Charting The Attack Surface Of Trigger Action Iot Platforms - Adopting A Zero Trust Approach 5 Cyber Threats To Expect

Adopting A Zero Trust Approach 5 Cyber Threats To Expect

Charting The Attack Surface Of Trigger Action Iot Platforms .
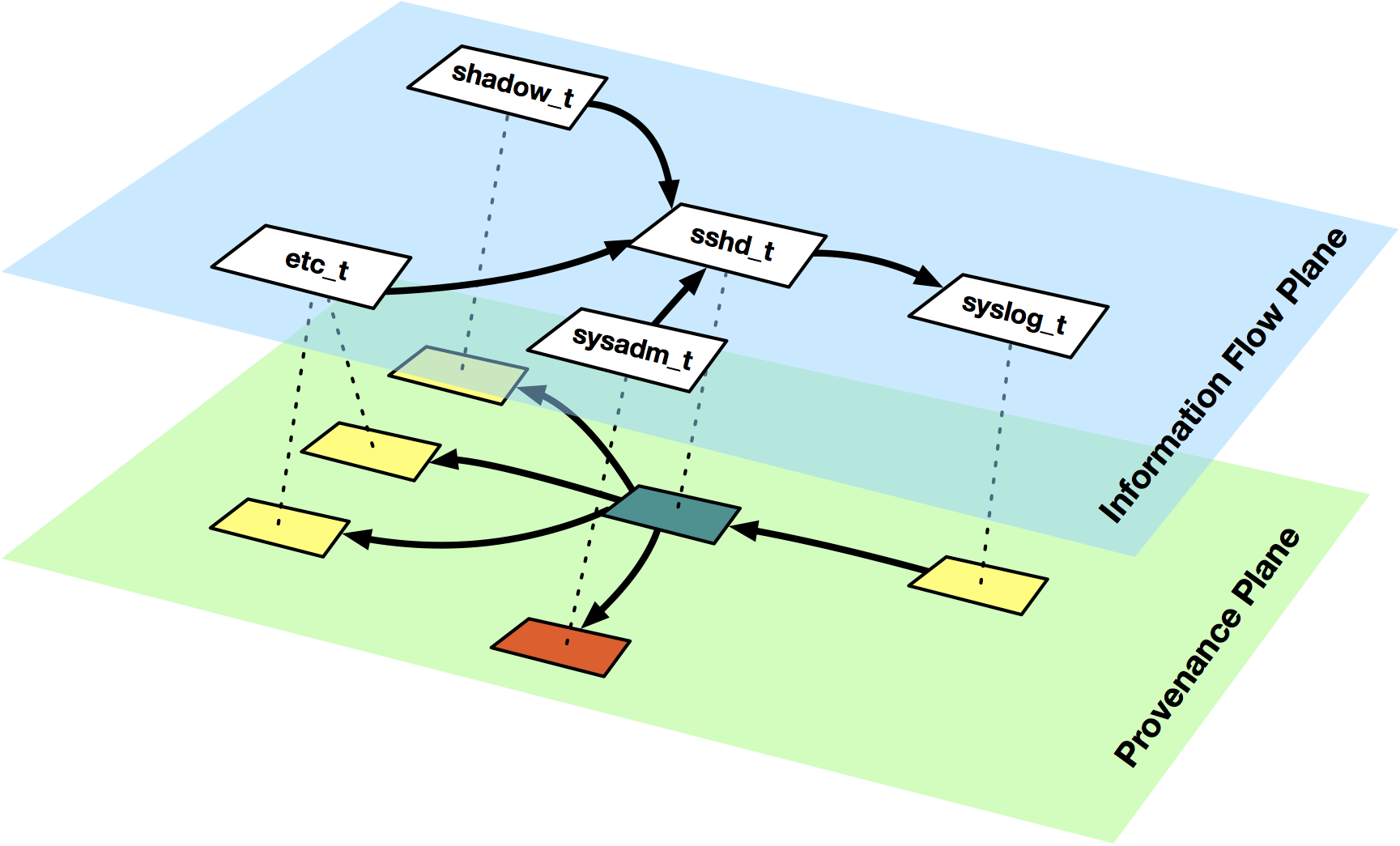
Consumer Device Security .

