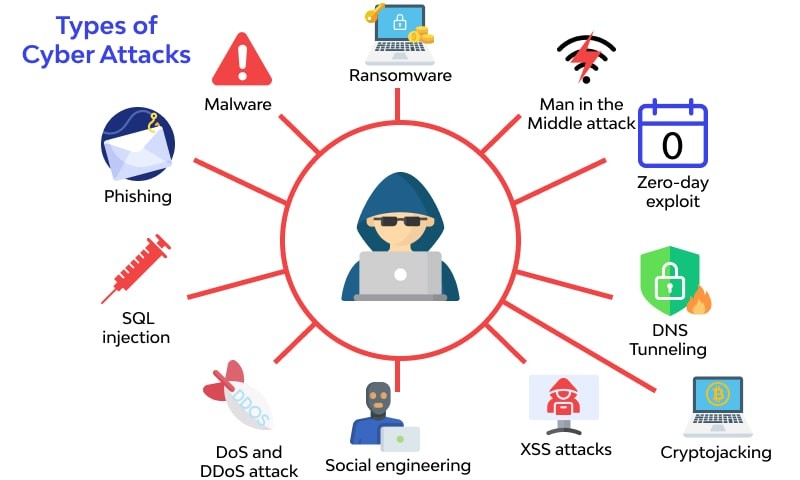
Cyber Security Attacks .
How To Prevent Cyber Attacks And Threats Purplesec Png .

How To Protect Yourself From Cyber Attacks Geeksforgeeks .
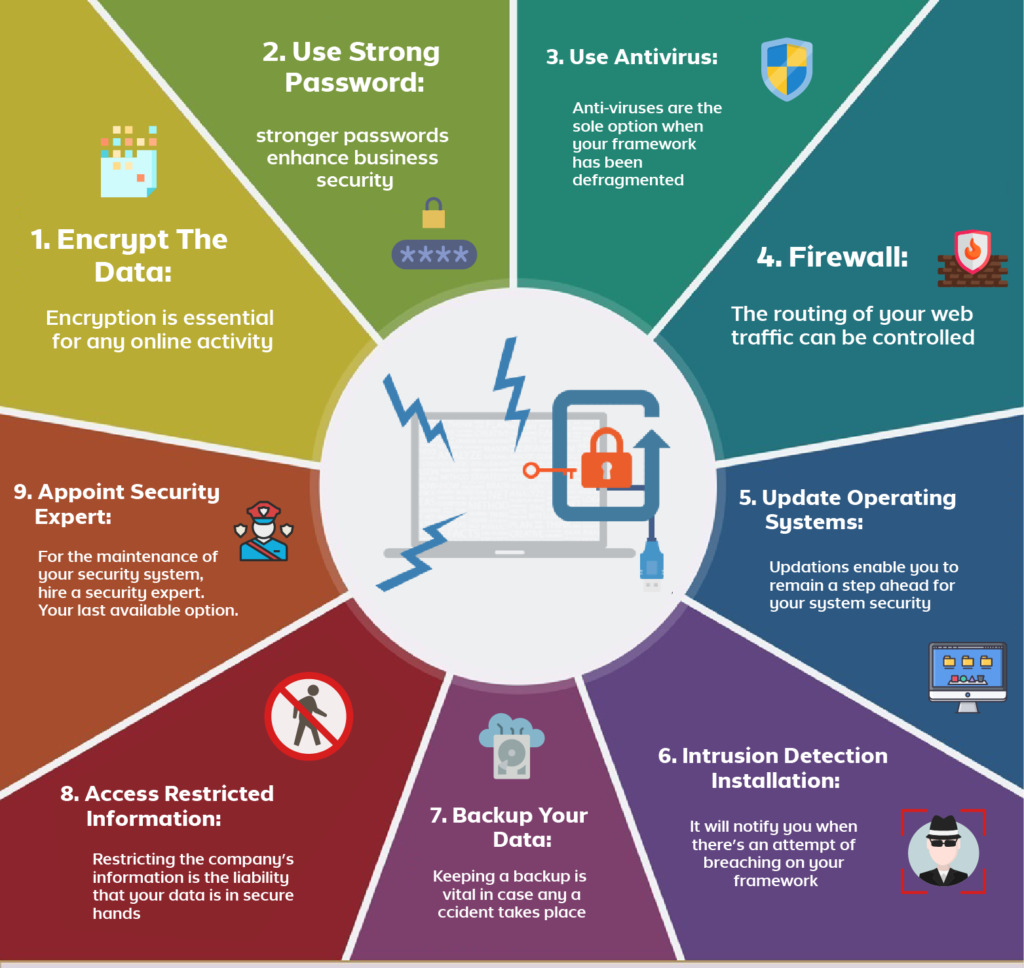
Two Main Ways To Protect Your Computer From Viruses Psadoservers .

