Endpoint Protection Comparison Chart - The 5 Stages Of A Malware Attack And What To Do Next

The 5 Stages Of A Malware Attack And What To Do Next
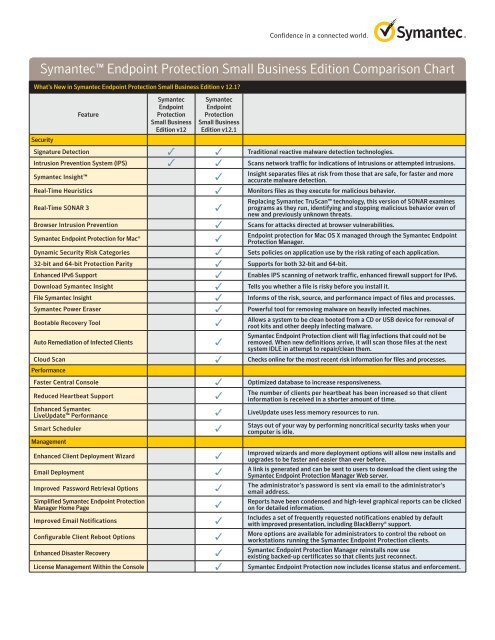
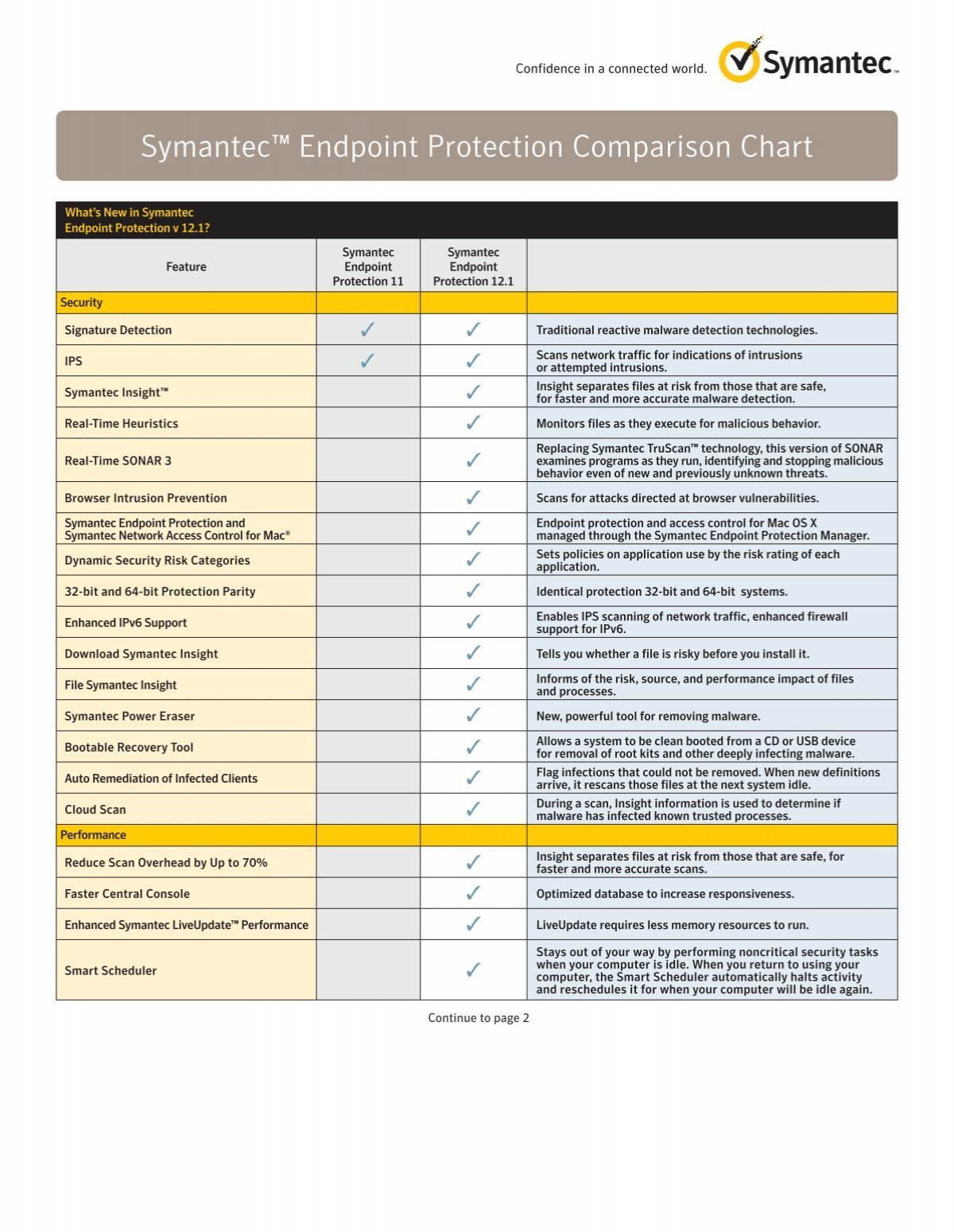
Symantec Endpoint Protection Comparison Chart Altimate .