Charting The Attack Surface Of Trigger Action Iot Platforms .
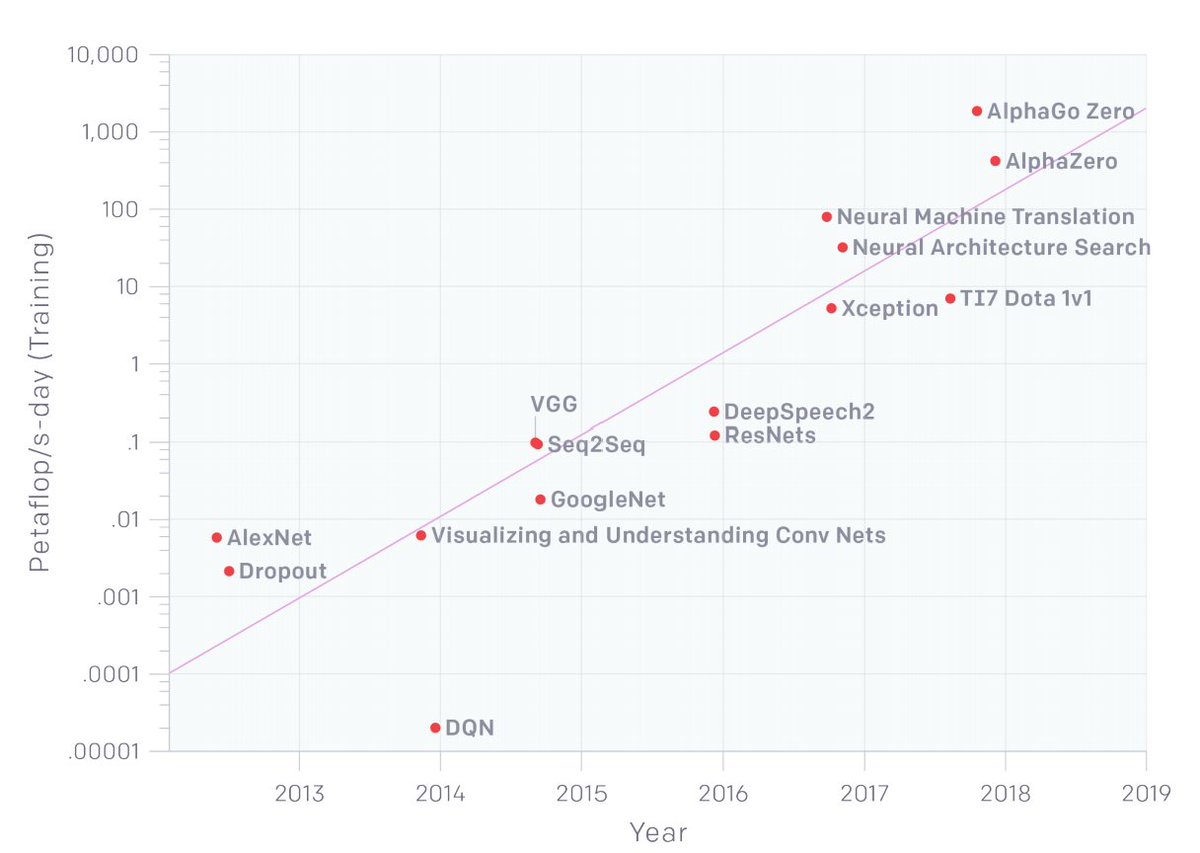
Research .
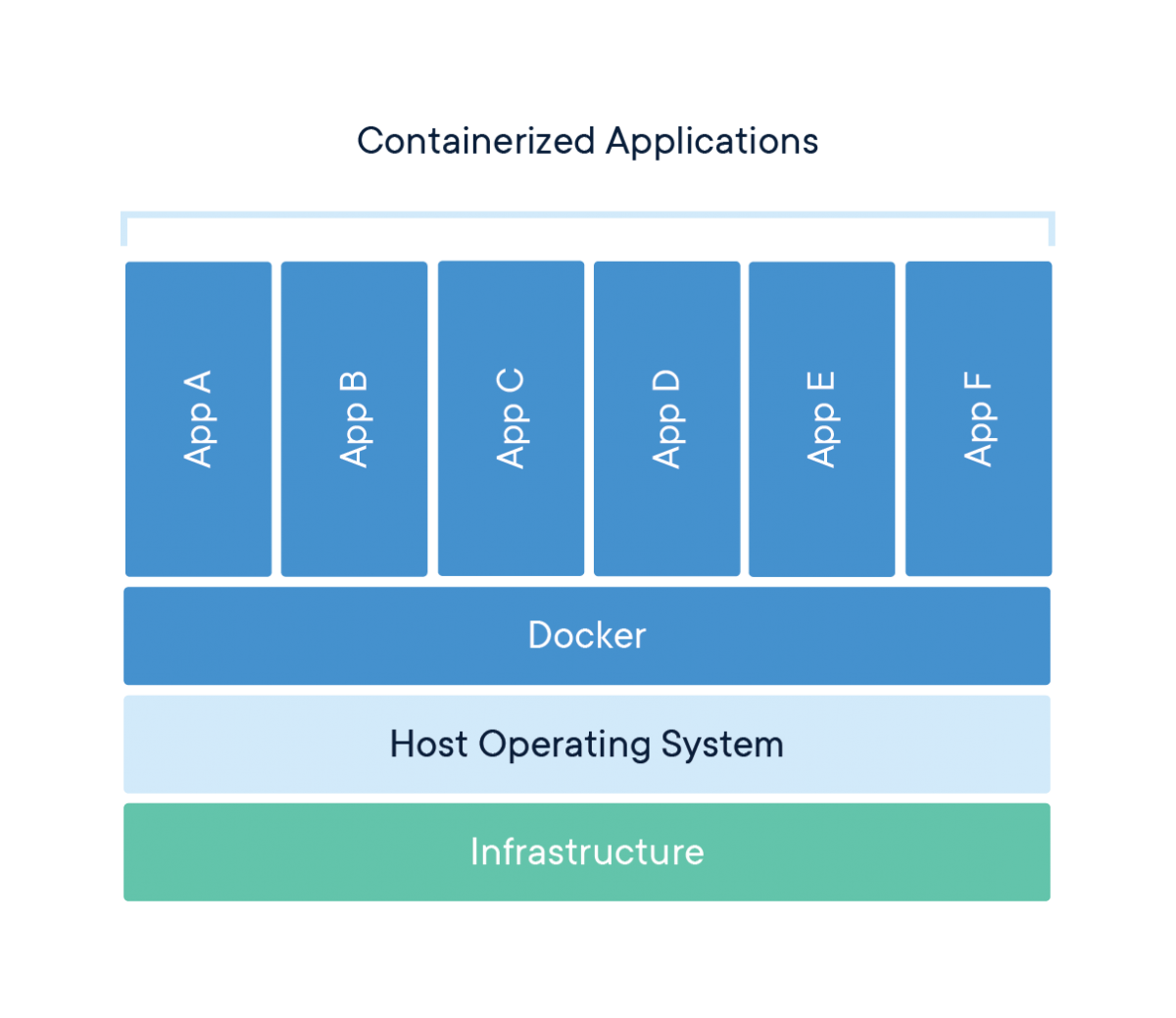
Adam Bates Adambatesorg Twitter .

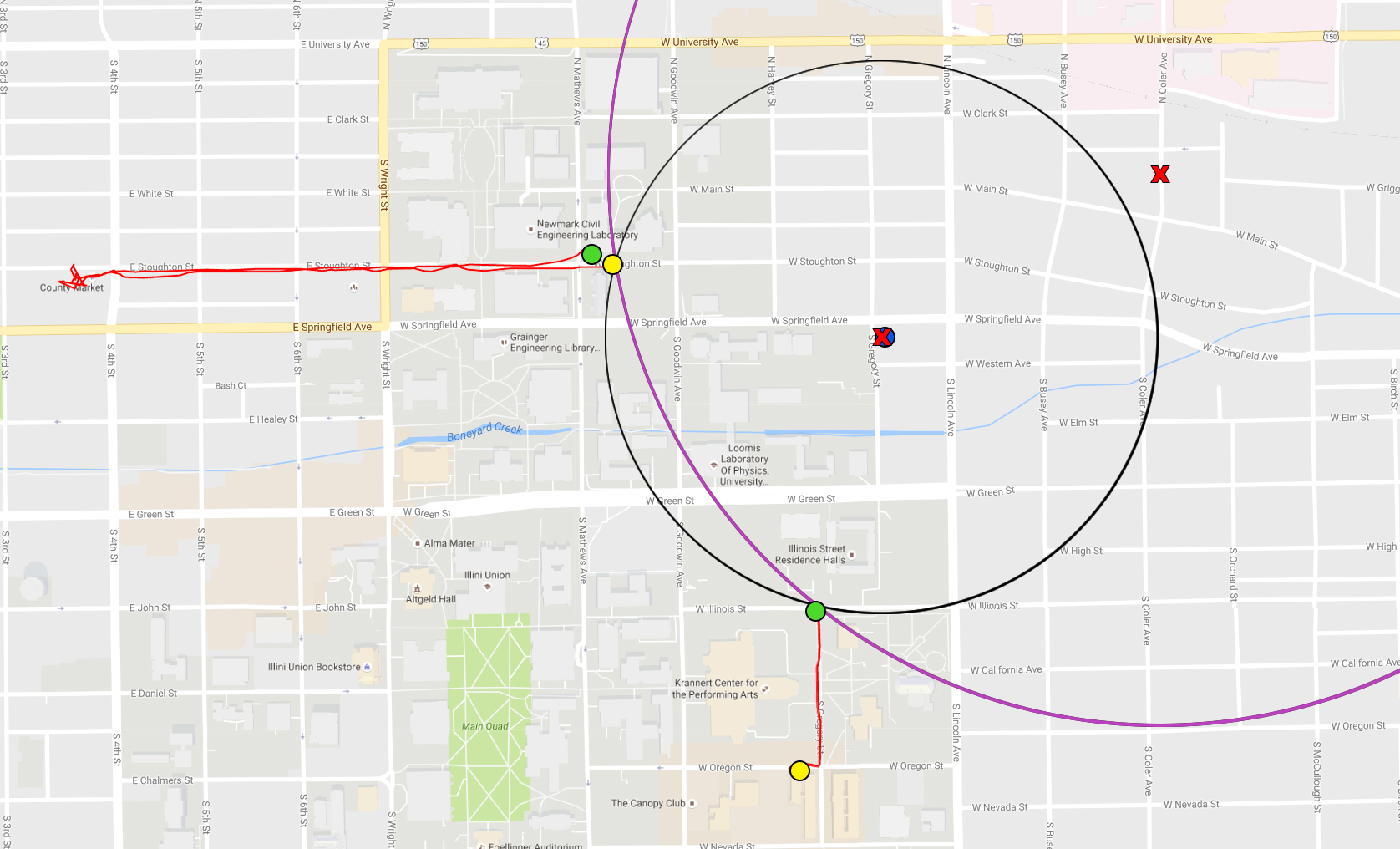
The Tool Also Provides A Textual Explanation Of Why The Rule .
Internet Of Robots Mobile Apps And Enterprises .

