Cyber Security Incident Response Flow Chart - Security Orchestration Use Case Curtailing Phishing Attacks

Security Orchestration Use Case Curtailing Phishing Attacks

Larson Security Releases Our Critical Data Classification .

Portland State Office Of Information Technology Computer .

Cybersecurity Incident Response Plan Csirp Checklist 2019 .

Cybersecurity Incident Response Plan Csirp Checklist 2019 .

Incident Response Process Flow Chart Cyber Security News .

Figure 2 From Cyber Crisis Management A Decision Support .
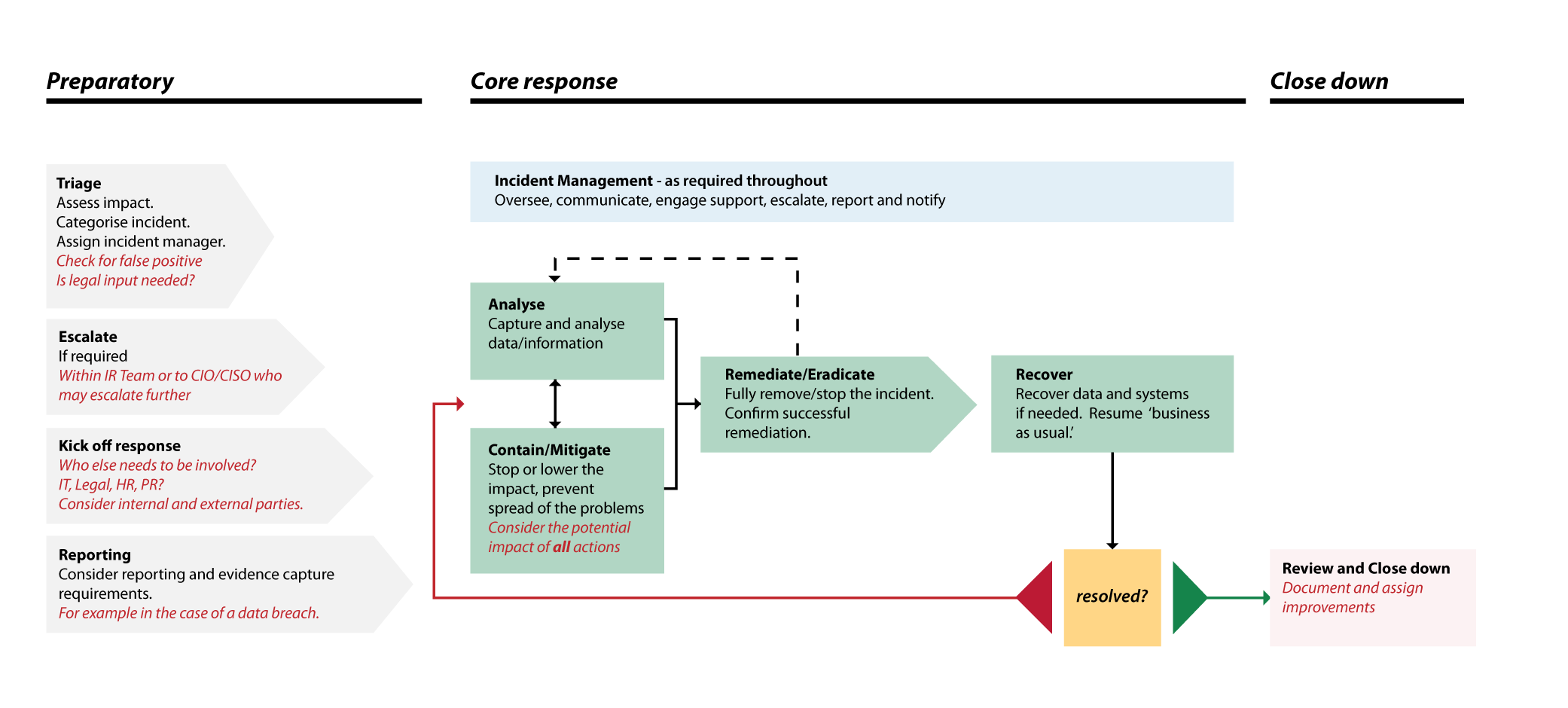
Incident Management Ncsc .

How To Create A Cybersecurity Crisis Management Plan .

How To Build An Incident Response Playbook Security Boulevard .

Focused Technologies Inc 9 Parts Of An Effective Cyber .

Understanding Security Incident Response Servicenow Docs .

Incident Response Flowchart Ferpa Sherpa In 2019 No .

