11 Steps To Help Protect Your Business From Cyber Extortion Travelers - Research Methodology Process
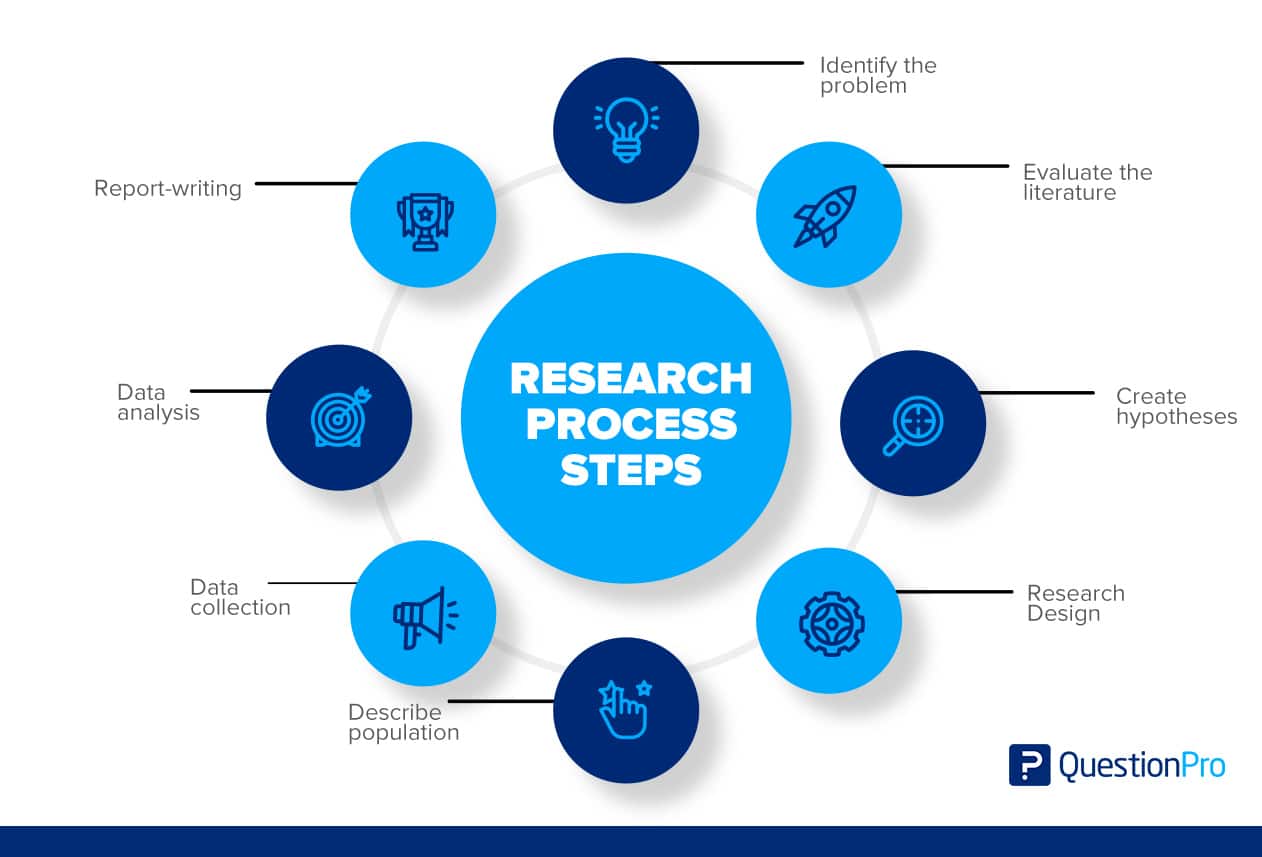
Research Methodology Process

How To Keep Your Employees Safe In The Workplace Healthcare Staffing .

9 Pro Tips To Help Protect Your Business During A Recession Economic .

Steps To Take To Protect Your Business From Ransomware Daisy .

10 Ways To Improve Network Security And Protect Your Business .

How To Protect Your Business Taxassist Accountants Taxassist .

Globe Mybusiness Check Point Help Protect Your Business Across All .