Shows An Example Of The Output Produced By The Tool The .

Articles Vinnter Ab .
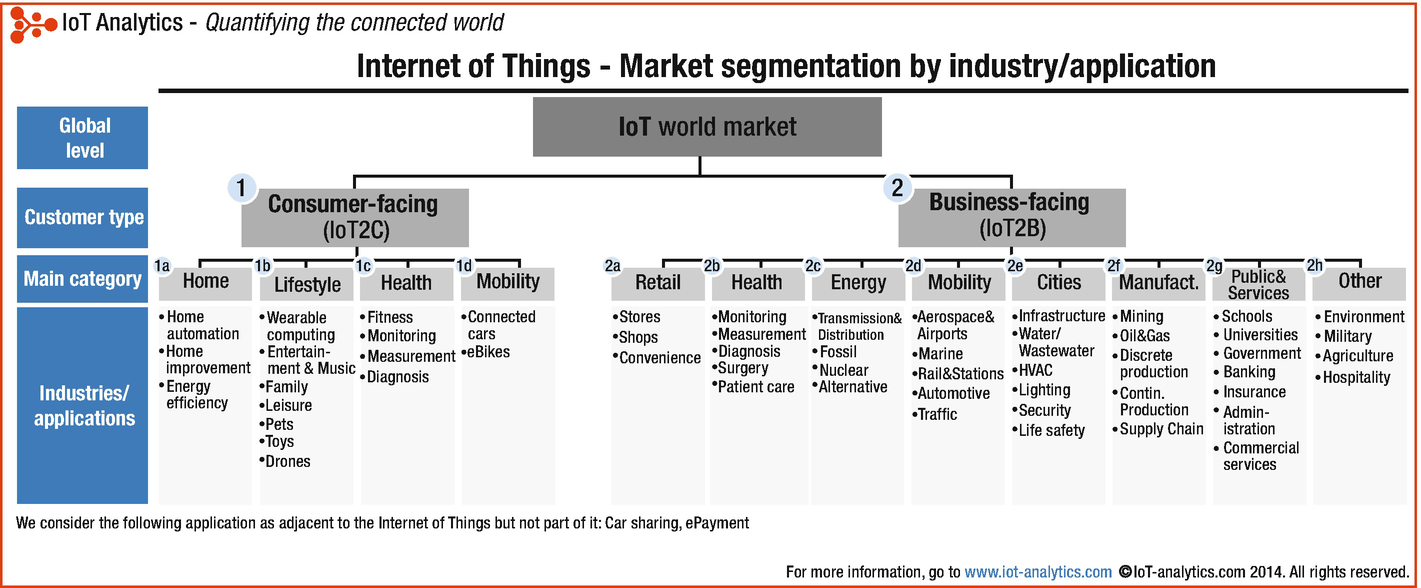
Iot Frameworks And Complexity Springerlink .

Adam Bates Adambatesorg Twitter .

Articles Vinnter Ab .
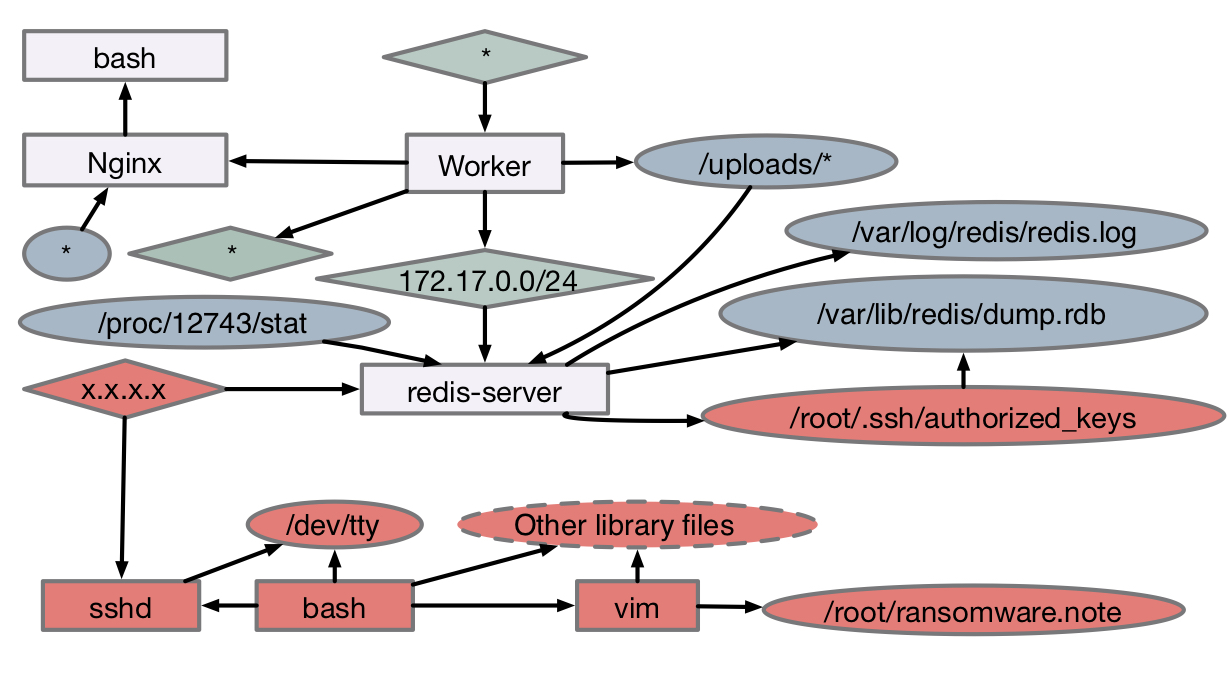
Adam Bates .
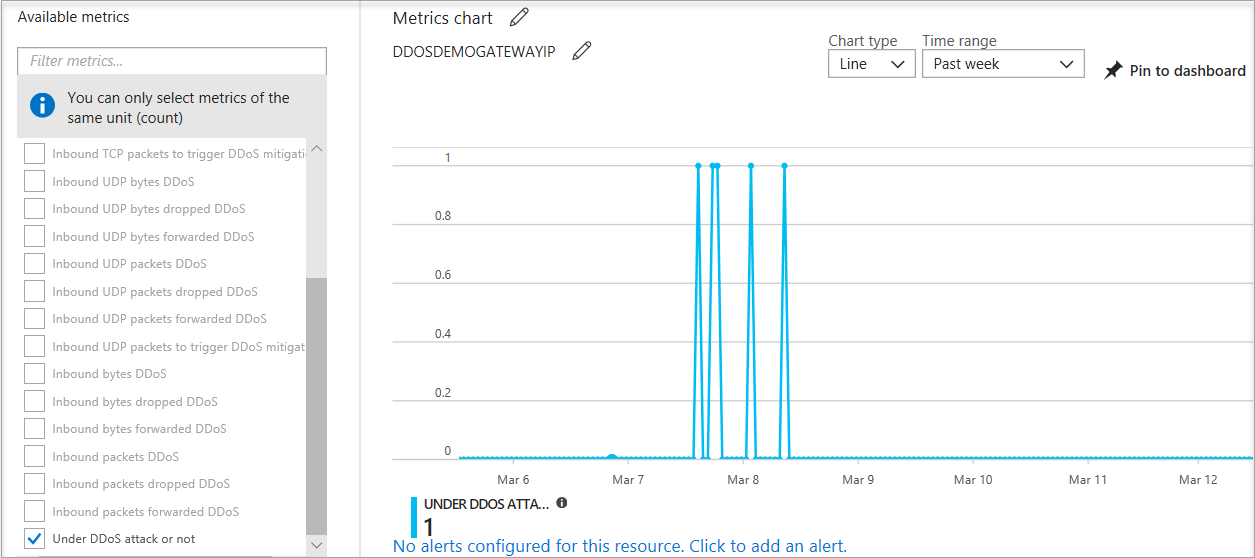
Azure Ddos Protection Designing Resilient Solutions .