Techbytes Blog .

Six Ways To Protect Yourself Against Cyber Attacks .

Ways To Prevent Cyber Attack That May Hinder Business Growth .

Cyber Attacks In India Iasbaba .

How To Protect Against Cyber Attacks .

Types Of Attacks In Cyber Security Powerpoint Slides Diagrams Rainy .

Common Cyber Attacks And Ways To Prevent Them .
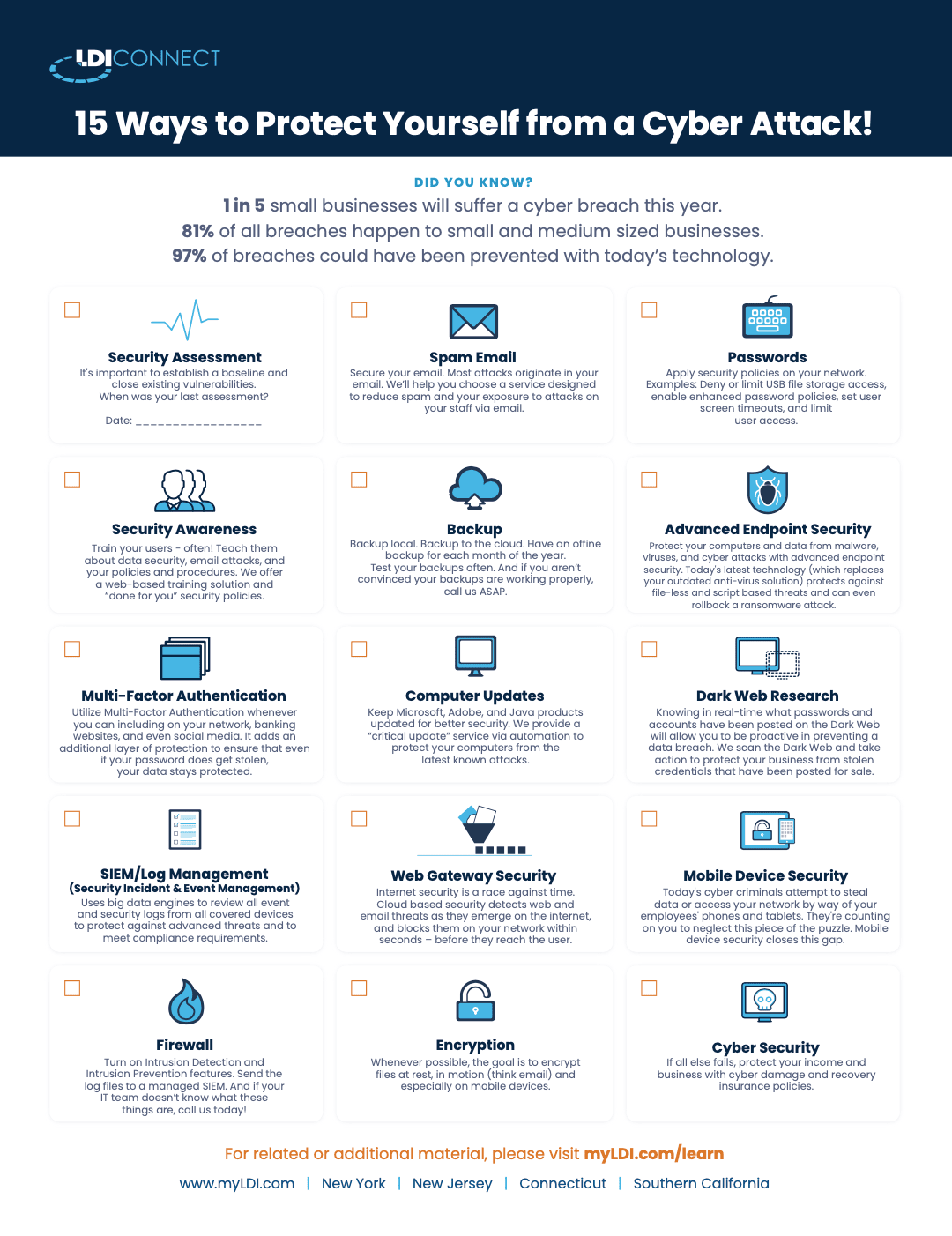
15 Ways To Protect Yourself From A Cyber Attack .
Msmes Save Their Data From Cyber Attacks .