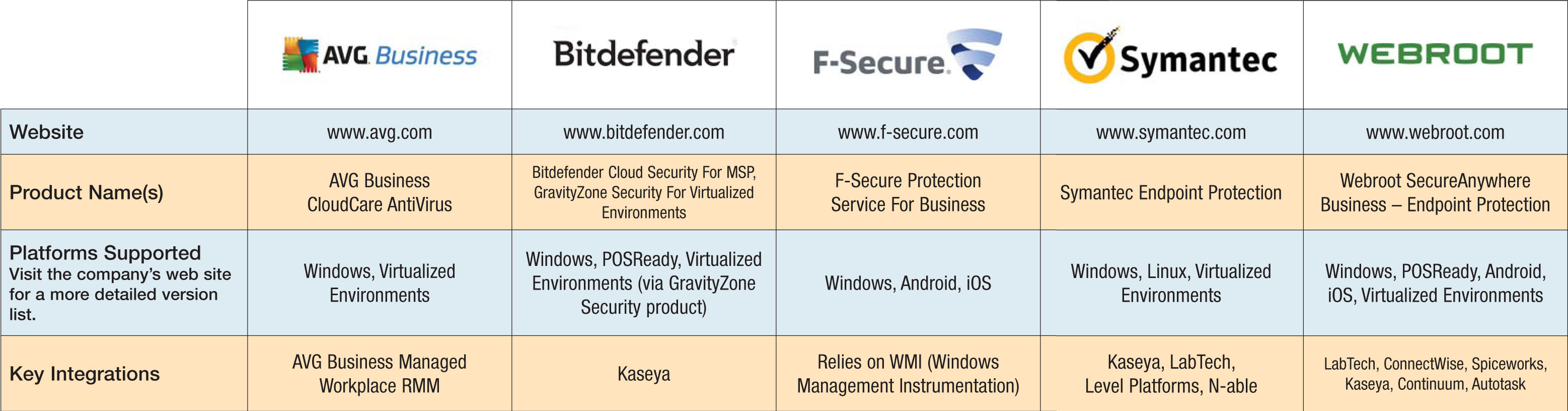
Product Comparison Endpoint Security Solutions .
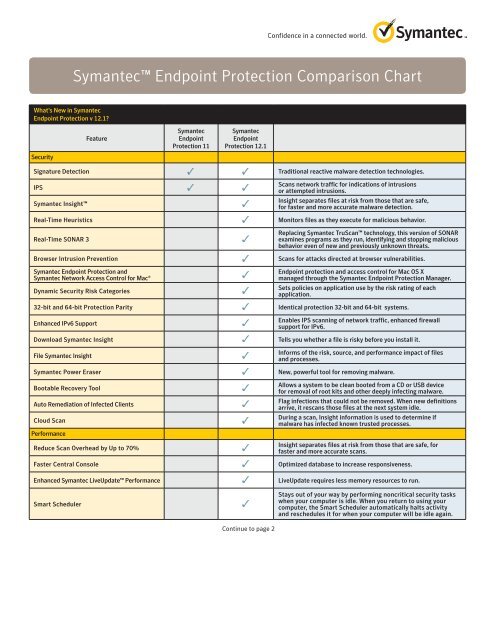
Symantec Endpoint Protection Comparison Chart Altimate .
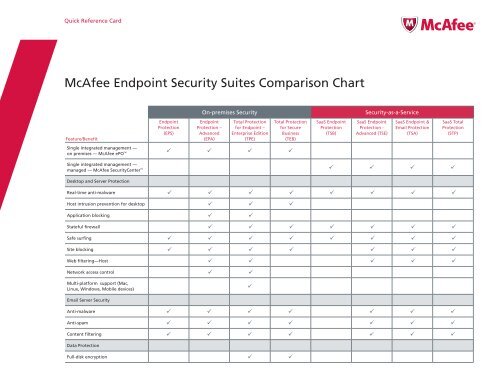
Mcafee Endpoint Security Suites Comparison Chart Arrow Ecs .