Articles Vinnter Ab .
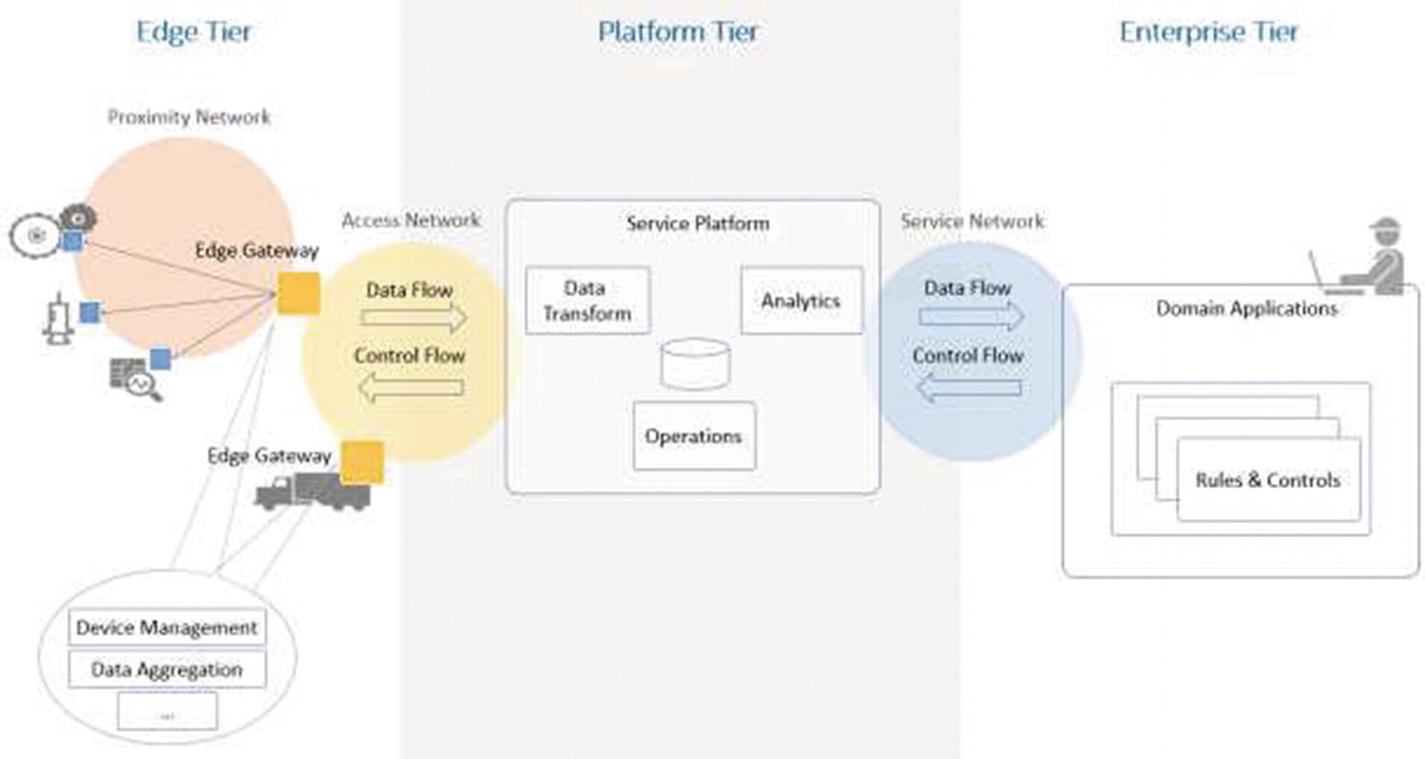
Iot Frameworks And Complexity Springerlink .

The Environment For Executing Rules In A Simulated Context .
Nextgen Kill Chain Defending The Cloud .

Enterprise Iot Projects Data Ml Security And Other Key .
Adam Bates Adambatesorg Twitter .

2018 A Year Of Cyber Attacks Hackmageddon .
Adam Bates .

Articles Vinnter Ab .