5 Ways You Can Save The Environment From Home Infographic .

Basic Steps To Protect Your Business Against Trojans Yuna Web .
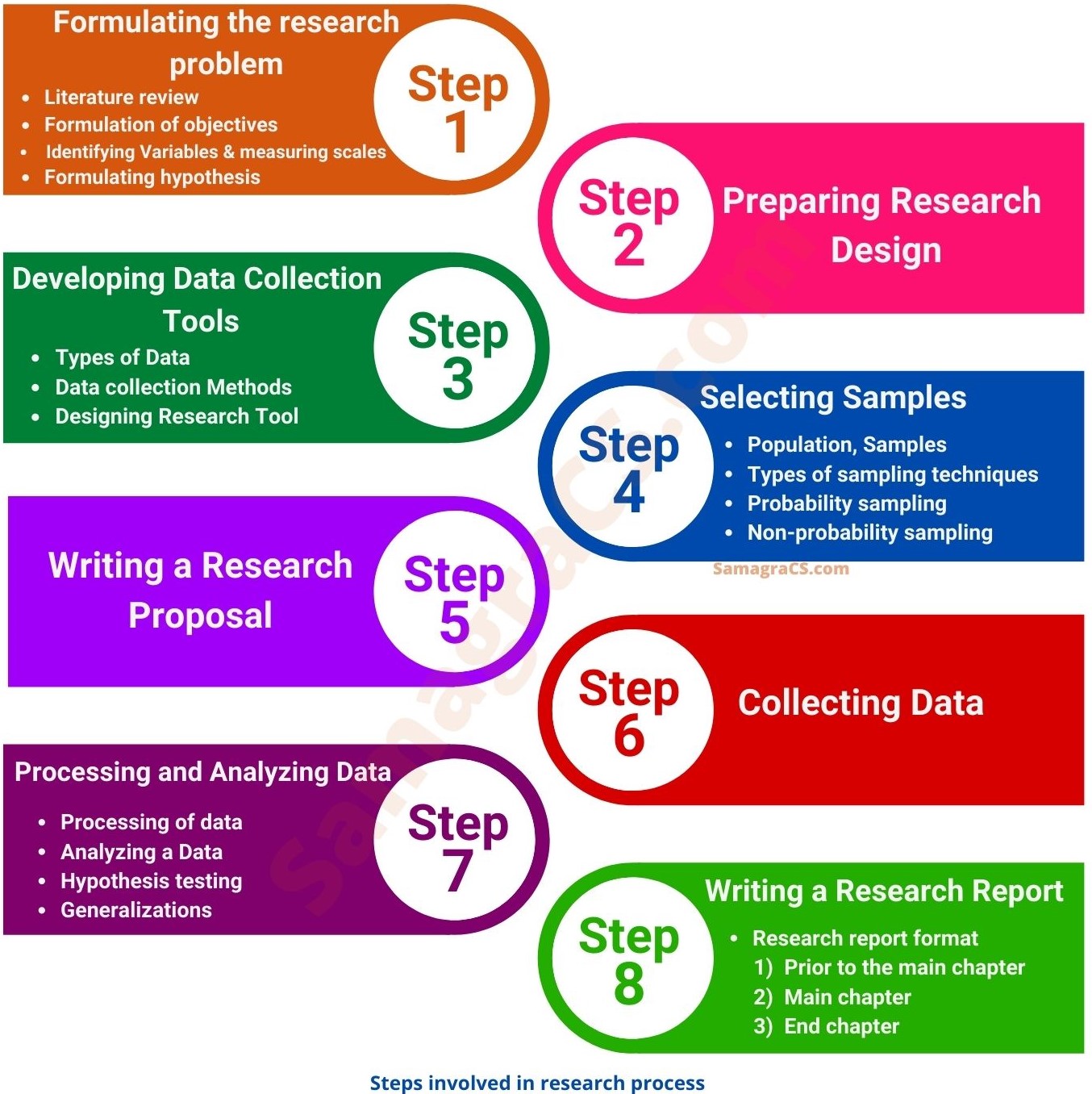
Phases Of Research Design Formulation Design Talk .