Cybersecurity Incident Response Plan Csirp Checklist 2019 .
Generation Safe .

Dealing With Ransomware And Cryptolockers Security .

Security 101 .
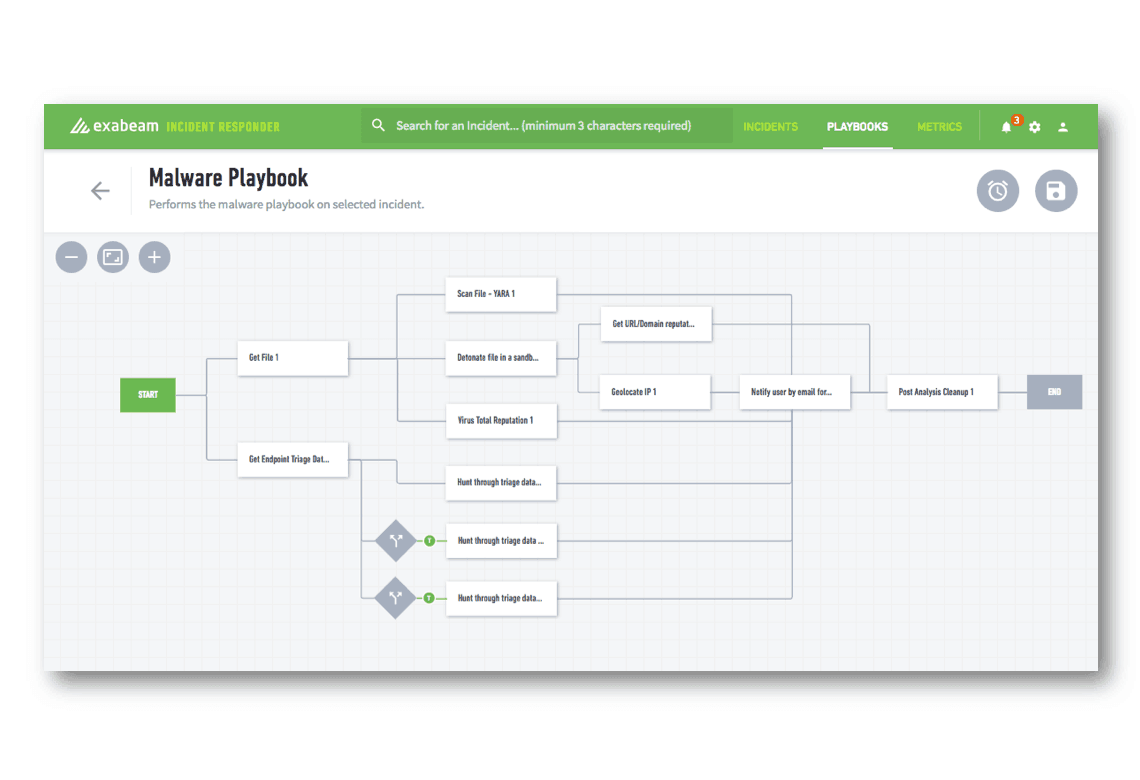
Cyber Security Incident Response Exabeam .

Sans Digital Forensics And Incident Response Blog The Big .
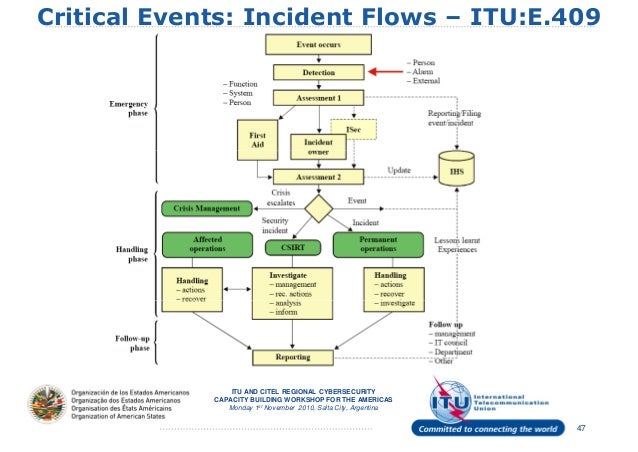
Un Itu Organisational Structures And Incident Management .

Incident Management Guideline Queensland Government Chief .

Cybersecurity Incident Response Plan Csirp Checklist 2019 .

Incident Vulpoint .