Pdf Supporting End User Debugging Of Trigger Action Rules .
Pdf Contexiot Towards Providing Contextual Integrity To .
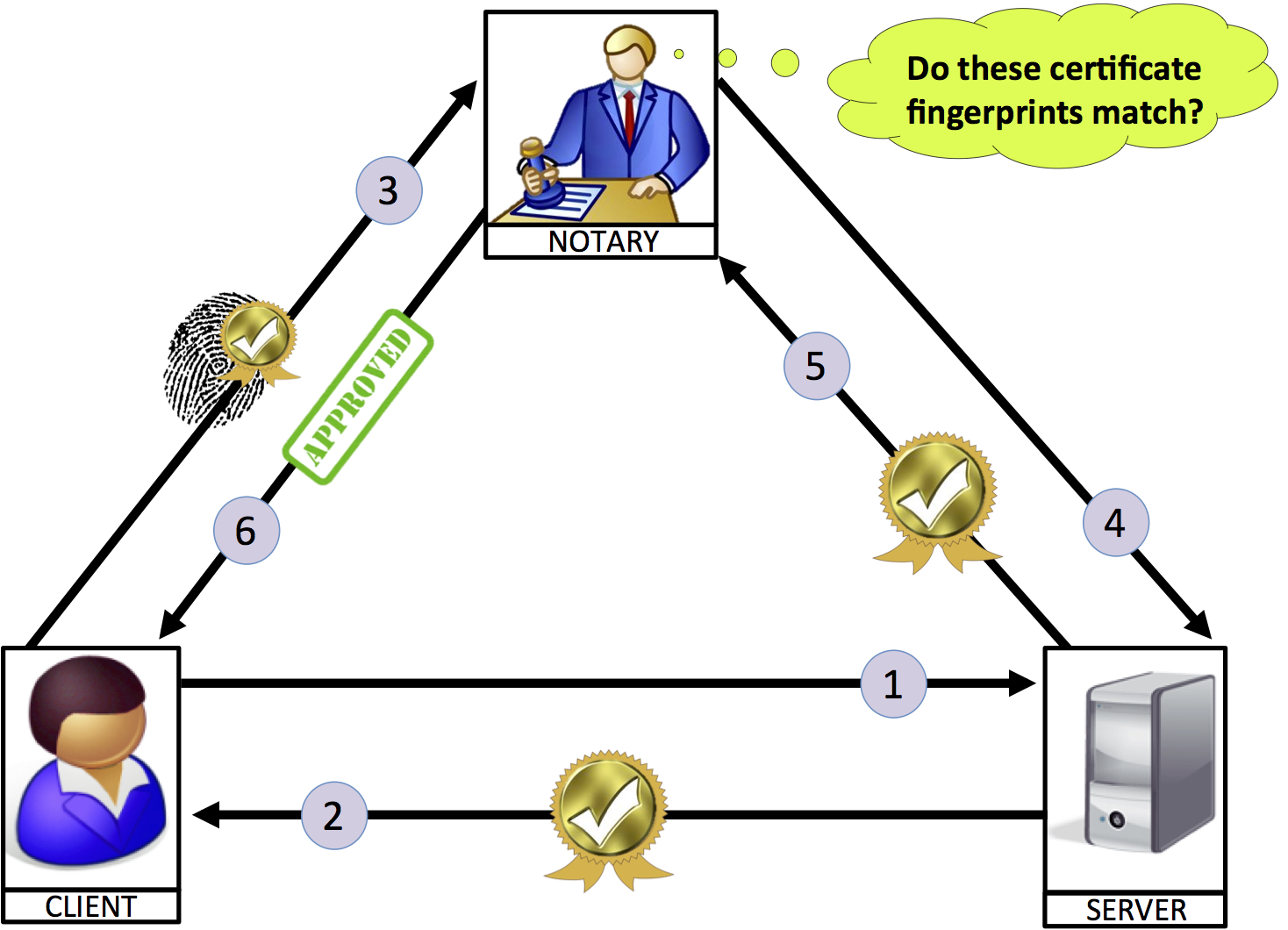
Adam Bates .
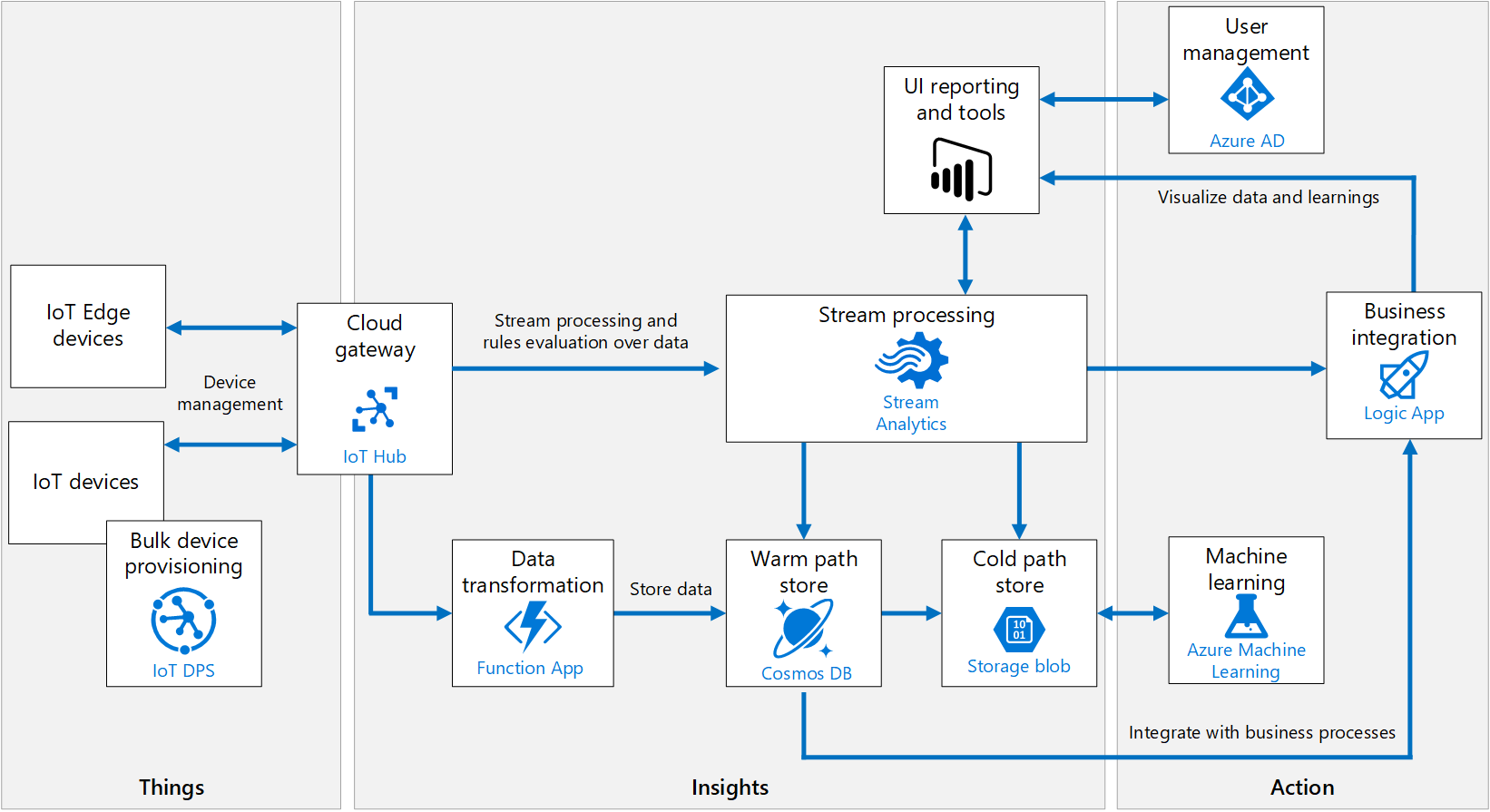
Azure Iot Reference Architecture Azure Reference .
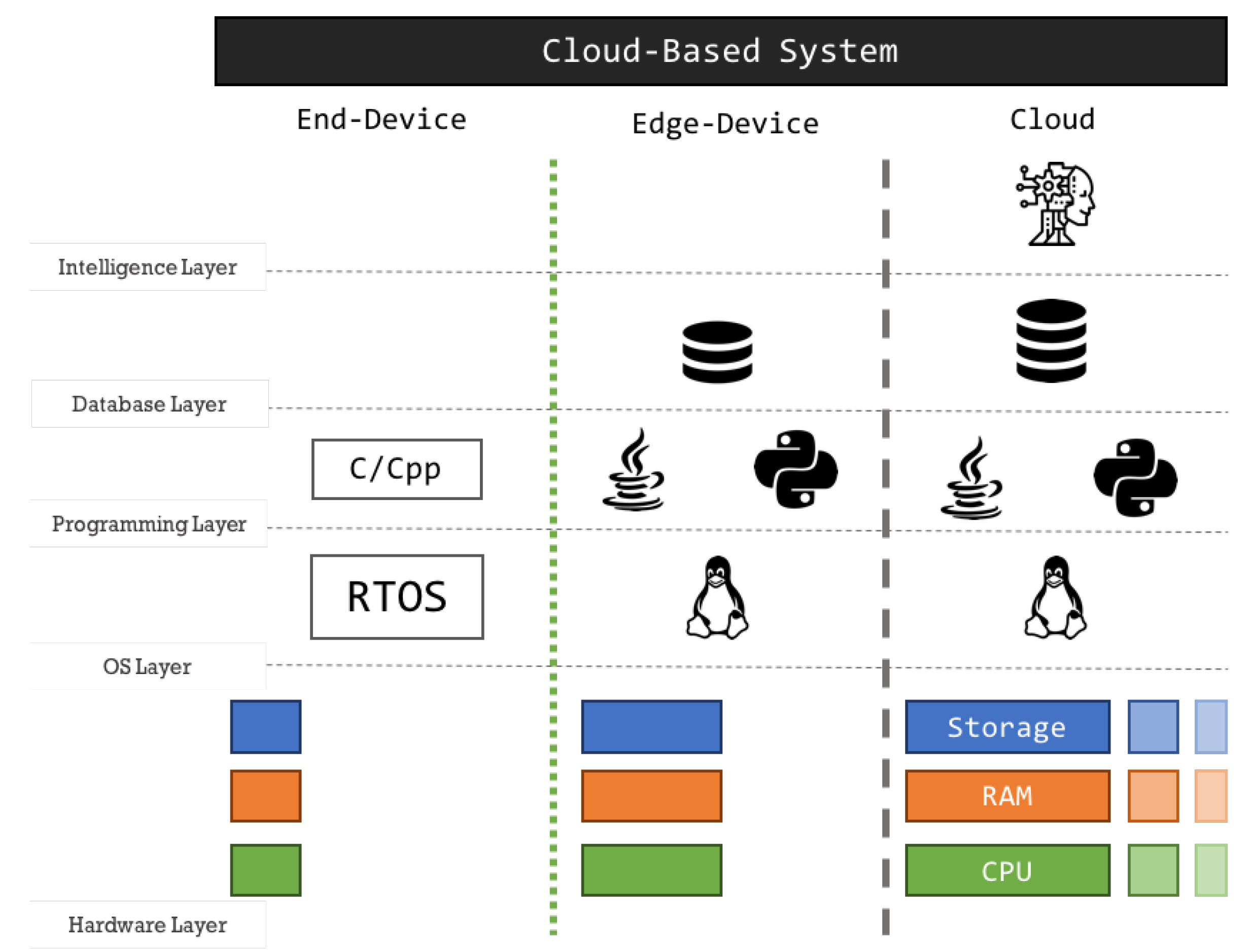
Electronics Free Full Text Machine Learning In Resource .
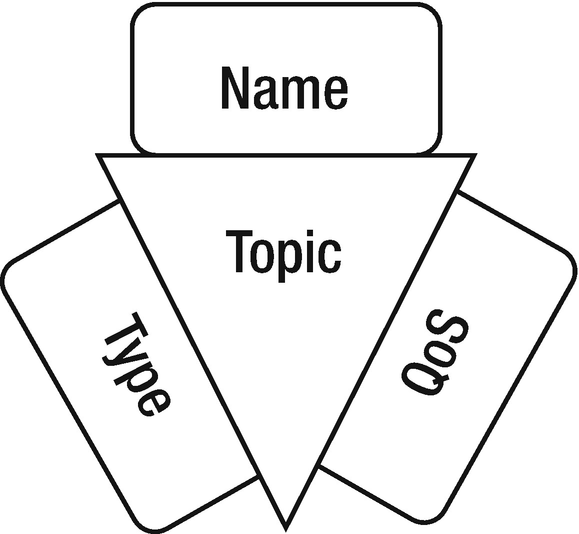
Iot Frameworks And Complexity Springerlink .