Kaspersky Endpoint Security Value Added Distribution In Uae .

Endpoint Antivirus Vs Endpoint Security Key Differences .

How To Choose Endpoint Security Vs Antivirus Software .

News From Avtest It Security Antivirus Research Av Test .

News From Avtest It Security Antivirus Research Av Test .
Mcafee Endpoint Security Suites Comparison Chart Arrow Ecs .
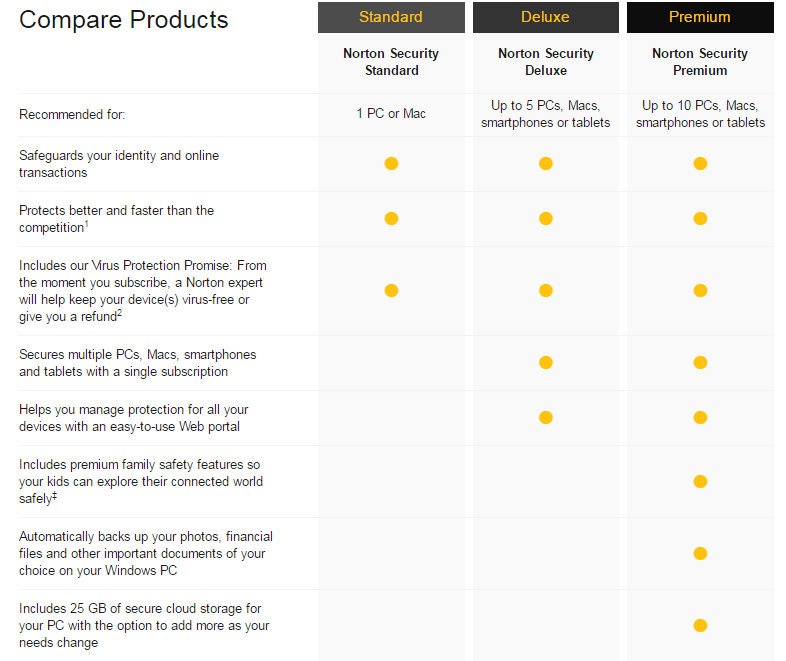
Enterprise Security Enterprise Endpoint Security Comparison .

The 5 Stages Of A Malware Attack And What To Do Next .

Whats Changed The 2019 Gartner Magic Quadrant For Endpoint .
Altimate Magazines .

Enterprise Security Enterprise Endpoint Security Comparison .
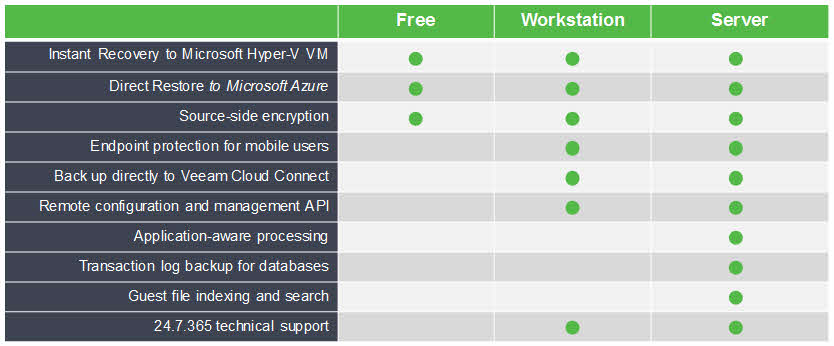
New Veeam Agent For Microsoft Windows 2 0 Beta Davoud .

Mssp Product Comparison Chart In 2019 Security Services .

Greenradar Bioxten Systems Llp .
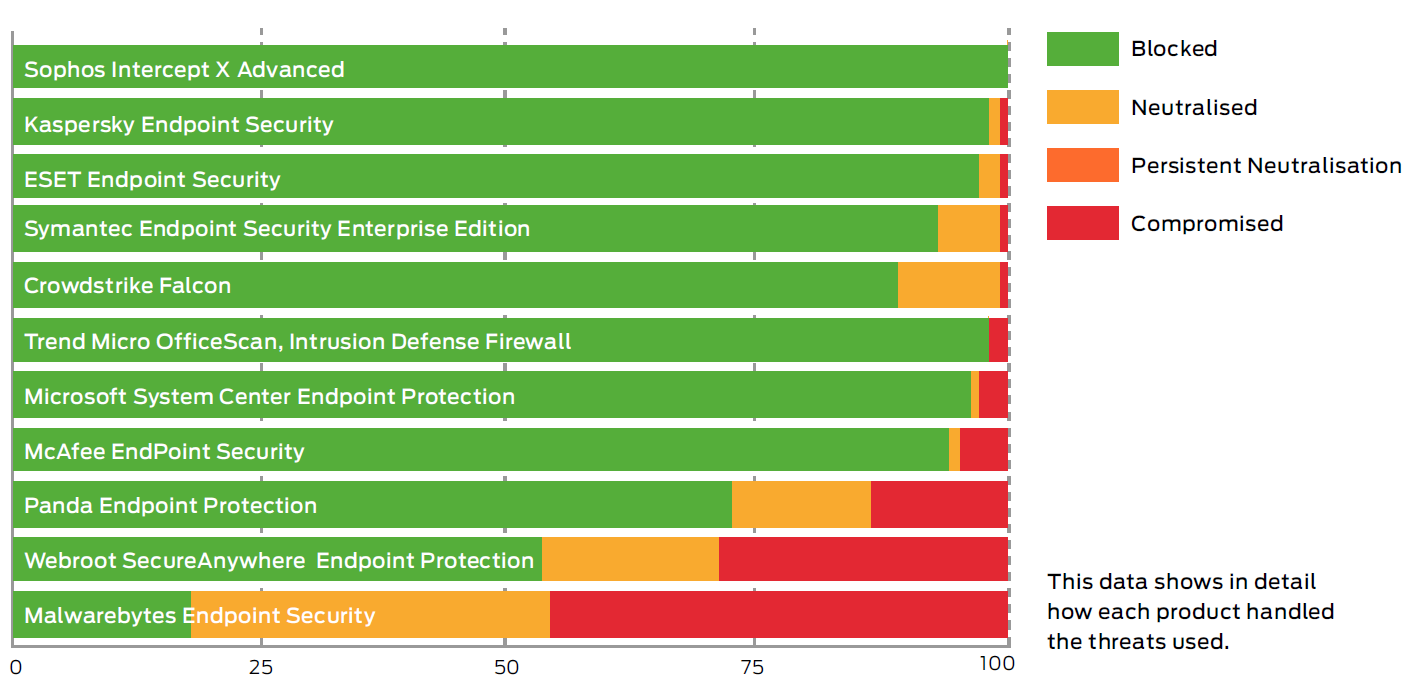
Sophos Ranks 1 For Endpoint Protection By Se Labs Sophos News .