Cyber Security Incident Response Exabeam .
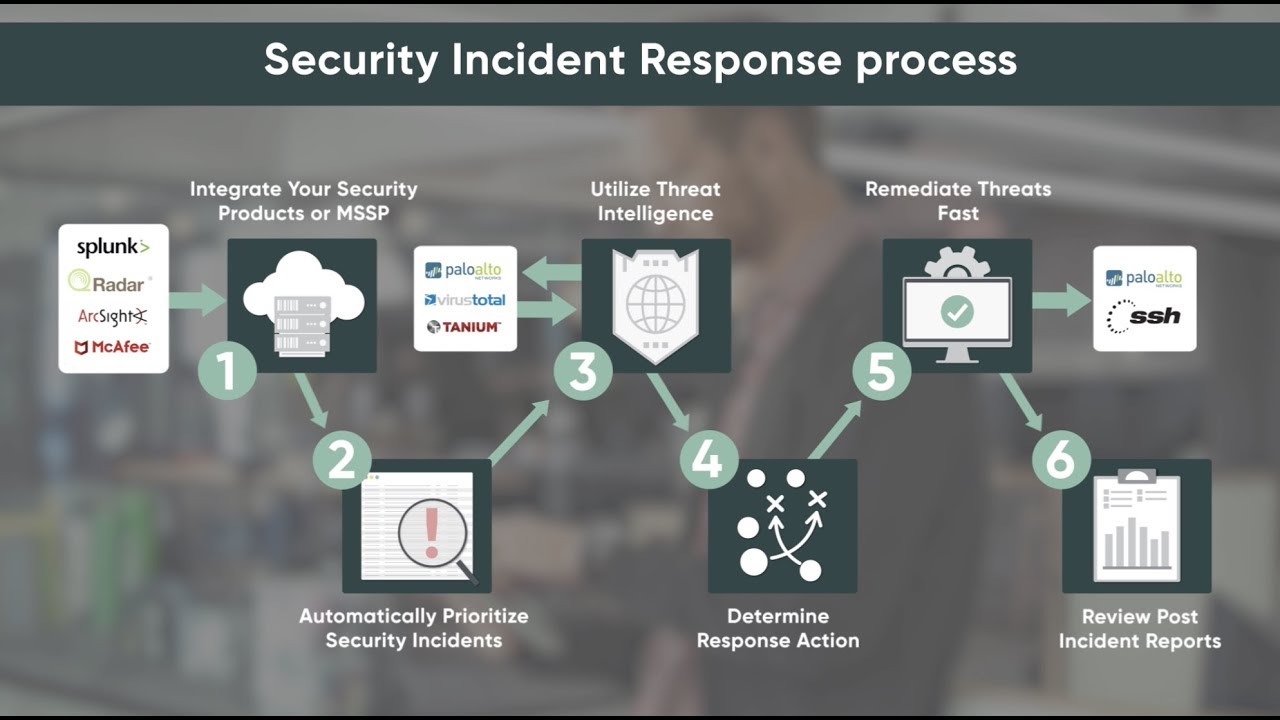
Understanding Security Incident Response Servicenow Docs .

Building An Incident Response Program Creating The .
Computer Security Incident Management Wikipedia .

Incident Management Guideline Queensland Government Chief .

Image Result For Cybersecurity Incident Response Plan No .
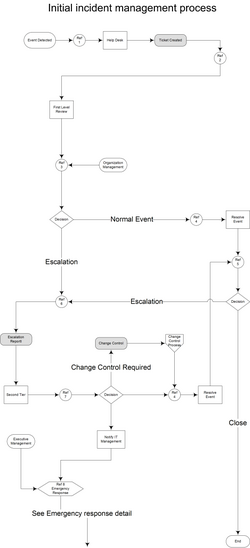
Gc Information Technology Incident Management Plan Canada Ca .

Free Cybersecurity Incident Response Plan Template .

Security Incident Phishing Workflow Template Servicenow Docs .

Risk Triage For Security Vulnerability Announcements .

Gsma Cybersecurity A Governance Framework For Mobile .

Cyber Security Incident Response Reporting Process .

Coalfire Coalfire Incident Response Retainer And Advisory .