How To Prevent Cyber Attacks In 2024 10 Effective Steps .

Premium Vector Protect Against Cyber Attacks Infographic .
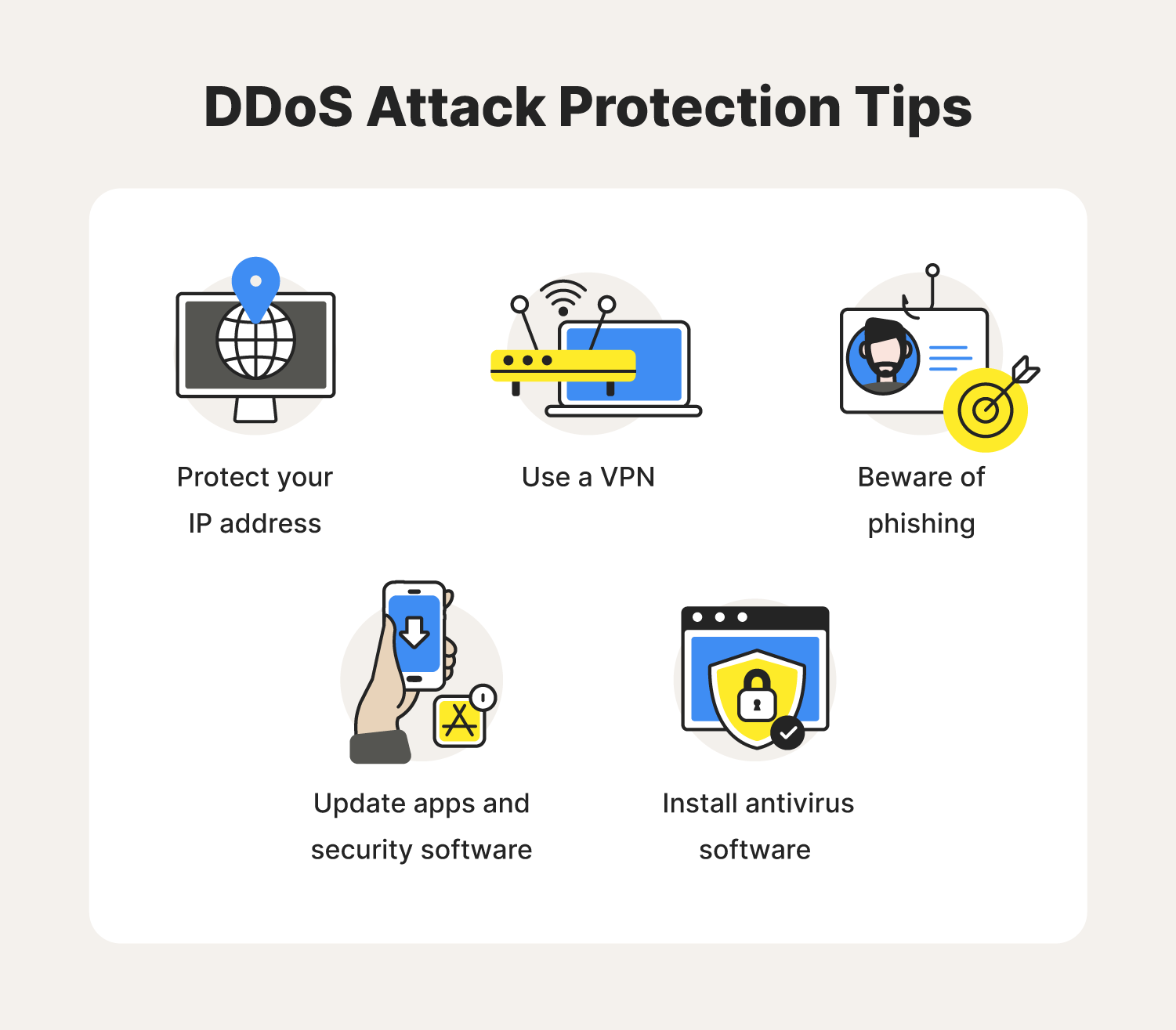
Denial Of Service Attack Dos Nedir Bulb .
Free Vector Protect Against Cyber Attacks Infographic .