Cybersecurity Management And Control For Companies .

The 22 Top Endpoint Protection Platforms Of 2019 For .

Difference Between Kaspersky And Trend Micro Difference .

Endpoint Protection Platform Epp Vs Endpoint Detection .

Microsoft Office Versions Comparison Chart Office Guide .

34 Hand Picked Virus Protection Comparison Chart .

34 Hand Picked Virus Protection Comparison Chart .
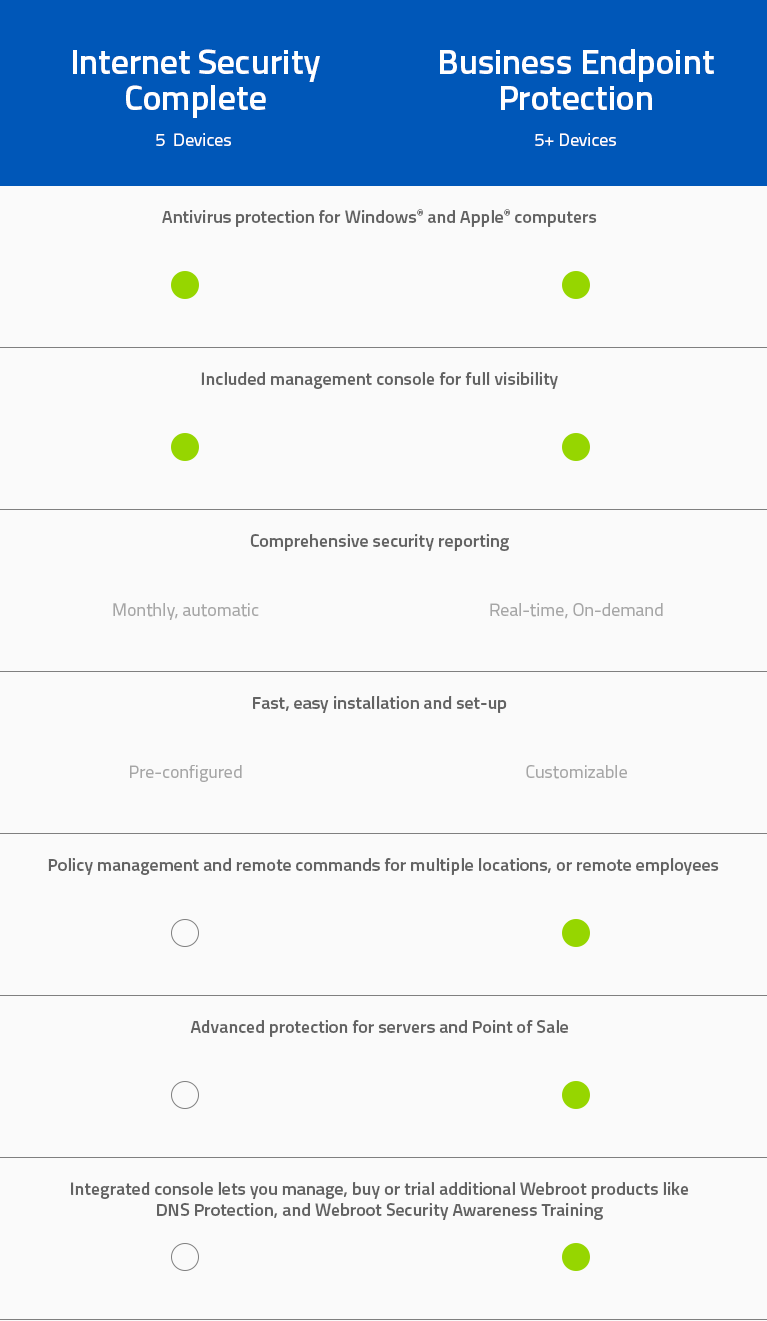
Small Business Antivirus Software Solutions You Can Trust .

