Incident Response Flow Chart - Security Orchestration Use Case Curtailing Phishing Attacks

Security Orchestration Use Case Curtailing Phishing Attacks

Incident Response Test Flow Chart Incidentcontrolroom Com .

Incident Response Flowchart Ferpa Sherpa In 2019 No .

Cybersecurity Incident Response Plan Csirp Checklist 2019 .

Incident Response Flowchart Illustrating The Course Of .

Incident Response Process Flow Chart Cyber Security News .
Generation Safe .
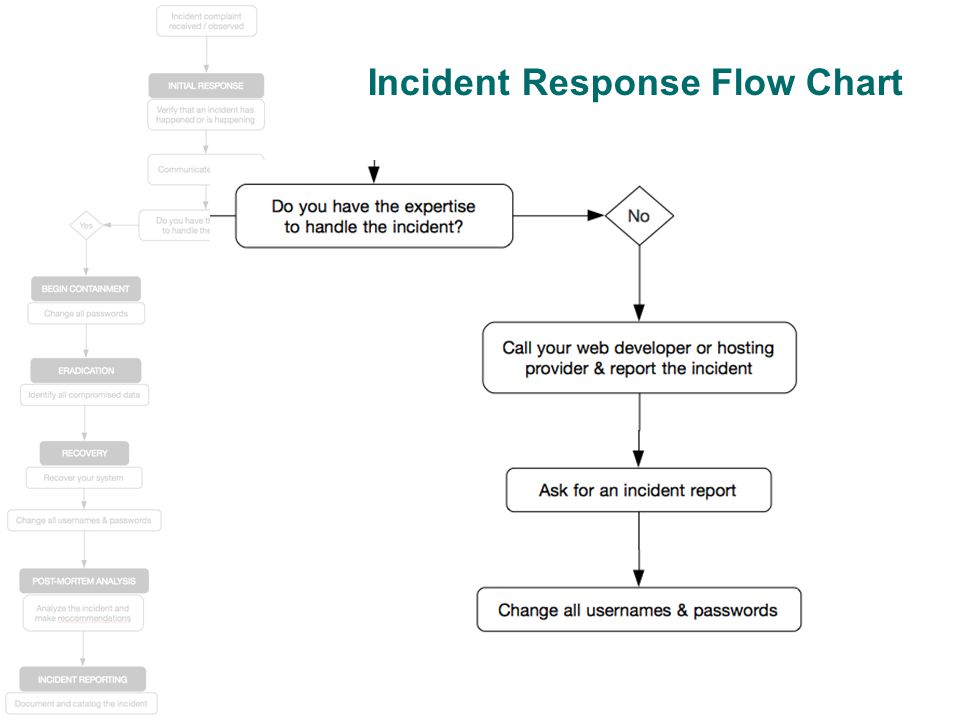
Incident Response Updated 03 20 Ppt Download .

Portland State Office Of Information Technology Computer .