Smartthings Architecture Overview Download Scientific Diagram .
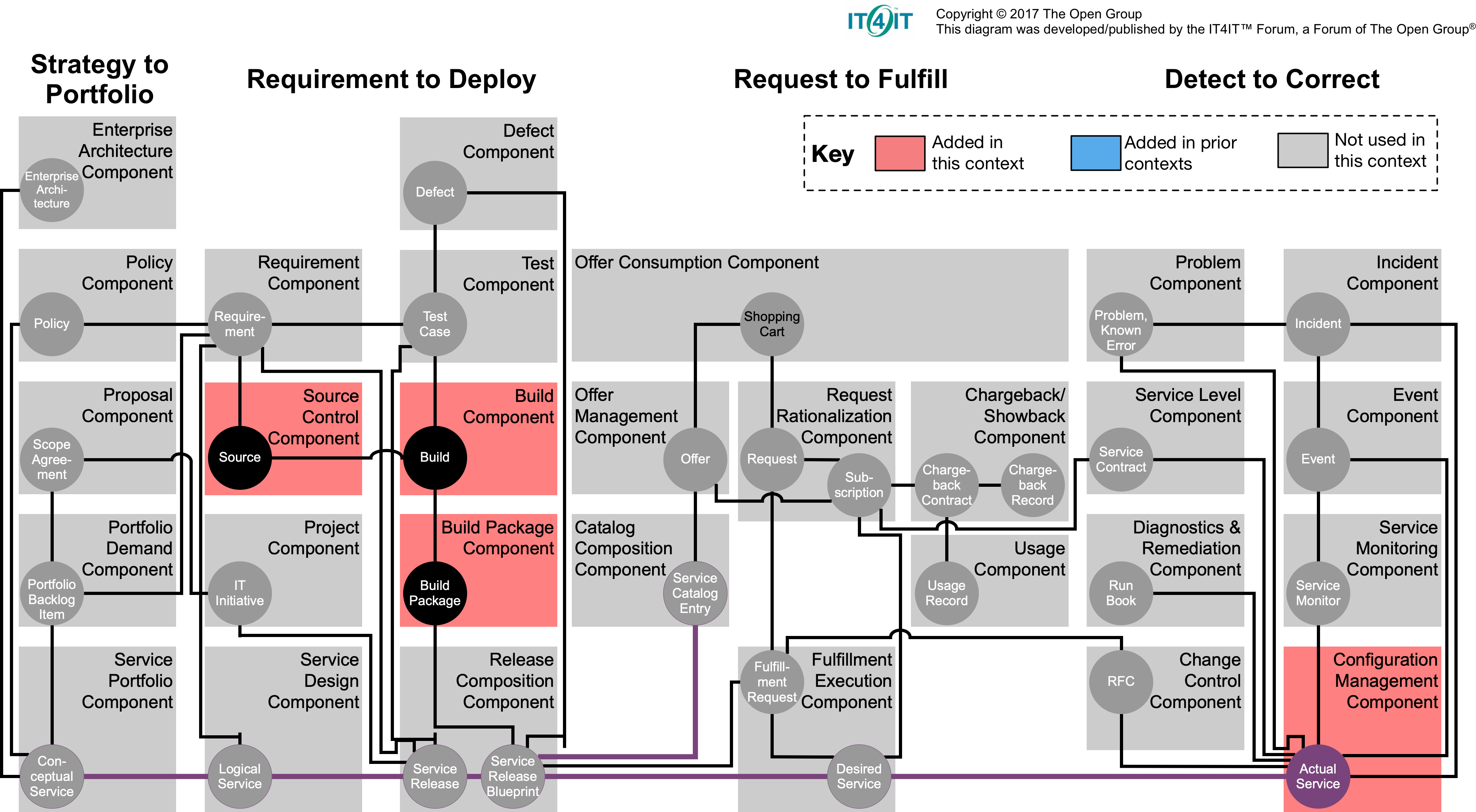
Digital Practitioner Body Of Knowledge Standard .
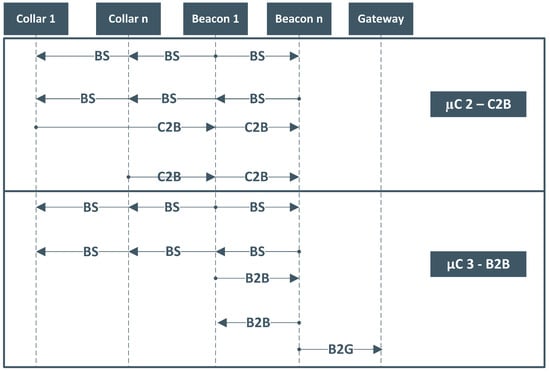
Sensors Special Issue Selected Papers From The 2nd .