10 Steps To Protect Your Business On Social Media .

Protect Your Business With The Best Web Firewall Service In London .
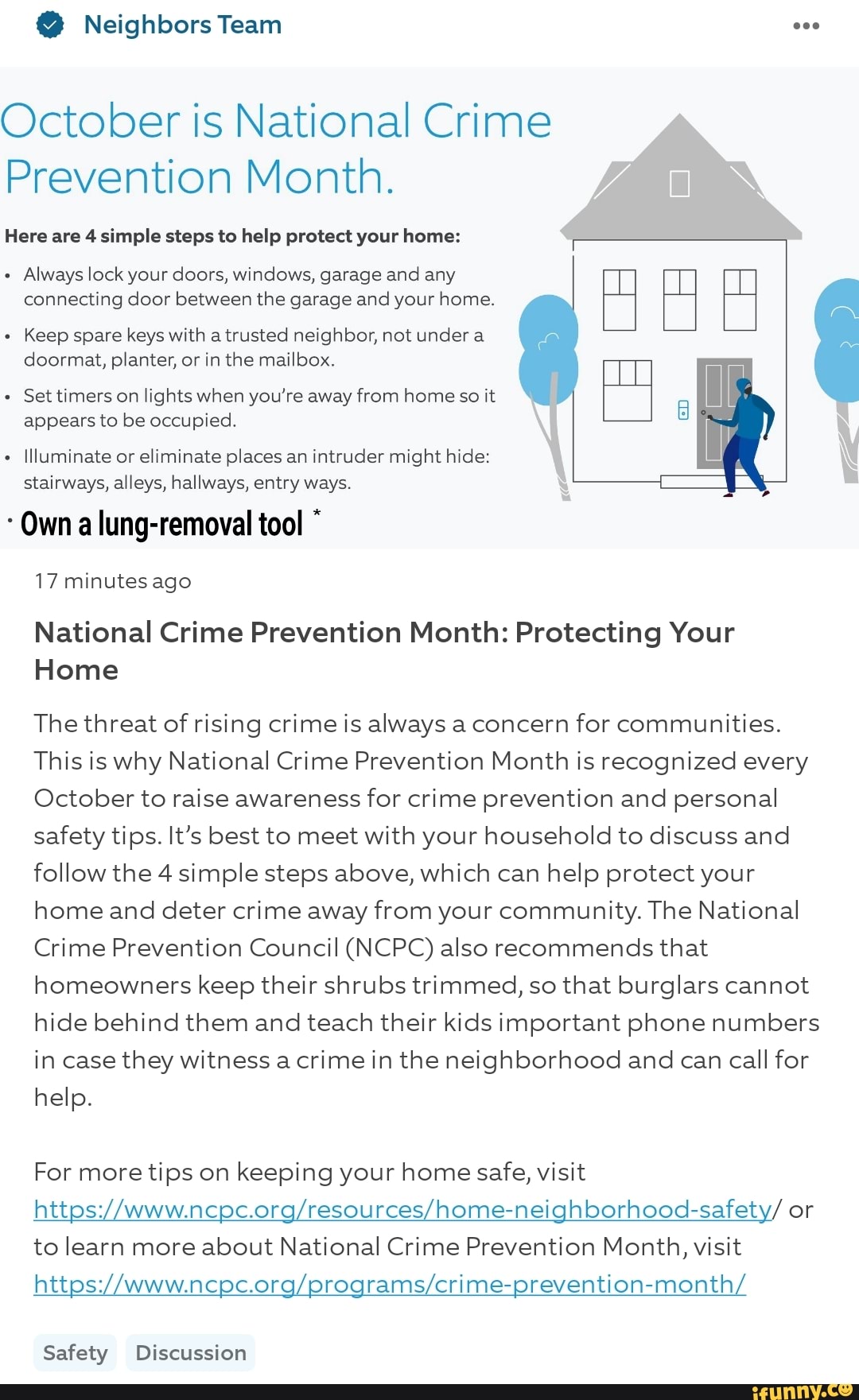
Neighbors Team October Is National Crime Prevention Month Here Are 4 .
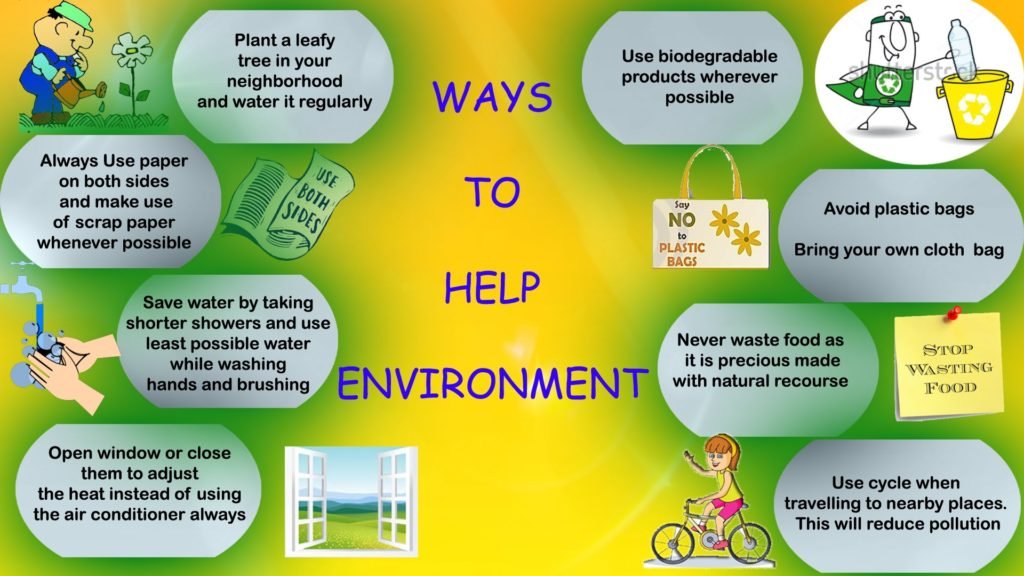
5 Things You Can Do To Help Save The Environment Pahal Welfare Foundation .

Protect Your Business From Physical And Cyber Crime Y Ny Growth Hub .
.png)
Protect Your Business .

How To Protect Your Business Legacy Engage .
Free Stuff To Help You Protect Your Business And Personal Info By .

6 Cybersecurity Threats To Watch In 2023 Myalignedit Com .

5 Common Business Risks And How To Prepare For Them Fam Insurance Inc .

How To Protect Your Business From Social Media Scams Virtual Stacks .