Larson Security Releases Our Critical Data Classification .
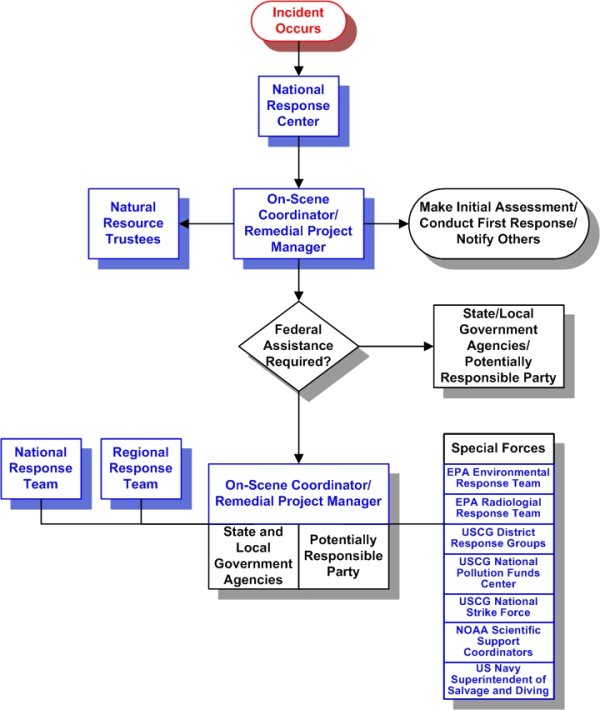
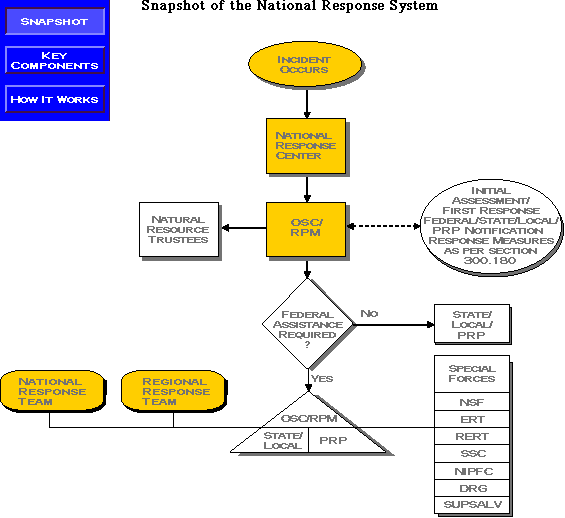
National Response System Emergency Response Us Epa .

Bias Incident Response Plan .

Security Incident Phishing Workflow Template Servicenow Docs .

1 Incident Response Timeline Or Simple Process Flow .
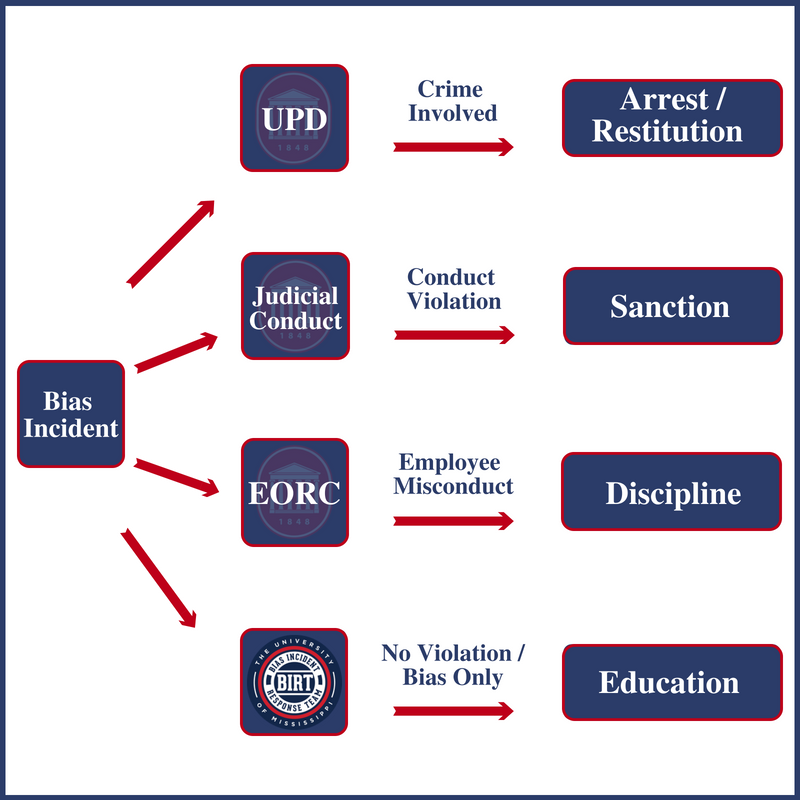
Bias Incident Response Team Reporting Bias Bias Incident .