Prevent .

Pin On Digital Marketing .
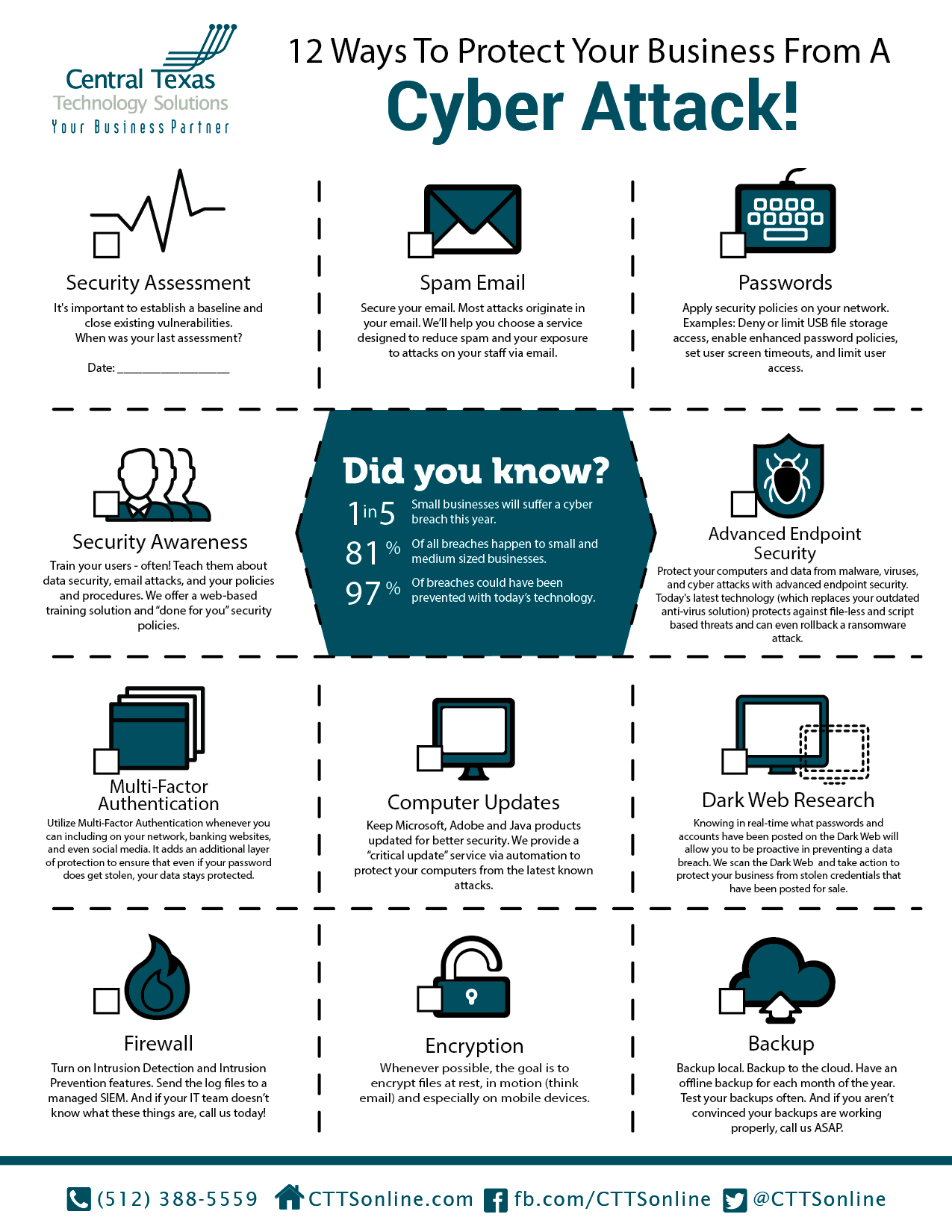
12 Ways To Protect Your Business From A Cyber Attack Ctts Inc .
Name The Cyber Attacks Itensure .