Mcafee .
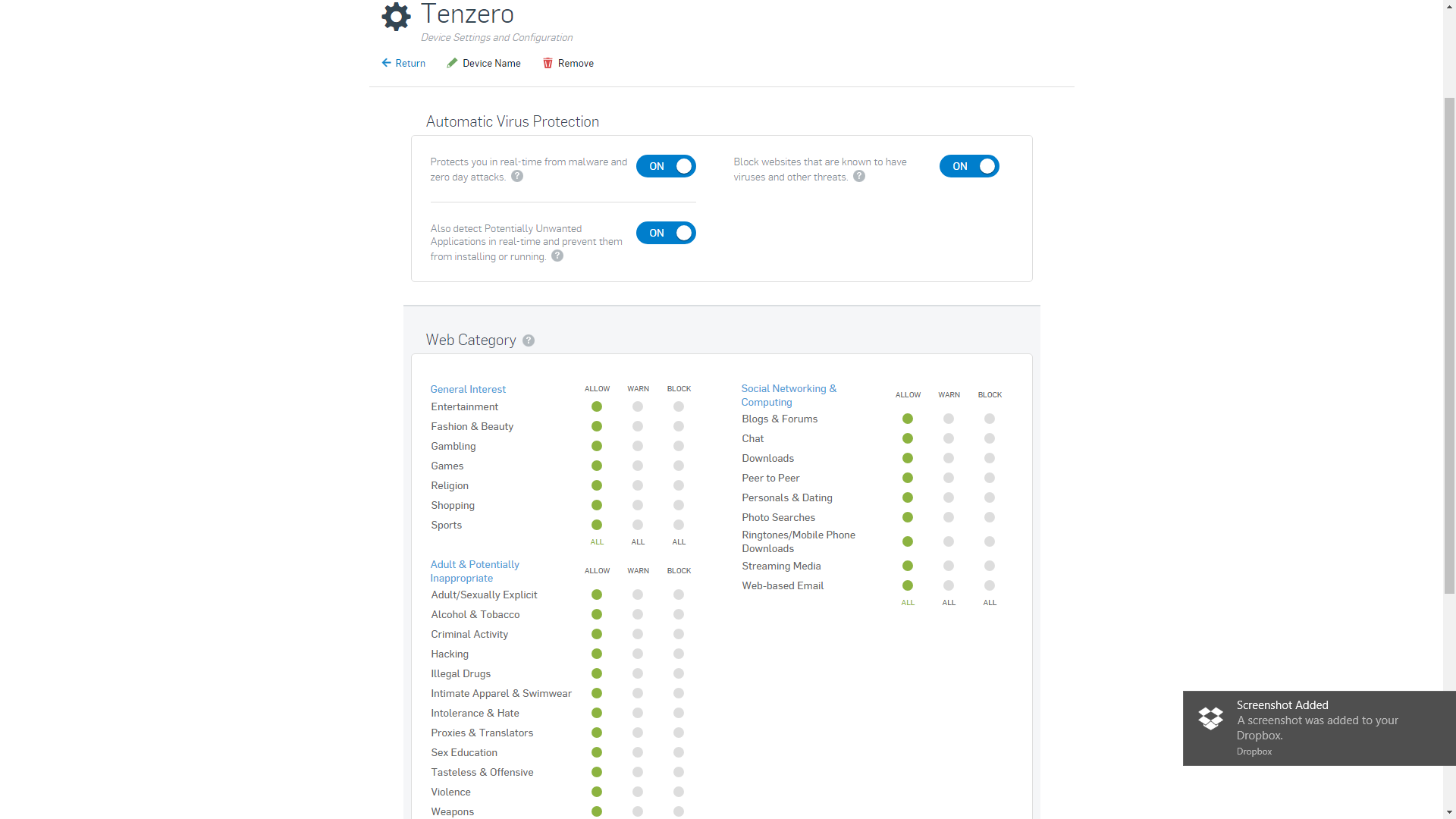
Sophos Av Comparatives .

Mcafee Endpoint Security Mcafee Products .

The 22 Top Endpoint Protection Platforms Of 2019 For Enterprises .

Difference Between Norton And Mcafee Difference Between .