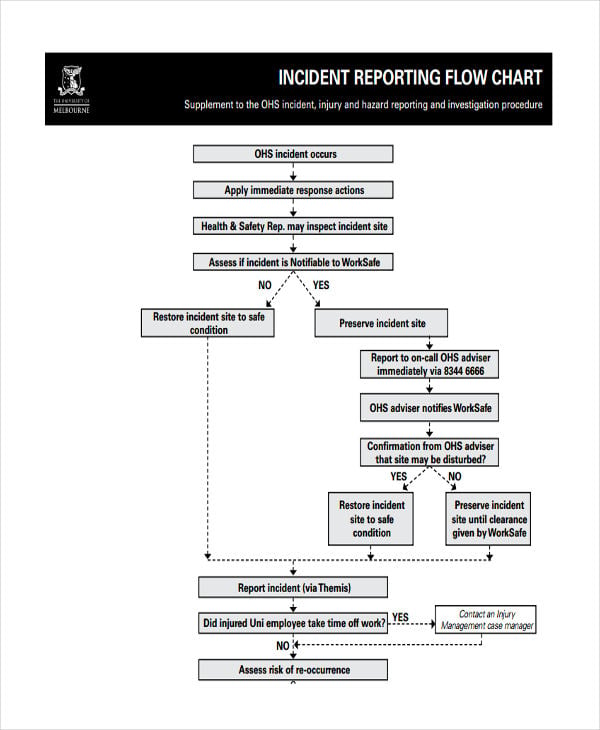
Security Incident Reporting Flow Chart Www .
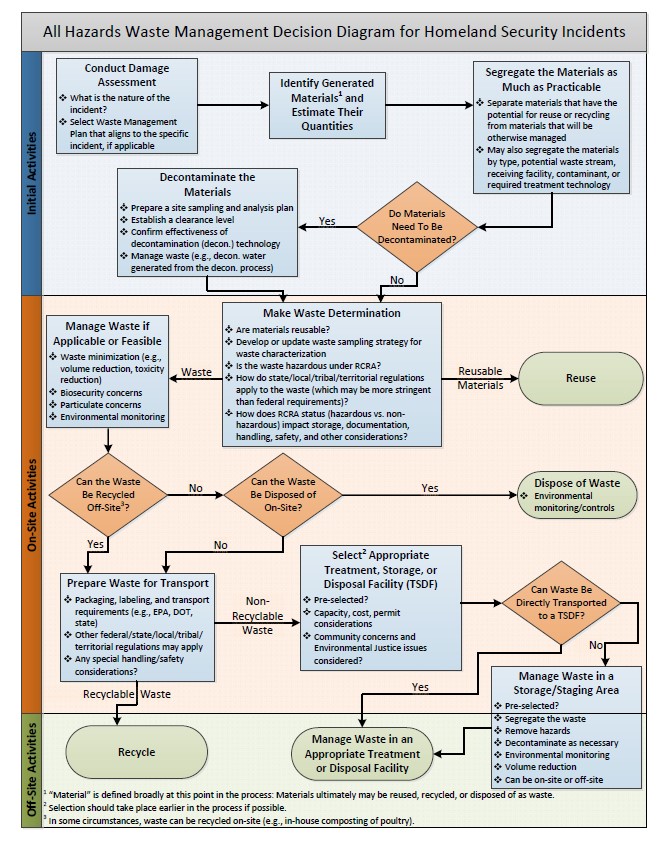
Waste Management Decision Making Process During A Homeland .

Critical Incident Management Policy Policies Procedures .

Cybersecurity Incident Response Plan Csirp Checklist 2019 .

Understanding Security Incident Response Servicenow Docs .

Focused Technologies Inc 9 Parts Of An Effective Cyber .