Workflow For Cyber Security Incident Response Team .
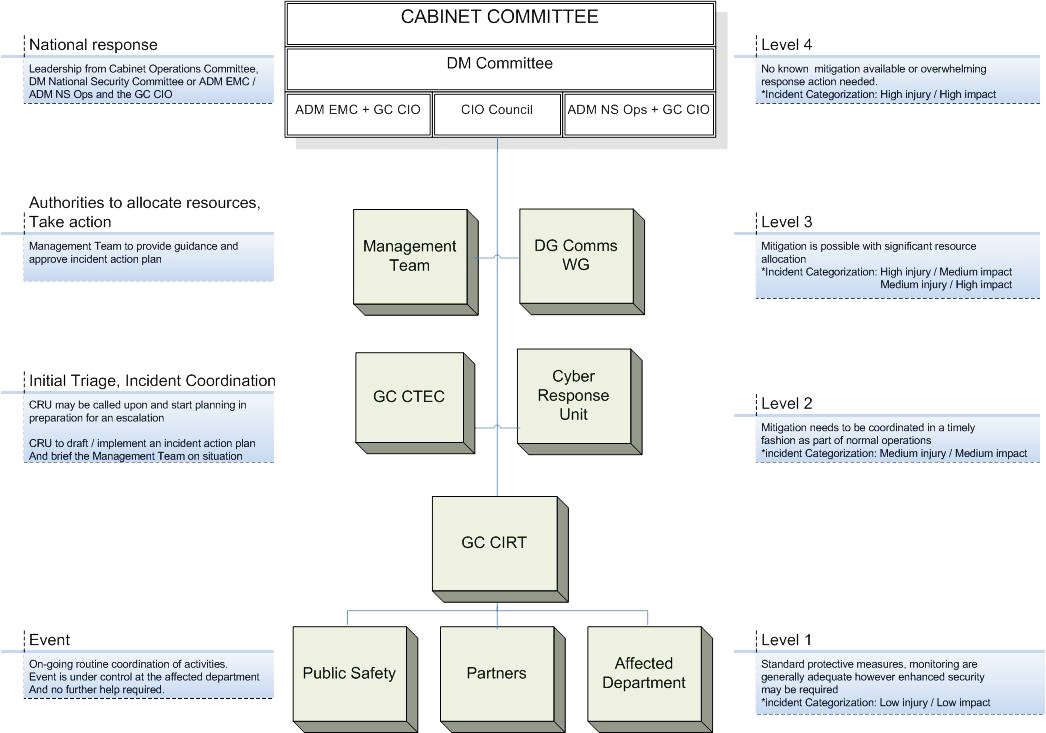
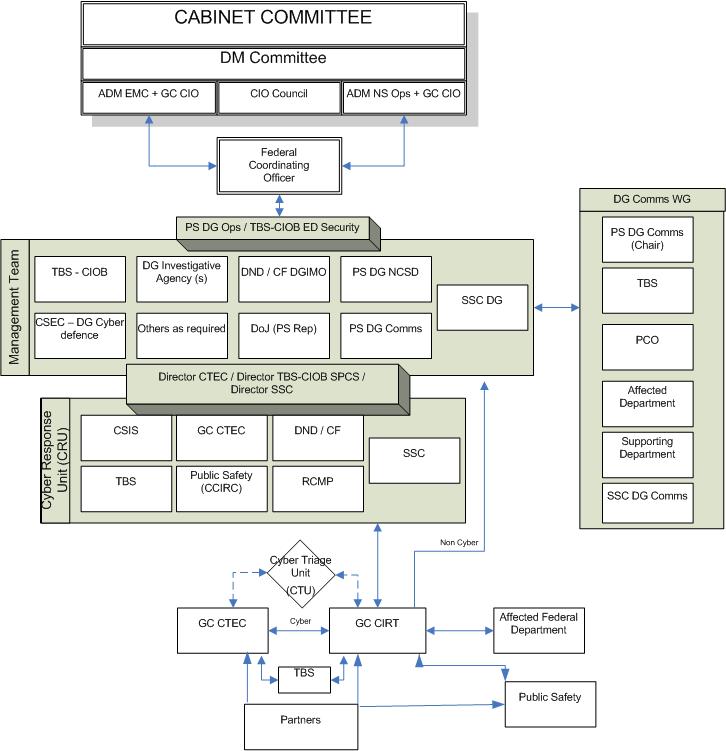
Gc Information Technology Incident Management Plan Canada Ca .

Emergency Response Planning Blogs Cyber Security .

47 Problem Solving Incident Management Process .

Security Orchestration Use Case Curtailing Phishing Attacks .