Best Endpoint Security Software Products Comparison 2020 .
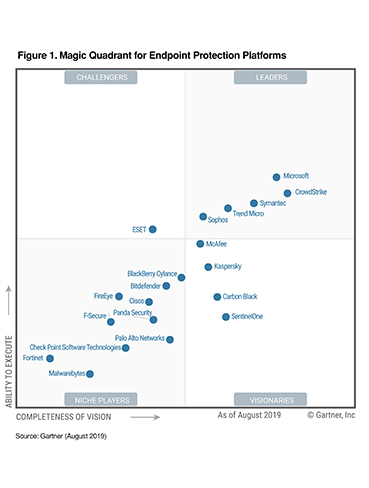
2019 Gartner Magic Quadrant Mq For Endpoint Protection .

The Best Hosted Endpoint Protection And Security Software .

Comparison Of Endpoint Protection Suites By The Tech Writers .

Advanced Endpoint Protection Aep Overview Nss Labs Inc .

10 Best Edr Security Services In 2020 For Endpoint Protection .

Best Endpoint Protection Software In 2019 G2 .
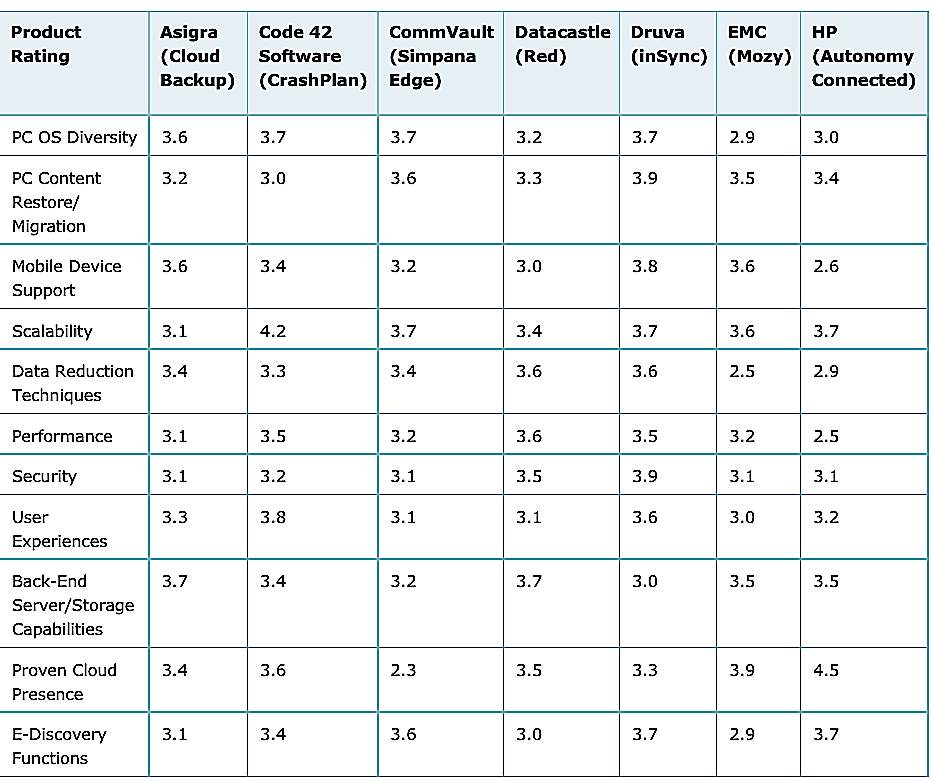
Enterprise Security Enterprise Endpoint Security Comparison .

Sonicwalls Cyber Security Earn Recommended Rating From .

Gartner Names Microsoft A Leader In 2019 Endpoint Protection .