Figure 2 From Cyber Crisis Management A Decision Support .
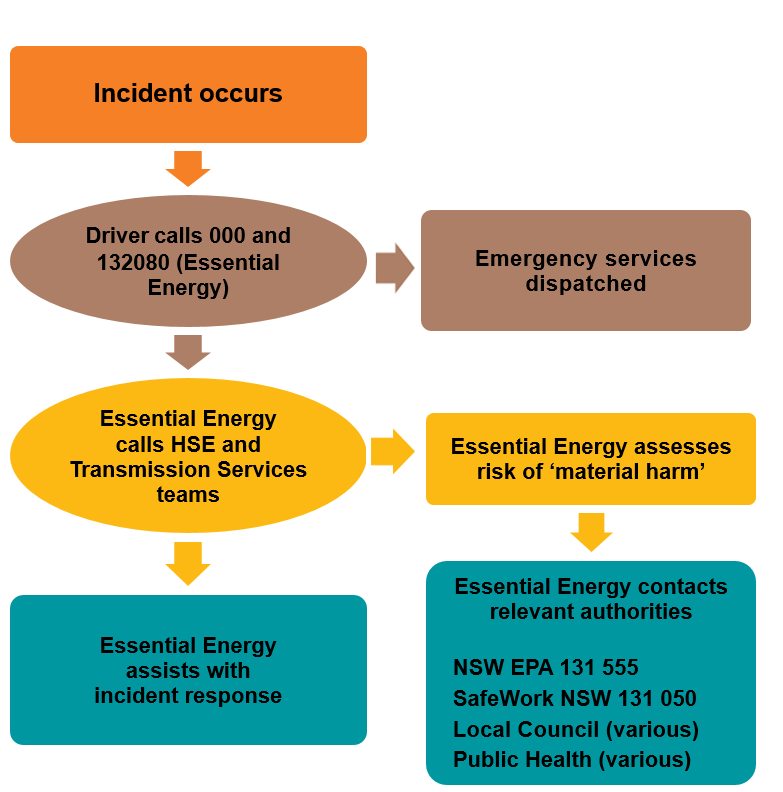
Pollution Incident Response Management Plan .
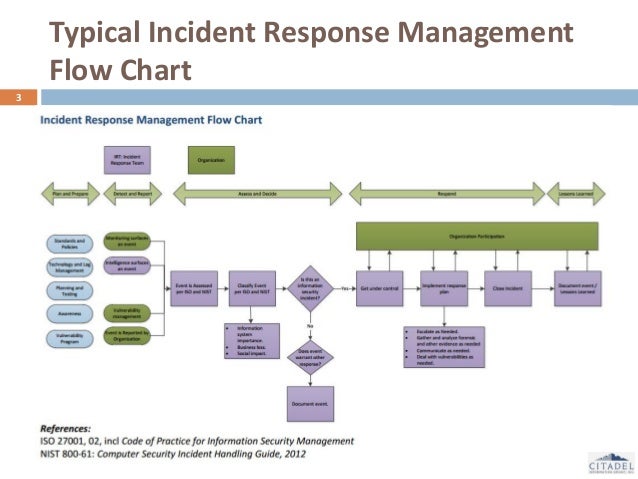
Fssf Breach Incident Table Top .
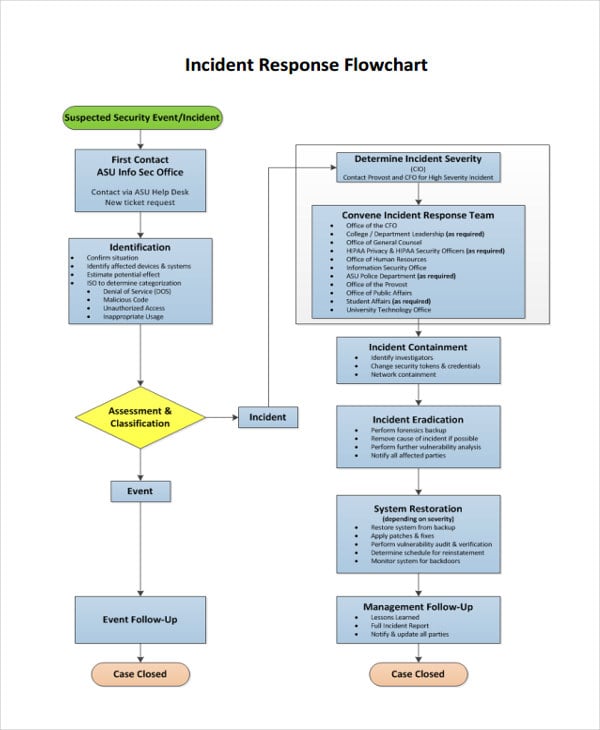
32 Sample Flow Chart Templates Free Premium Templates .

Data Breach Incident Response Plan Toolkit Infographic .