How Key Person Insurance Can Protect Your Business Art Of Retirement .

Premium Vector Environmental Protection Infographic Flat Concept Of .

Dmarc Help Protect Your Brand Against Email Fraud Progist Blogs .

Research Methodology Process .

Aug 31 How To Protect Your Business Avoiding 6 Common Mistakes .

Learn To Protect Your Business From Ecommerce Security Threats Adobe .
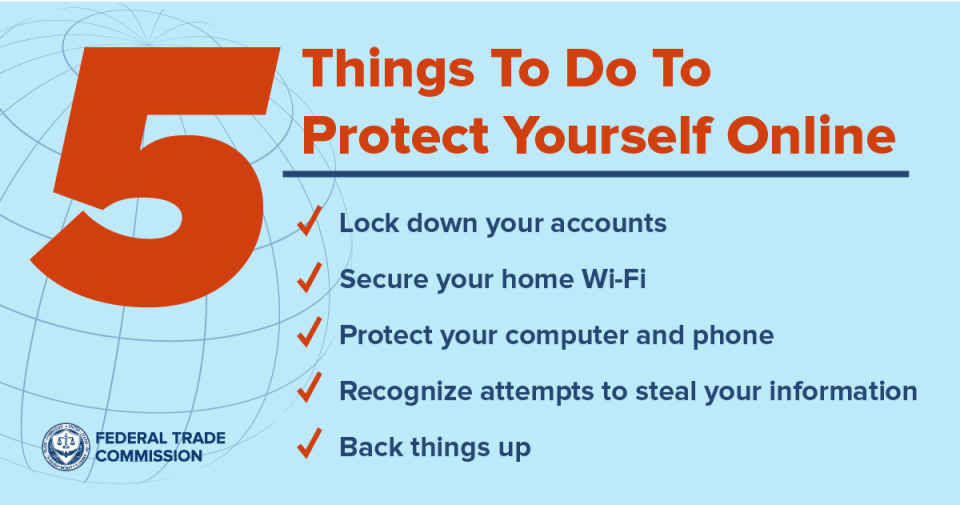
Five Things To Do To Protect Yourself Online Hellotds Blog .

Protect Your Business From Cyber Threats With The 39 Essential Eight .

Protecting Your Employees Through Business Numbers .

What Insurance Does My Business Need Business Insurance .

How Iso 27001 Can Protect Your Business Information .

How To Keep Your Business Protected Exeleon Magazine .
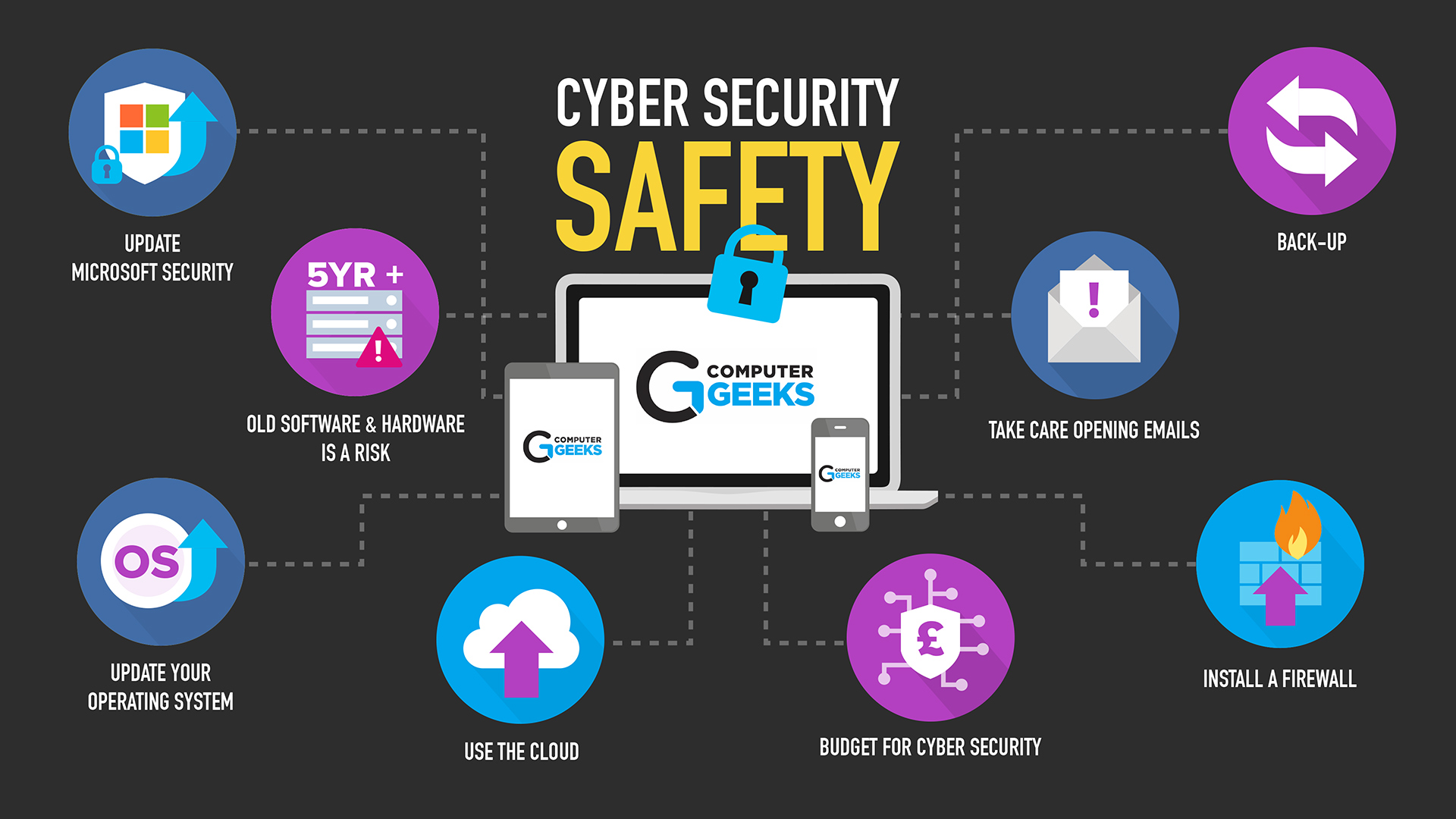
How To Protect Your Business Against Advanced Cyber Threats Klsentral Org .