10 Ways To Prevent A Cyber Attack Kbi .

Cyber Warfare Research Topics Cyber Warfare Research Paper 2022 10 15 .
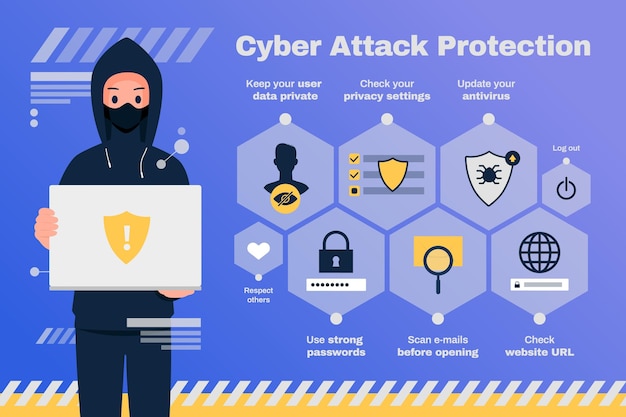
Protect Against Cyber Attacks Infographic Free Vector .

Protect Against Cyber Attacks Infographic Free Vector .
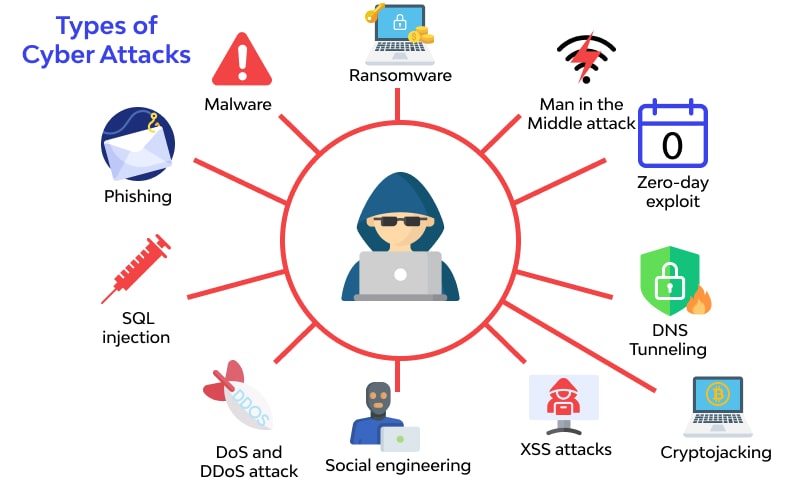
The Most Professional Cyberattack Guide You 39 D Ever Find What Are .
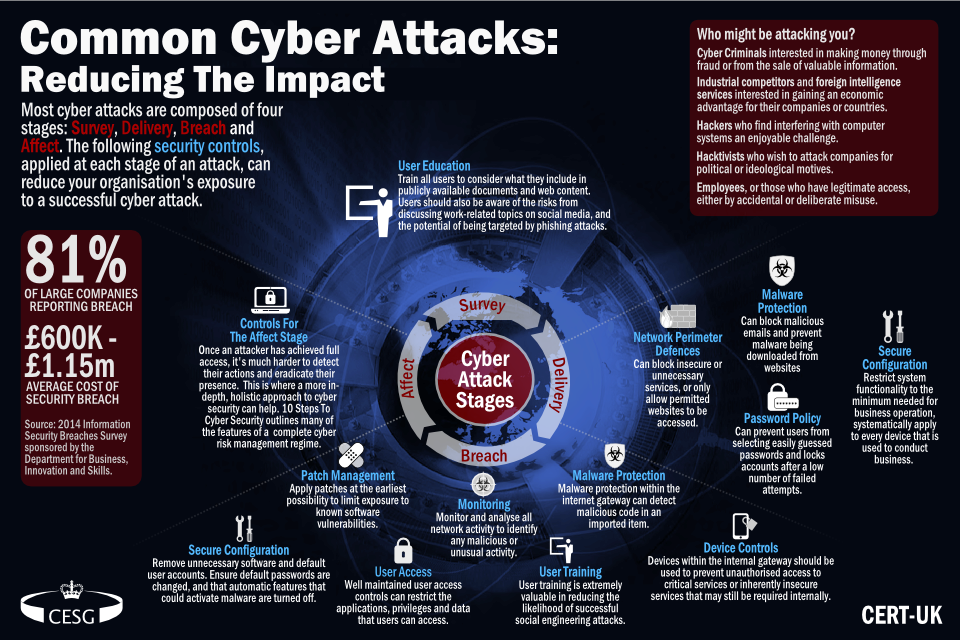
Withdrawn Common Cyber Attacks Summary Gov Uk .

Free Vector Protect Against Cyber Attacks Infographic .