Cyber Security Incident Response Reporting Process .
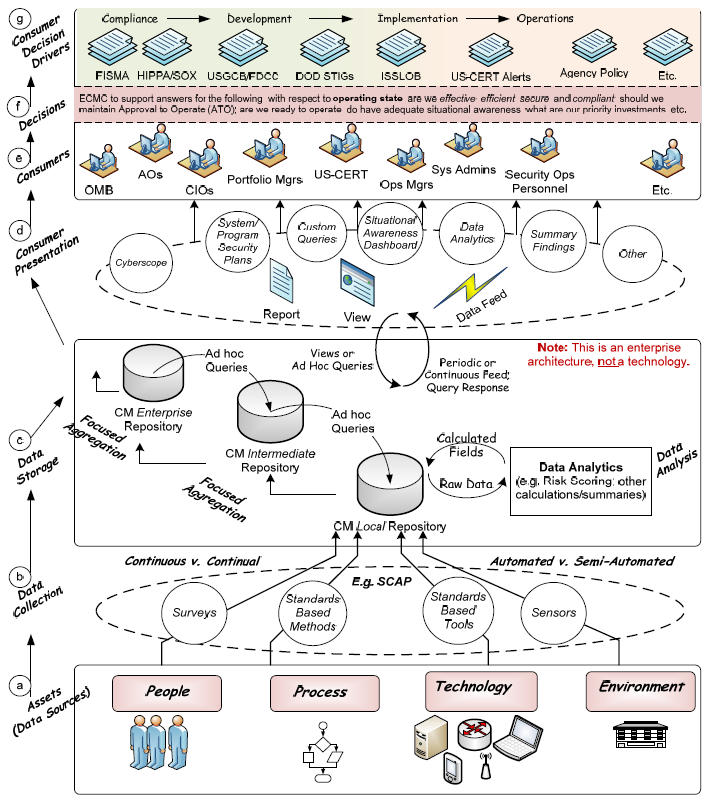
Situational Awareness In Cyber Security At T Cybersecurity .
How To Create A Cybersecurity Crisis Management Plan .

Automated Incident Response In Office 365 Atp Now Generally .

Guidance For Setting Up A Cloud Security Operations Center .

A Practical Guide To Building A Cyber Incident Response Team .

Flow Chart Of The Proposed Approach Download Scientific .

Esg Lab First Look Resolve Systems Accelerating Security .
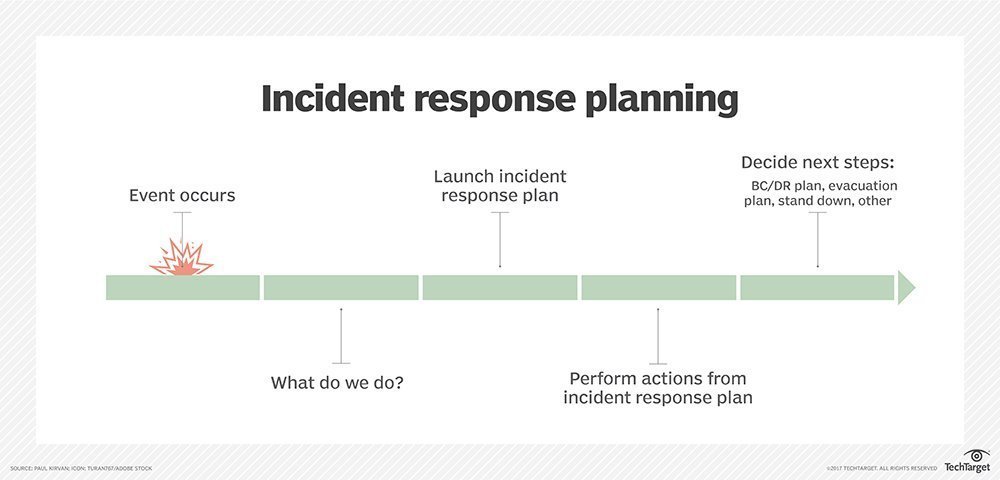
Free Cybersecurity Incident Response Plan Template .

The Roof Is On Fire Data Breach And Incident Response .
- yale ingalls rink seating chart
- cell organelles size chart
- pregnancy belly size chart
- psychic abilities in astrology chart
- billboard world chart
- acetylene conversion chart
- bismuth pellet count chart
- standard cable size chart
- foo fighters seating chart fenway park
- open c tuning chord chart
- welding rod current chart
- soil ph chart for fruit trees
- itunes folk charts
- dallas depth chart cowboys
- northwestern chart
- mobil equivalent chart
- free behaviour charts
- capital abcd chart
- cat6 conduit fill chart
- gantt chart template pro unlock
- lamons gasket color chart
- google pantone color chart
- pokemon go gloom evolution chart
- rogers arena seating chart ufc
- verbatim m disc compatibility chart
- kitco com gold chart
- armour to synthroid conversion chart
- isami gi size chart
- encyclopedia of chart patterns pdf
- the 70 weeks of daniel 9 chart