Cybersecurity Checklist 16 Tips To Protect Your Business In 2023 .
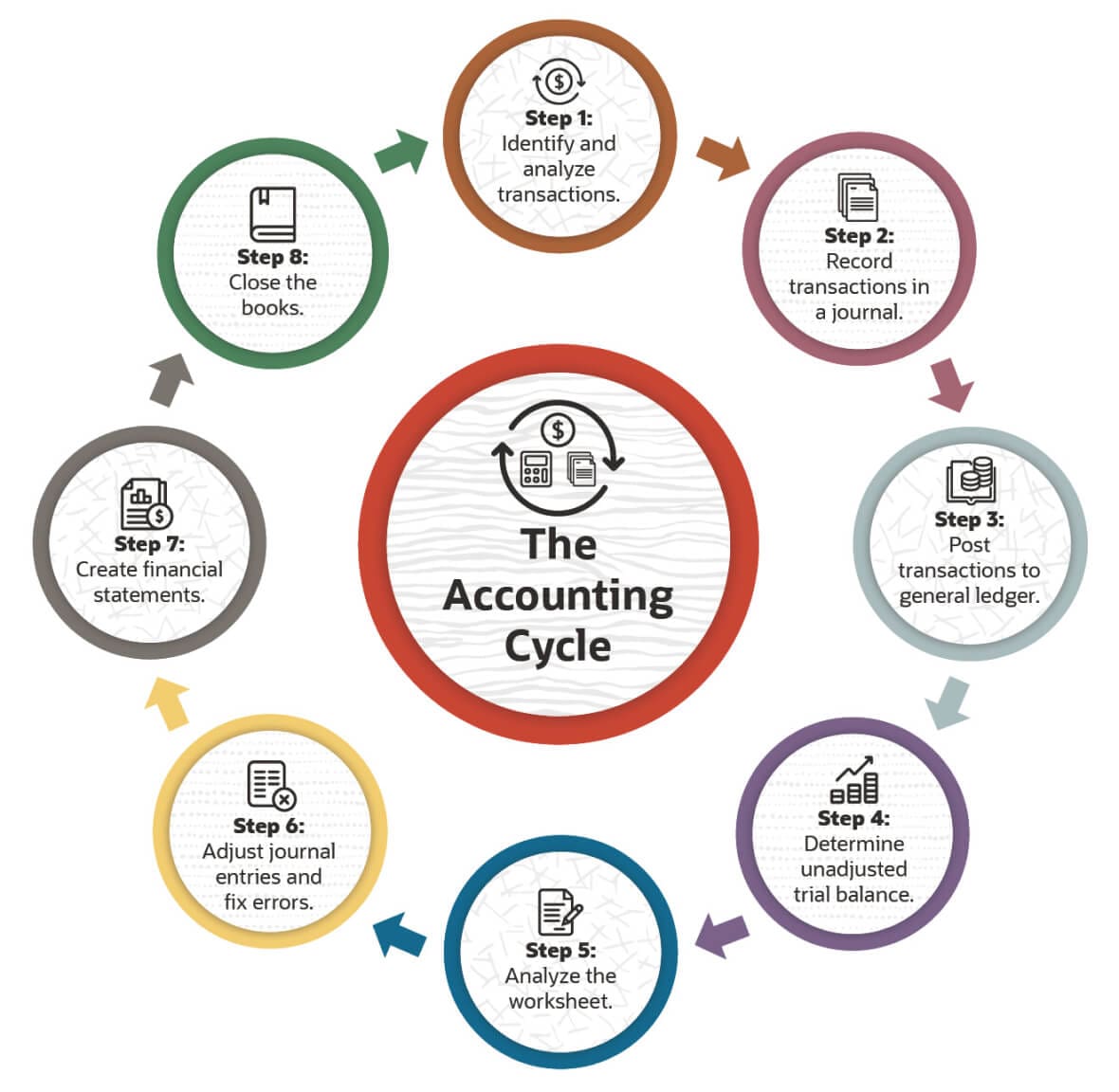
What Is The Accounting Cycle Steps And Definition Netsuite .
Protecting Your Business From Employee Claims On Vimeo .
Acrisure Response On The App Store .