Iot A Passion For Research .
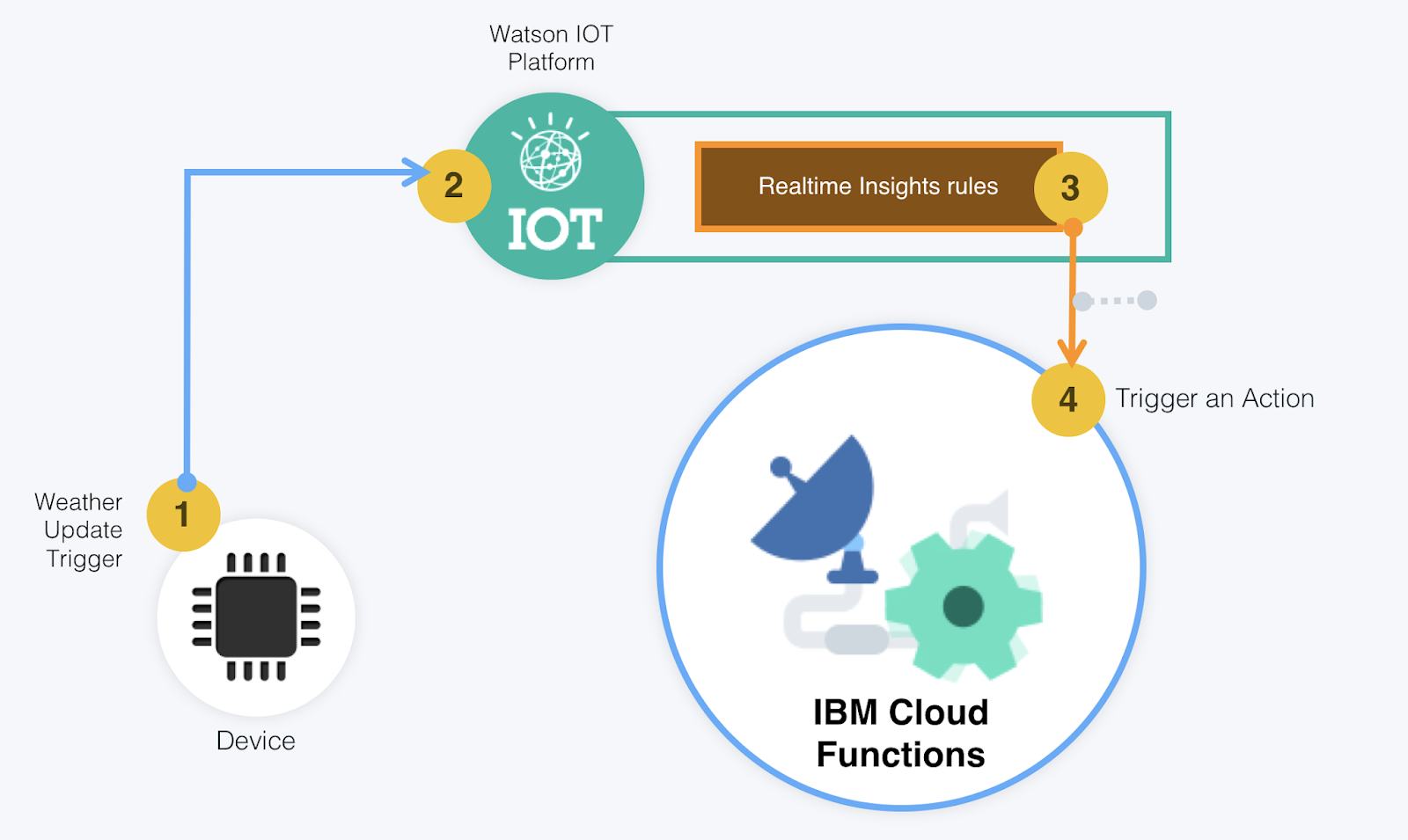
Internet Of Robots Mobile Apps And Enterprises .

Articles Vinnter Ab .

Iot A Passion For Research .

Introducing Industrial Security By Tenable .
Iot Frameworks And Complexity Springerlink .

The Technologies Shaping Your Future Global Technology Radar .

The Environment For Executing Rules In A Simulated Context .

Adopting A Zero Trust Approach 5 Cyber Threats To Expect .

Digital Energy 2018 Day 2 .