1 Incident Response Timeline Or Simple Process Flow .

47 Problem Solving Incident Management Process .

Dealing With Ransomware And Cryptolockers Security .
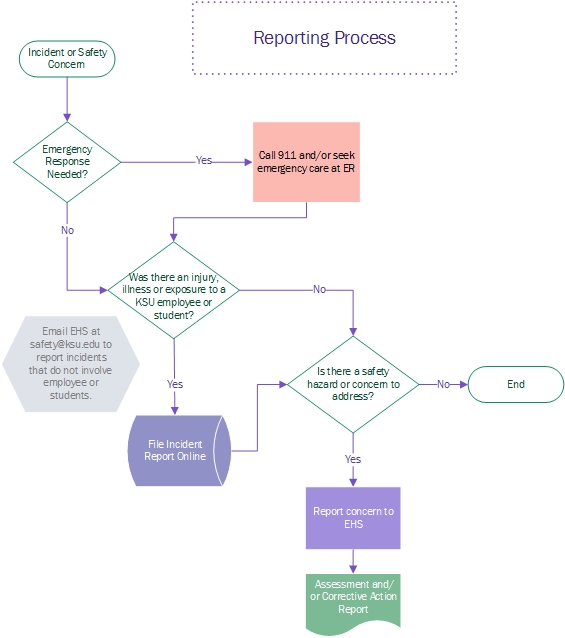
Incident Injury Reporting .

004 Data Incident Response Figure Cyber Plan Template Doc .

Workflow Examples From The Field .

Incident Response Tool .

What To Do If You Get Hit By A Ransomware Attack .

Security 101 .

Escalation Matrix Flow Chart Vmware How To File A Support .

Sans Digital Forensics And Incident Response Blog The Big .
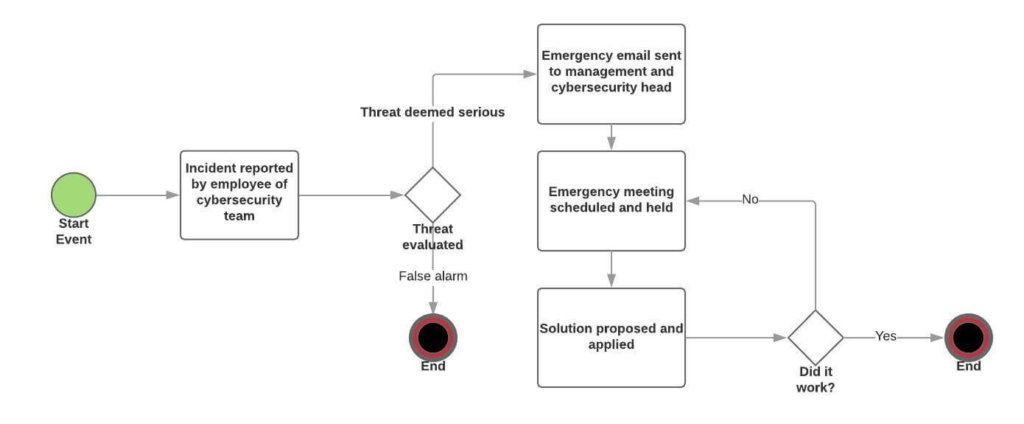
What Is A Process Flowchart And How To Use It 5 Examples .

What You Should Know About Ddos Incident Response Nsfocus .