Scott Christensen On Linkedin Are You Properly Prepared For A Cyber .

5 Ways To Protect Your Business During Divorce By Emersonlawfl She .

Tips For Businesses To Navigate Covid 19 Employee Challenges Pardo .

Keith Hall On Linkedin Happy Independence Day .

10 Ways To Save Earth Save Earth Save Planet Earth Save Mother Earth .
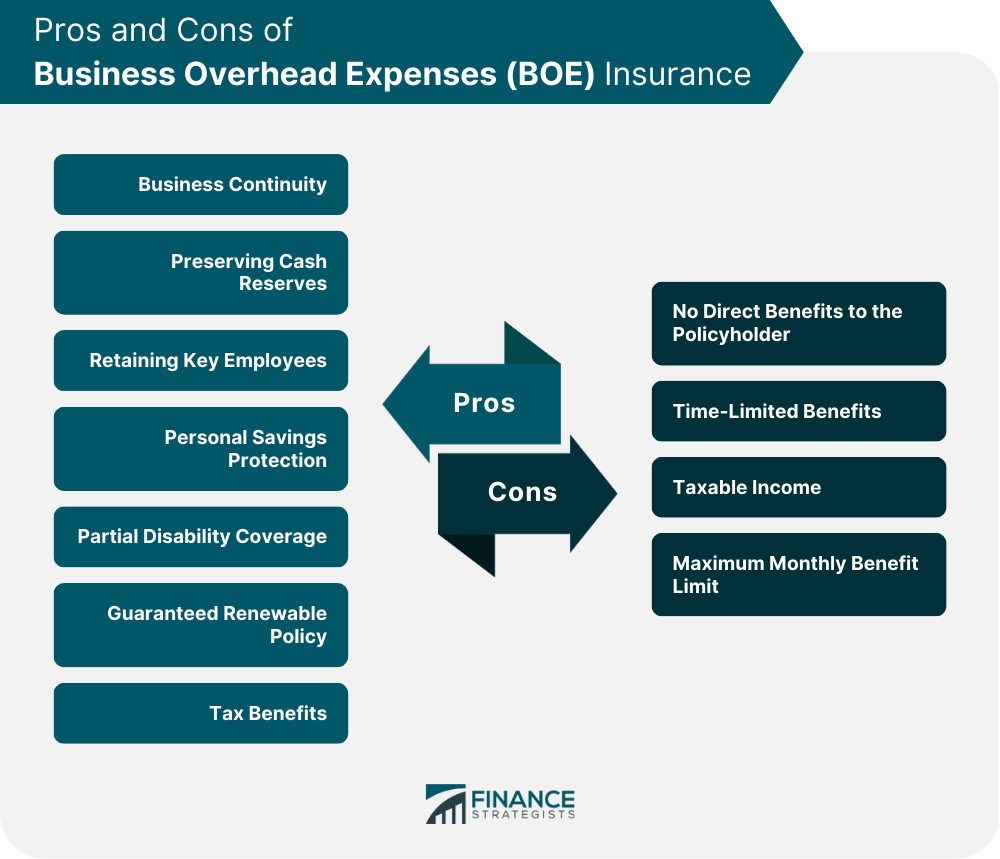
Business Overhead Expense Insurance Definition Pros Cons .