Darktrace Technology .
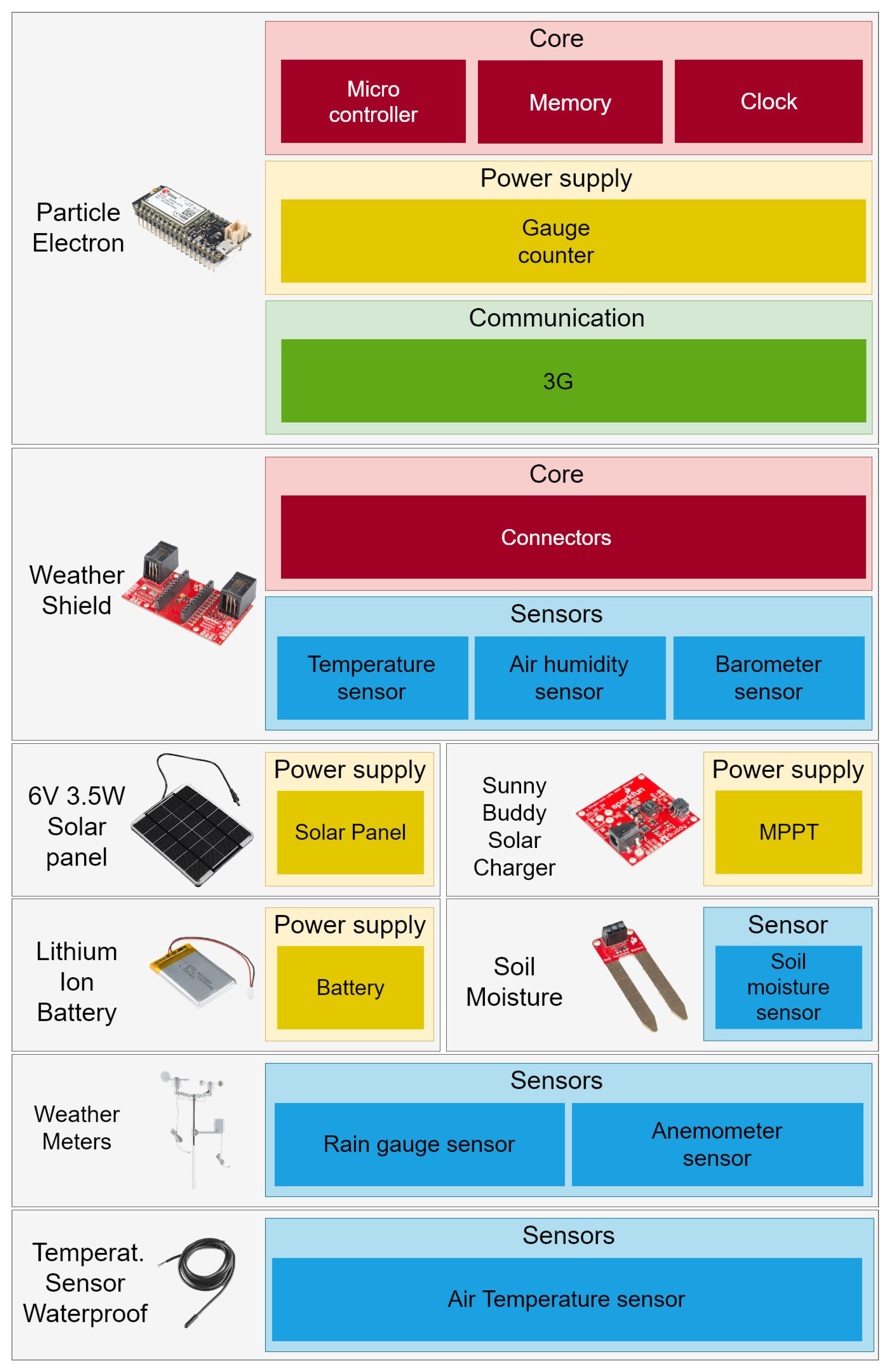
Electronics Free Full Text A Comprehensive Iot Node .
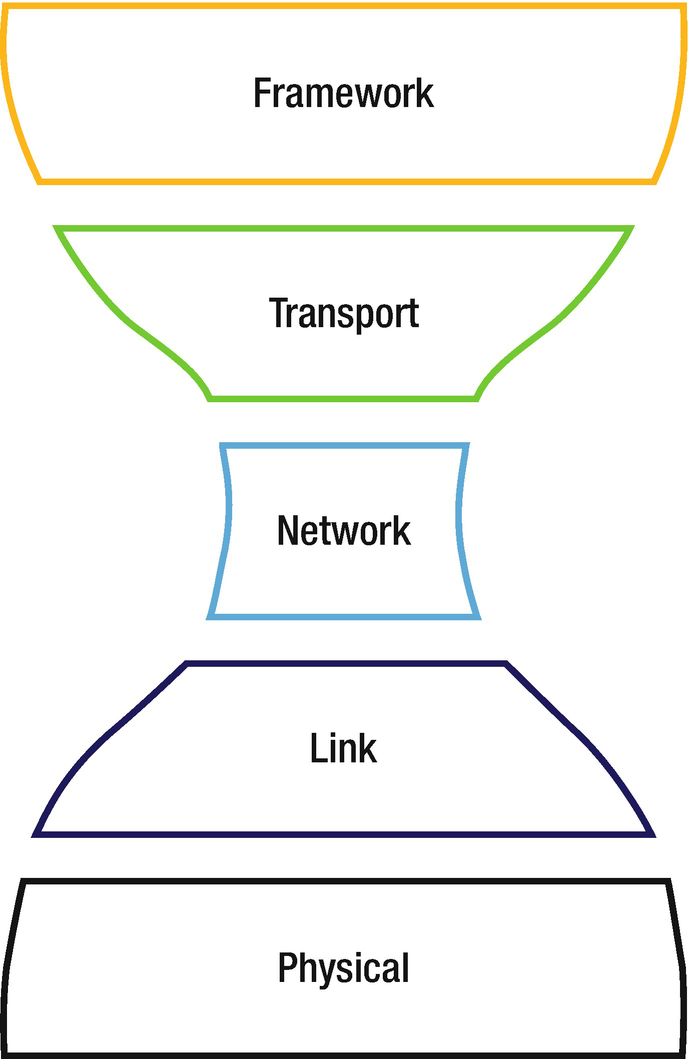
Iot Frameworks And Complexity Springerlink .

Cyrim Scenario Bashe Attack By Cambridge Judge Business .

A Survey On Security Attacks In Vanets Communication .

Iot A Passion For Research .
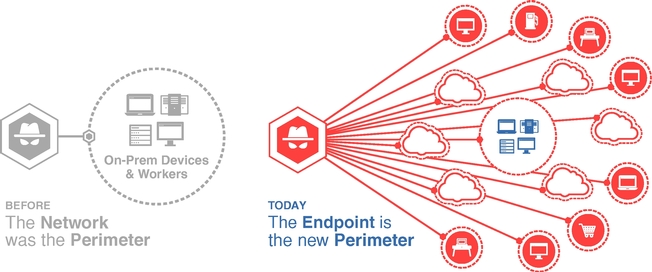
Carbon Black .

Articles Vinnter Ab .
- small animal skull identification chart
- useful charts royal family tree
- hudiburg chevrolet center seating chart
- leaf stock chart
- javascript gantt chart open source
- shalimar game chart 2013
- tial qr bov spring chart
- material density chart in kg m3 pdf
- silver legacy reno grande exposition hall seating chart
- cub cadet belt cross reference chart
- gd&t basics wall chart
- gre scaled score chart
- large wooden ruler height chart
- ionic detox foot bath color chart
- atlanta falcons interactive seating chart
- weight chart frame size
- shimano rc7 size chart
- centurylink field seating chart by row
- ndsu basketball seating chart
- motul recommendation chart india
- fish substitution chart
- 767 seating chart british airways
- mlb hitting spray charts
- cbd vs thc chart
- excel smooth line chart
- pokemon combat chart
- saco river depth charts
- verona arena detailed seating chart
- off the charts music festival
- car light bulb replacement chart