The Top Iot Attack Vectors How Hackers Exploit Vulnerabilities .
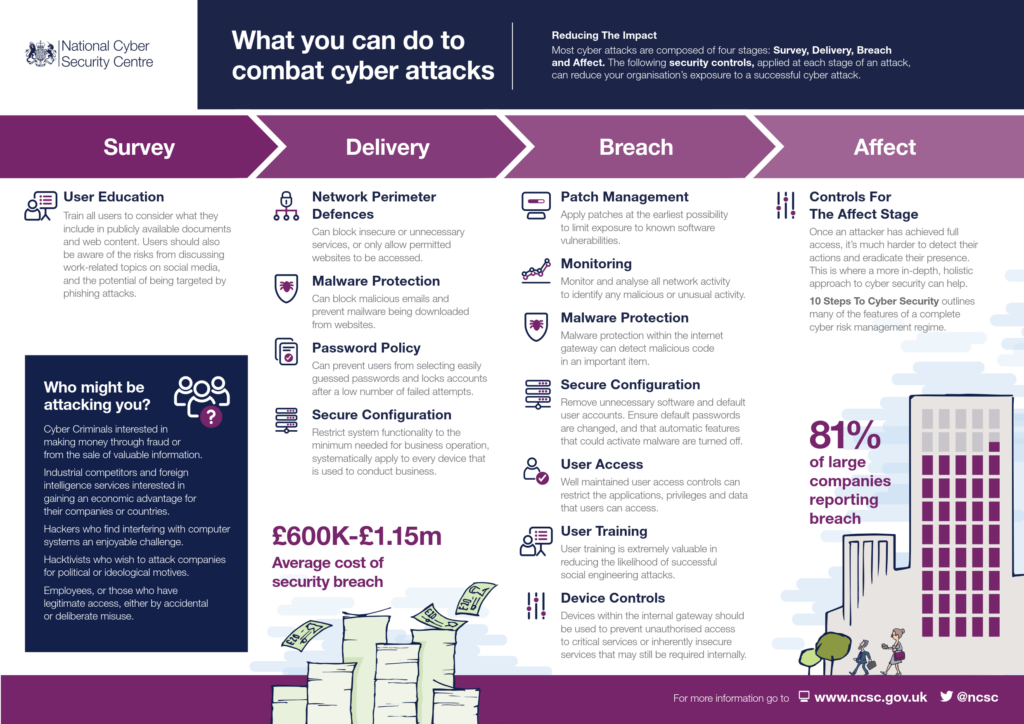
Infographic Stages Of Common Cyber Attacks Safety4sea .
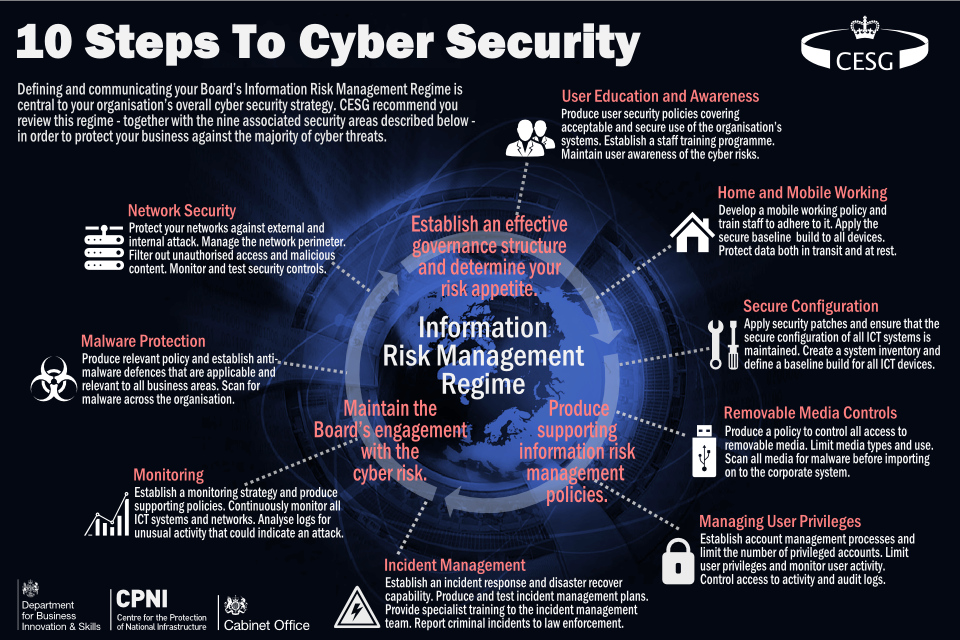
10 Steps Summary Gov Uk .
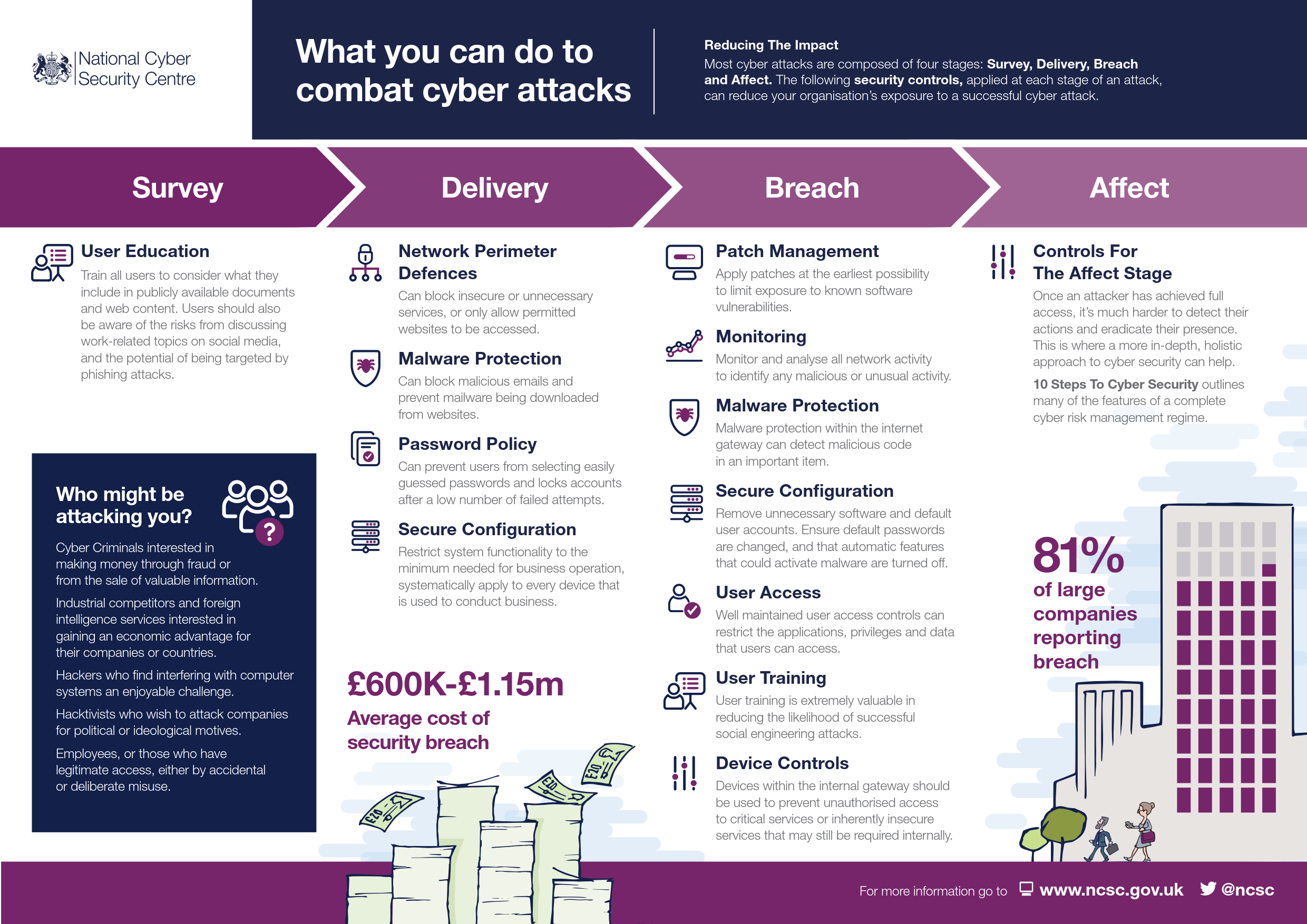
Infographic Stages Of Common Cyber Attacks Safety4sea .
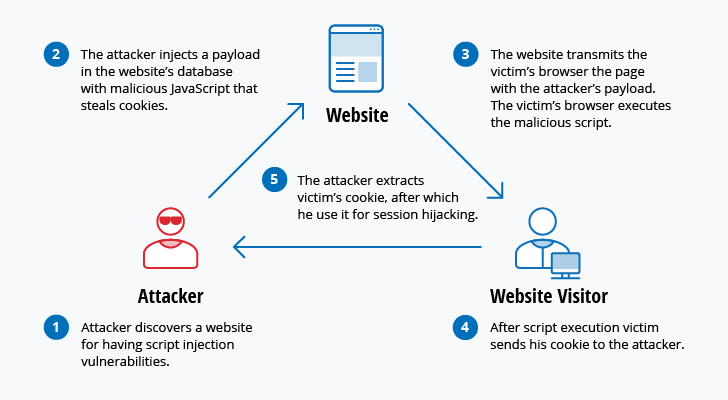
Top 10 Most Common Types Of Cyber Attacks Rhyno Cybersecurity .
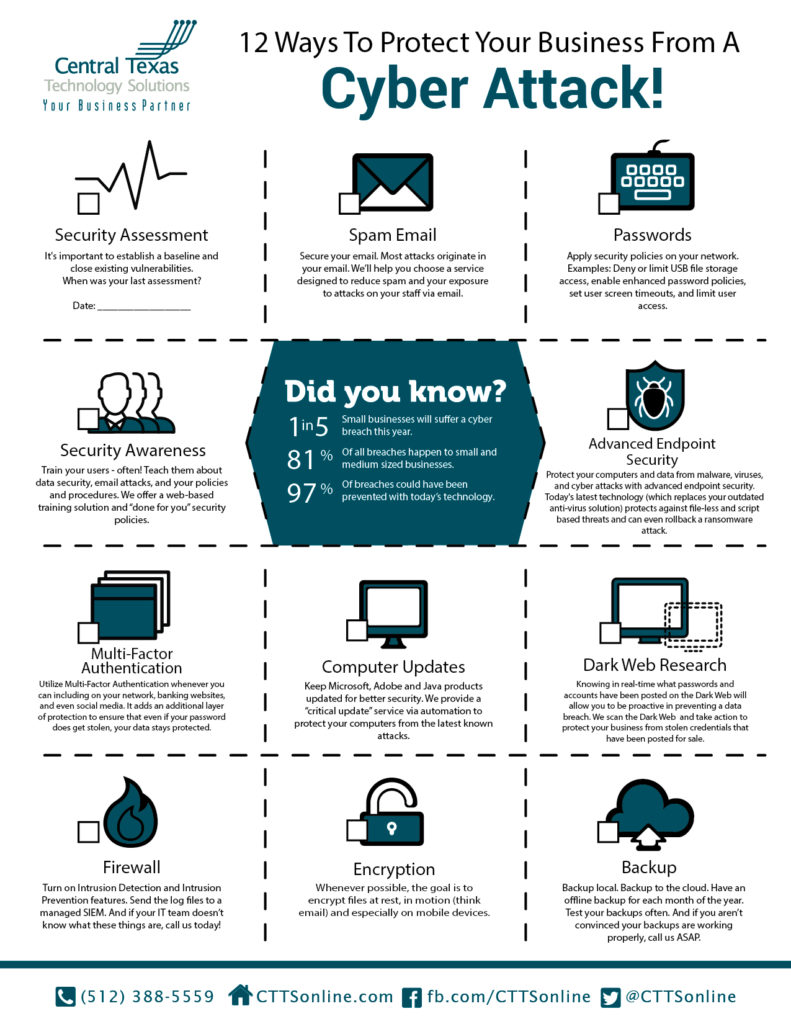
12 Ways To Protect Your Business From A Cyber Attack Ctts Inc .

The Law Society Of Northern Ireland .

Are You Cyber Secured Be Aware Of Potential Cyber Attacks Ecs .
- world religions chart worksheet answers key
- publishing process flow chart
- atlantic hurricane tracking chart
- the home buying process flow chart
- reading candlestick chart patterns
- vince camuto swimsuit size chart
- quality control chart excel
- tree chart creator
- topical antifungal comparison chart
- sample church chart of accounts
- under armour cleats size chart
- rcbs bullet molds chart
- whitetail deer movement chart
- state farm seating chart glendale
- valspar metallic paint color chart
- samsung phone comparison chart 2019
- sharpie chart markers
- ion hair toner chart
- raptors seating chart prices
- texas mortgage rates chart
- one direction buffalo seating chart
- where is chart of accounts in quickbooks
- raising cane center seating chart
- read my natal chart
- staples seating chart tool
- define run chart
- the union event center seating chart
- maryland theatre hagerstown md seating chart
- the best stock charts
- william saroyan theater seating chart