Ways To Protect Your Business Data Webwerks .
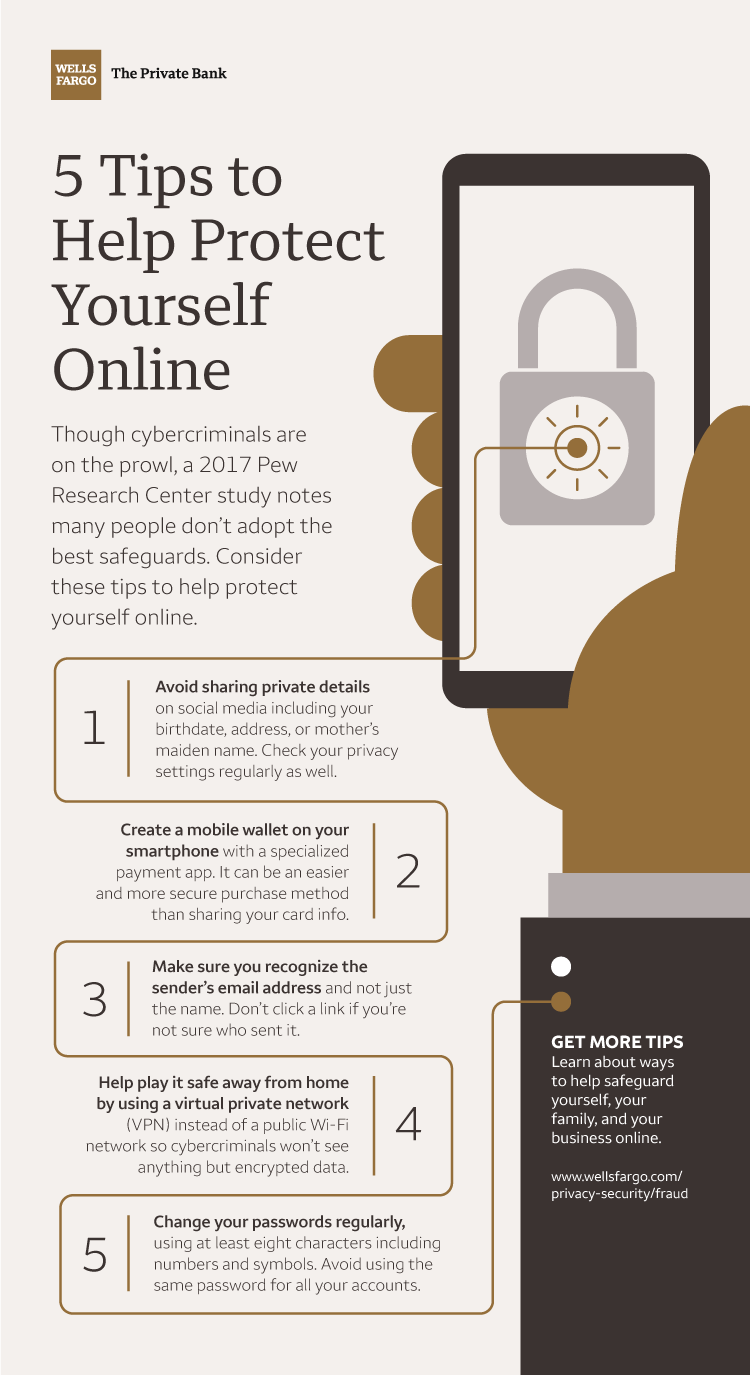
Help Protect Yourself Online With These 5 Tips Wells Fargo Conversations .
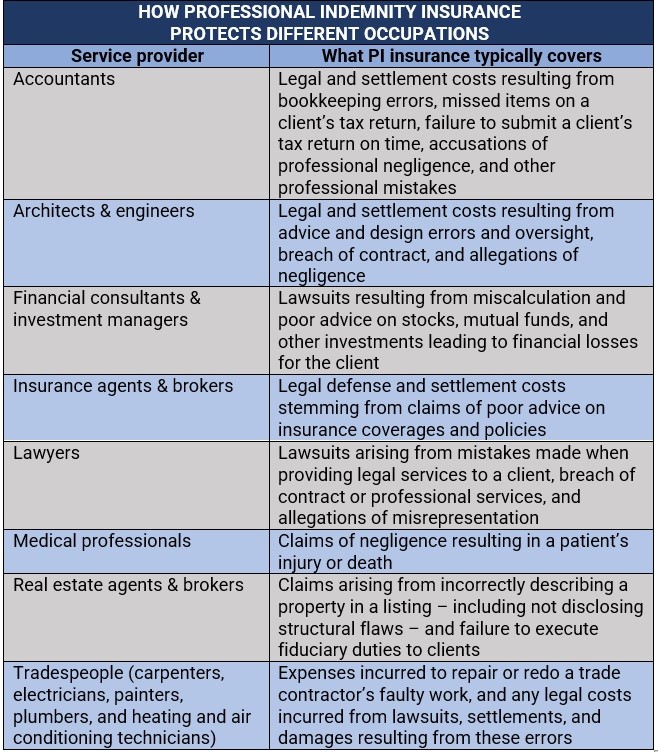
Professional Indemnity Insurance What Is It And How Does It Work .

Pin On Child Protection .
.png)
Who Is Protected By Consumer Protection Laws .

Save The Environment 8 Simplest Ways Students Can Help Save Earth .

Simple Tips To Protect The Planet On Earth Day Water Coolers Direct .
Windows 8 End Of Life Network Migration Service Nerds Support .