4 Steps Toward A Better Plan 9yahds .

The Devops Incident Management Flowchart Victorops .
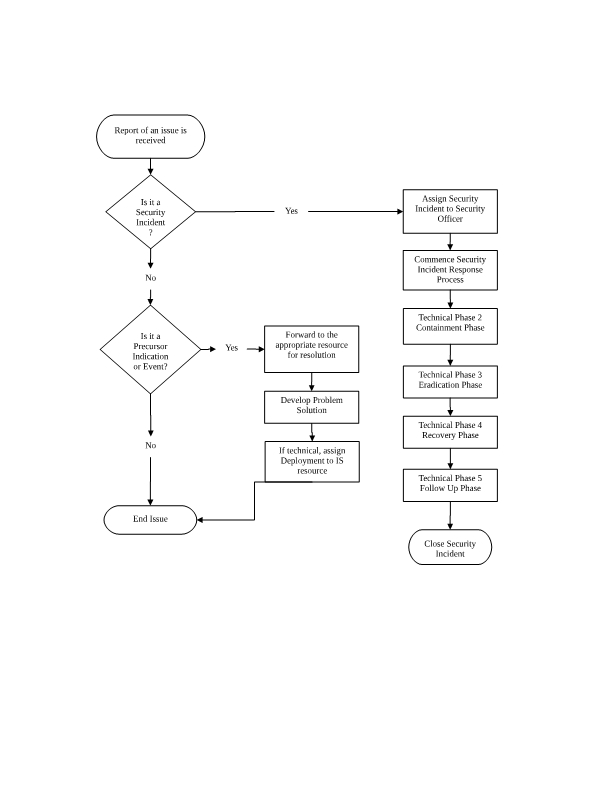
Security Incident Flowchart Polices Brazil .
Flowchart For Spills Response .
32 Sample Flow Chart Templates Free Premium Templates .
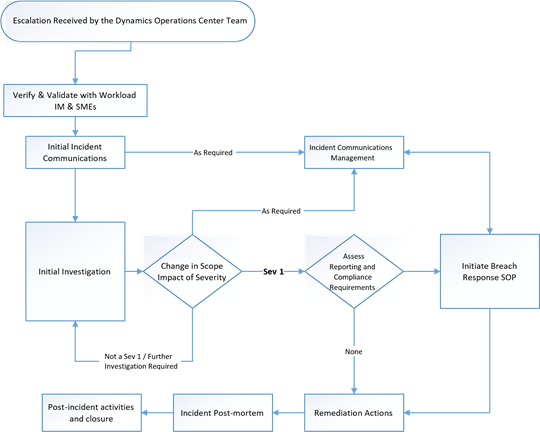
Security Incident Management In Microsoft Dynamics 365 .
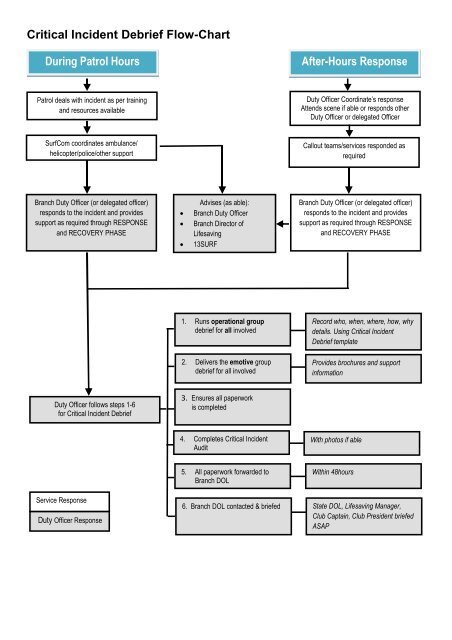
Supporting Resources And .

The Life Cycle Of An Incident Effective Incident Response .

Cimp Flow Chart Png Critical Incident Management Plan .

Incident Management It Process Wiki .

Security Orchestration Use Case Curtailing Phishing Attacks .

Helpdesk Troubleshooting Flowchart Incident Response Process .
- bok luke bryan seating chart
- capacitor substitution chart
- monier roof tile colour chart
- division chart with answers
- 6 month baby food chart in bengali
- 2006 charts top 40
- american airlines arena seating chart row numbers
- vaccination chart during pregnancy
- hexadecimal letters chart
- office 2013 gantt chart
- advil dosage chart by weight for adults
- lg tv comparison chart 2015
- seating chart meyerson symphony center
- math chart for 8th class
- blood group diet chart pdf
- nathan burton seating chart
- us soybean price chart
- diet chart for gaining weight for boy
- cholesterol chart 2016
- disney pin color price chart
- aes sedai strength chart
- cdss org chart
- head size chart
- carbon monoxide levels ppm chart
- apft run chart
- growth chart decal canada
- eye colour dominance chart
- atmosphere clothing size chart
- ucf depth chart
- elements of fiction chart