50 Off Selected Eset Products Alt Works .
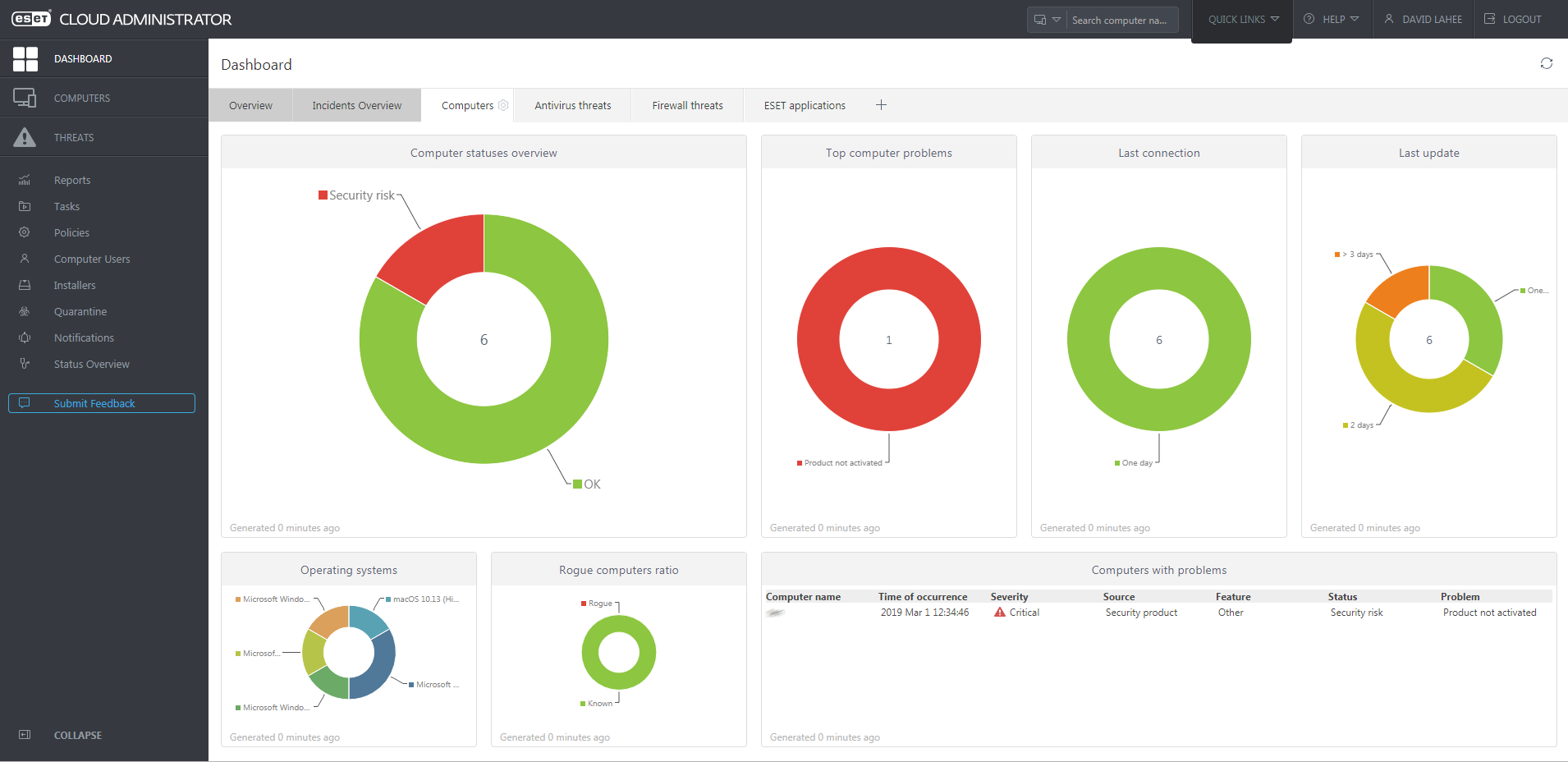
Business Security Test 2019 March June Av Comparatives .
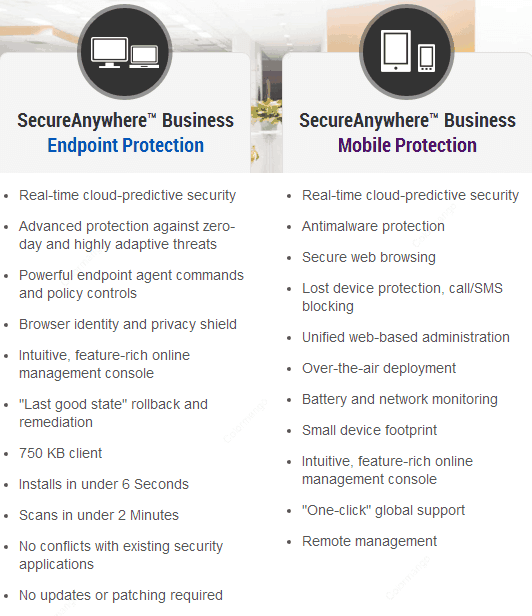
Secureanywhere Business Endpoint Protection .
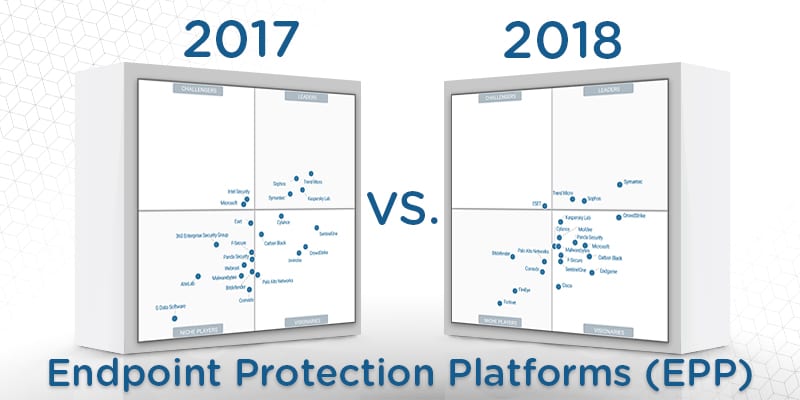
The Gartner 2018 Mq For Endpoint Protection Platforms .
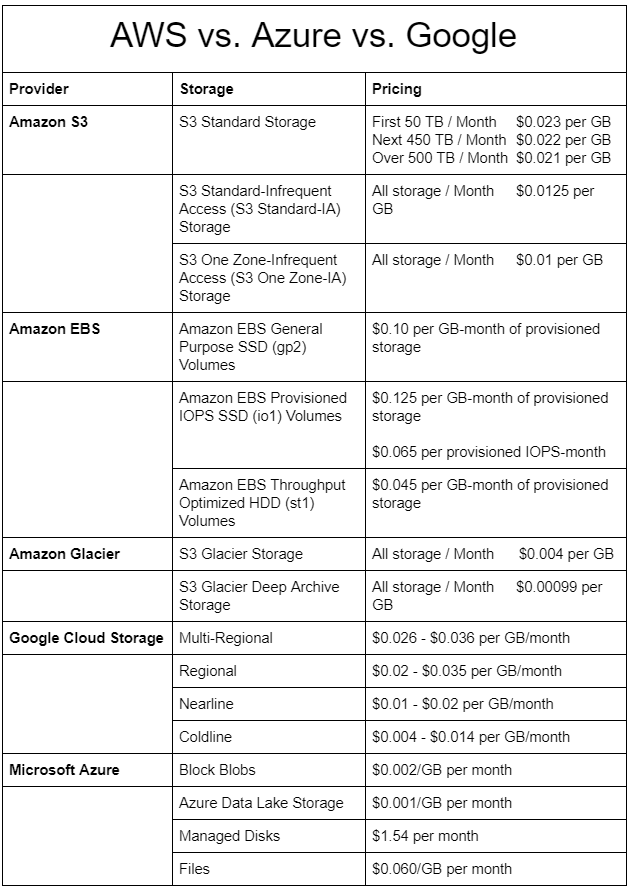
Cloud Storage Cost Comparison Aws Vs Azure Vs Google .
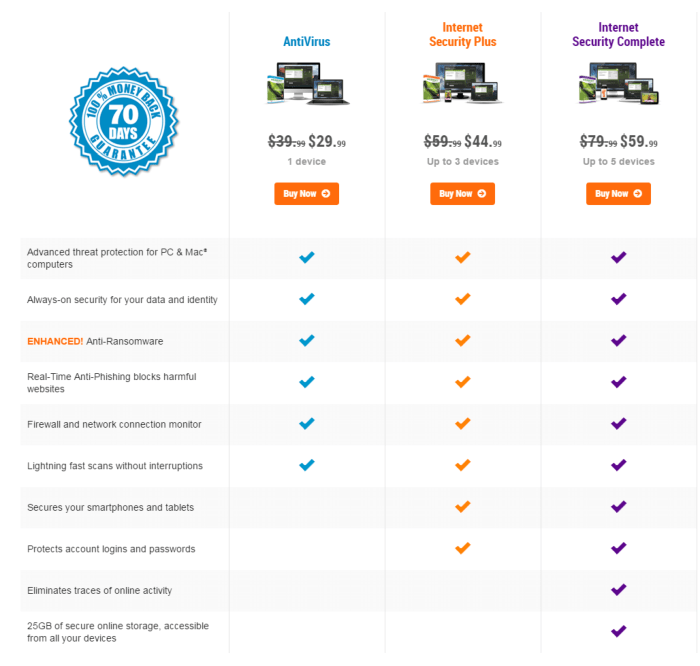
Compare Antivirus Security Suites Of 2019 Comparison Table .

Mcafee Endpoint Security Mcafee Products .
- minwax penetrating stain color chart
- the natal chart
- gi sportz glide pants size chart
- tamron teleconverter compatibility chart
- daytona supercross seating chart
- prediction chart
- gooby harness size chart
- led bulb wattage chart
- jojo bow size chart
- dynamic discs flight chart 2018
- mahogany color chart
- morning sickness chart
- stubhub center carson ca seating chart
- polyblend sanded grout color chart
- how to make a sticker chart for a toddler
- shipping box size chart
- home loan payment chart
- double hung egress window chart
- riot society size chart
- joico high lift color chart
- charting site
- decibel exposure chart
- kettle creek hatch chart
- supple cup size chart
- south park charted poster
- saratoga springs spac seating chart
- crossbow string length chart
- maps charts graphs
- tulip fabric dye color mixing chart
- european bra size conversion chart