Protect Your Business Stock Photo Image Of Care Promote 89988956 .
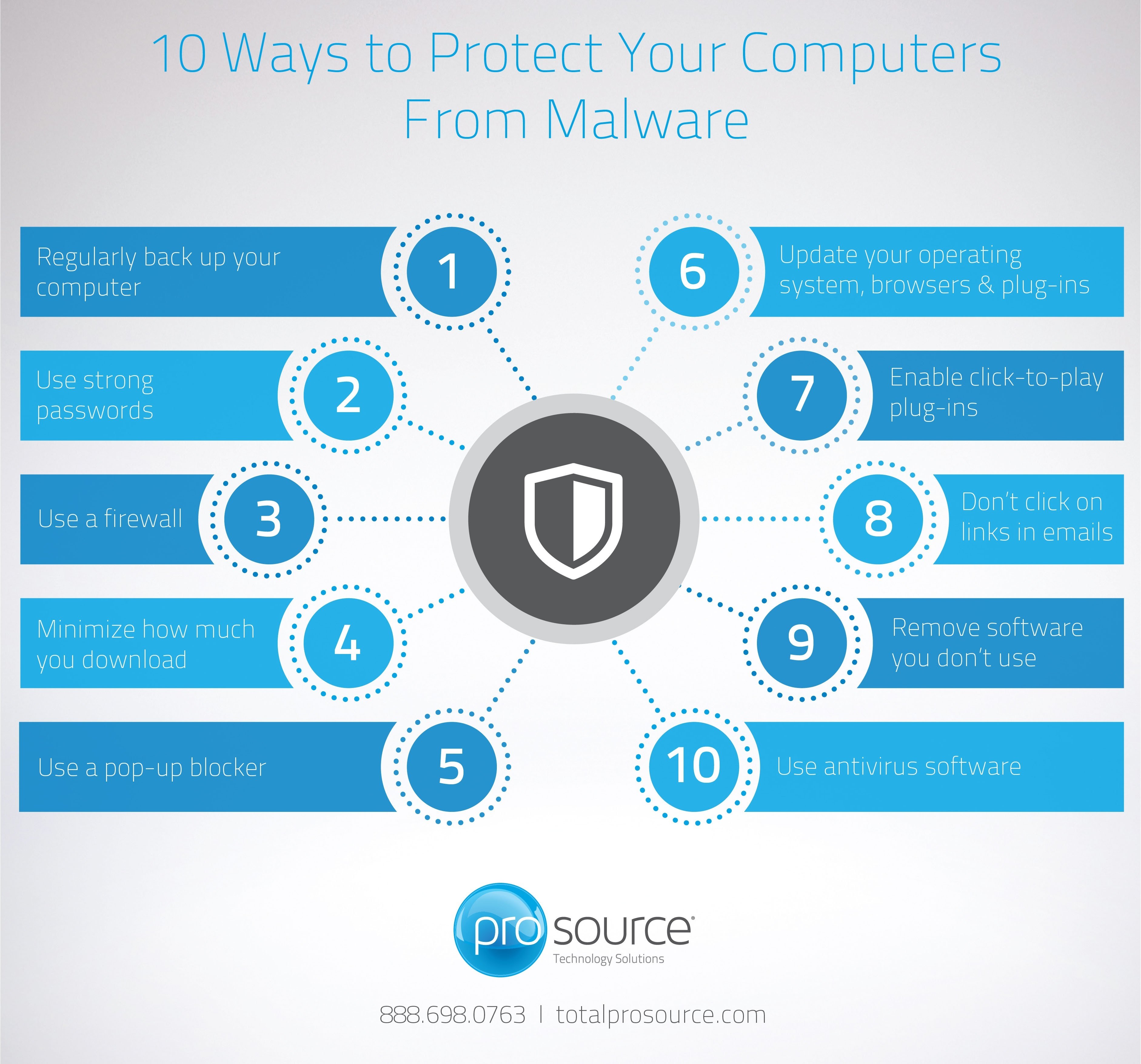
10 Ways To Protect Your Computers From Malware .

How To Keep Oceans Clean Signalsteel19 .

Protect Yourself Online Campaign Against Cybercrime Launched In Australia .

Keep Our Children Safe Rekord East .

Protect Yourself From Identity Theft Lincoln Sda Credit Union .

Coral Reefs Then Now Drsamsblog Com .

Environment Protection .
- army body fat chart
- my chart sentara
- blood chart
- baby shoe size chart
- best stock charting software
- hair color mixing chart
- golf ball compression chart
- dvc point chart 2020
- what is a natal chart
- legacy arena seating chart
- chart house restaurant san antonio
- school chart
- organizational chart maker
- birth control comparison chart
- millimeters to inches chart
- epic charting system
- workers compensation injury chart
- population growth chart
- bulb chart
- vaccination chart for kids
- intermittent fasting chart
- navy federal pay chart
- gauge chart
- a1c levels chart type 2 diabetes
- radar chart
- epic games stock chart
- birth chart analysis
- valley view casino center seating chart
- nissan stadium seating chart
- mgm national harbor seating chart